A shared lock allows multiple transactions to read a resource simultaneously without interfering with each other, ensuring data consistency during concurrent access. It prevents any transaction from modifying the resource while the shared lock is active, maintaining integrity in multi-user environments. Discover how shared locks work and their importance in your database management by reading the full article.
Table of Comparison
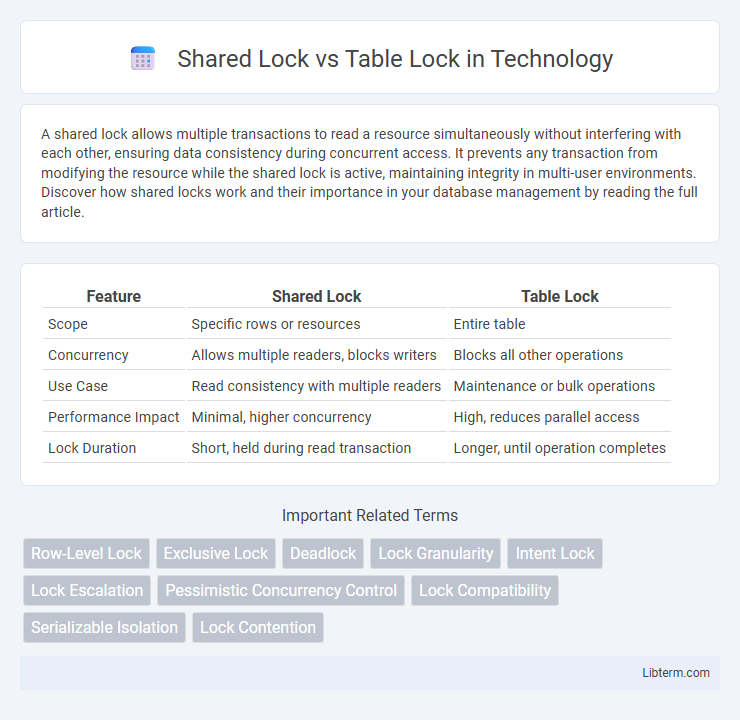
| Feature | Shared Lock | Table Lock |
|---|---|---|
| Scope | Specific rows or resources | Entire table |
| Concurrency | Allows multiple readers, blocks writers | Blocks all other operations |
| Use Case | Read consistency with multiple readers | Maintenance or bulk operations |
| Performance Impact | Minimal, higher concurrency | High, reduces parallel access |
| Lock Duration | Short, held during read transaction | Longer, until operation completes |
Introduction to Database Locking Mechanisms
Shared locks allow multiple transactions to read a database resource concurrently without interference, ensuring data consistency during read operations. Table locks restrict access to an entire table, preventing other transactions from reading or writing until the lock is released, which can improve transaction isolation but reduce concurrency. Understanding these locking mechanisms is essential for optimizing database performance and maintaining data integrity in multi-user environments.
What is a Shared Lock?
A shared lock allows multiple transactions to read a database resource simultaneously while preventing any transaction from modifying it until all shared locks are released. This lock type is essential in maintaining data consistency during concurrent read operations without blocking other readers. Unlike a table lock, which restricts access to an entire table, a shared lock typically targets specific rows or pages, enabling greater concurrency.
What is a Table Lock?
A table lock is a database mechanism that restricts access to an entire table to ensure data integrity during transactions, preventing other operations from modifying the table simultaneously. Unlike a shared lock, which allows multiple transactions to read data concurrently while blocking writes, a table lock can block both read and write operations depending on the lock type (e.g., exclusive or shared). Table locks are commonly used in relational databases like MySQL and PostgreSQL to maintain consistency during bulk updates, schema changes, or maintenance tasks.
Key Differences Between Shared Lock and Table Lock
Shared locks allow multiple transactions to read data simultaneously without interference, ensuring data consistency during concurrent access. Table locks restrict access to the entire table, blocking other transactions from reading or writing until the lock is released, which can reduce concurrency but prevent deadlocks. Key differences include the granularity of locking--shared locks operate at the row or page level while table locks lock the entire table--and the level of concurrency allowed, with shared locks offering higher concurrency compared to table locks.
Use Cases for Shared Locks
Shared locks are primarily used in scenarios requiring concurrent read access while preventing data modifications, such as during complex SELECT queries or report generation in multi-user database environments. They allow multiple transactions to access the data simultaneously without conflict, enhancing system performance and read consistency. Shared locks are ideal for maintaining data integrity during read operations in high-concurrency systems like OLTP databases or data warehousing contexts.
Use Cases for Table Locks
Table locks are used to ensure data consistency and prevent conflicts during bulk operations such as large updates, deletes, or schema changes. They are essential in scenarios where operations must be atomic and isolated at the table level, such as during batch processing or maintenance tasks like indexing. Table locks reduce locking overhead but can lead to decreased concurrency, so they are best suited for situations where transaction speed is less critical than data integrity.
Performance Implications: Shared Lock vs Table Lock
Shared locks enable concurrent read access by multiple transactions without blocking reads, significantly improving performance in high-concurrency environments. Table locks restrict access to the entire table, leading to higher contention and reduced throughput during write operations. Choosing shared locks over table locks optimizes resource utilization and minimizes wait times, enhancing overall database performance.
Impact on Data Concurrency and Consistency
Shared locks allow multiple transactions to read data concurrently without blocking each other, enhancing data concurrency while maintaining consistency by preventing writes during the lock. Table locks restrict access to the entire table, reducing concurrency drastically but ensuring strong consistency by blocking all conflicting operations until the lock is released. Choosing shared locks benefits high-read environments by balancing concurrency and consistency, whereas table locks are suited for operations requiring complete isolation.
Best Practices for Choosing Lock Types
Selecting between shared locks and table locks depends on transaction concurrency and data integrity needs; shared locks allow multiple transactions to read while preventing writes, promoting higher concurrency during read-heavy operations. Table locks, which restrict access to entire tables, are best suited for bulk updates or administrative tasks where locking granularity is less critical. Implementing shared locks for fine-grained control and table locks for complete resource protection optimizes performance and maintains consistency in high-traffic database environments.
Conclusion: Selecting the Right Database Lock
Selecting the right database lock depends on the balance between concurrency needs and data integrity. Shared locks allow multiple transactions to read data simultaneously, enhancing performance in read-heavy environments, while table locks provide stronger protection by restricting access to the entire table, which is beneficial for operations requiring complete data consistency. Understanding workload patterns and locking granularity is critical for optimizing transaction throughput and minimizing deadlocks.
Shared Lock Infographic
 libterm.com
libterm.com