Intrusion detection systems monitor network traffic and system activities to identify unauthorized access or malicious behavior. These technologies use signature-based and anomaly-based methods to detect potential threats early and protect your digital assets. Explore the full article to understand how intrusion detection can enhance your cybersecurity strategy.
Table of Comparison
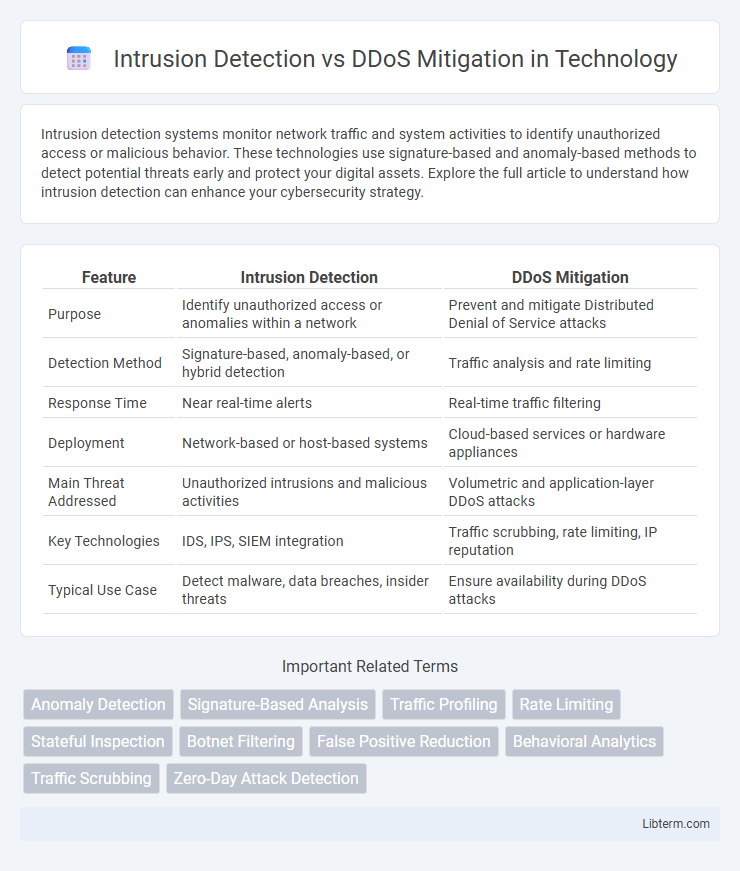
| Feature | Intrusion Detection | DDoS Mitigation |
|---|---|---|
| Purpose | Identify unauthorized access or anomalies within a network | Prevent and mitigate Distributed Denial of Service attacks |
| Detection Method | Signature-based, anomaly-based, or hybrid detection | Traffic analysis and rate limiting |
| Response Time | Near real-time alerts | Real-time traffic filtering |
| Deployment | Network-based or host-based systems | Cloud-based services or hardware appliances |
| Main Threat Addressed | Unauthorized intrusions and malicious activities | Volumetric and application-layer DDoS attacks |
| Key Technologies | IDS, IPS, SIEM integration | Traffic scrubbing, rate limiting, IP reputation |
| Typical Use Case | Detect malware, data breaches, insider threats | Ensure availability during DDoS attacks |
Introduction to Intrusion Detection and DDoS Mitigation
Intrusion detection systems (IDS) monitor network traffic and system activities to identify suspicious behavior, unauthorized access, or potential cyber threats, using signature-based or anomaly-based detection methods. DDoS mitigation involves techniques and tools designed to detect and mitigate Distributed Denial of Service attacks, which overwhelm targeted servers or networks with excessive traffic to disrupt services. Both play critical roles in cybersecurity, with IDS focusing on identifying attacks and DDoS mitigation aimed at maintaining service availability during volumetric attacks.
Defining Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) monitor network traffic to identify suspicious activities and potential security breaches in real-time, using signature-based or anomaly-based detection methods. IDS play a critical role in distinguishing between benign traffic and malicious attempts such as unauthorized access or malicious payload delivery. Unlike DDoS mitigation, which focuses on traffic volume control and attack prevention, IDS prioritize threat detection and alert generation to enable timely incident response.
Understanding DDoS Attacks and Their Impact
DDoS attacks overwhelm networks or servers with massive traffic, aiming to disrupt normal service availability and cause significant operational downtime. Intrusion detection systems identify suspicious patterns and anomalies in network traffic that may indicate the onset of a DDoS attack, enabling early warning and response. Effective DDoS mitigation involves traffic filtering, rate limiting, and leveraging cloud-based scrubbing to maintain service performance and protect critical infrastructure from downtime and financial loss.
How Intrusion Detection Systems Work
Intrusion Detection Systems (IDS) monitor network traffic and use signature-based or anomaly-based techniques to identify malicious activities, such as unauthorized access or policy violations. These systems analyze patterns in data packets, alerting administrators to potential threats in real-time without actively blocking traffic. IDS play a critical role in identifying early signs of Distributed Denial of Service (DDoS) attacks by detecting unusual traffic spikes or suspicious packet behavior.
Key Techniques in DDoS Mitigation
DDoS mitigation employs key techniques such as traffic filtering, rate limiting, and behavior analysis to identify and block malicious traffic while allowing legitimate users access. Traffic diversion through scrubbing centers redirects suspicious data to specialized systems that clean harmful packets before they reach the target network. Combined use of anomaly detection and real-time monitoring enhances detection accuracy and response speed against diverse Distributed Denial of Service attack vectors.
Major Differences Between IDS and DDoS Mitigation
Intrusion Detection Systems (IDS) primarily focus on monitoring network traffic to identify suspicious activities and potential security breaches, whereas DDoS mitigation specifically targets the prevention and filtering of Distributed Denial of Service attacks designed to overwhelm network resources. IDS analyzes patterns and signatures to detect unauthorized access attempts, while DDoS mitigation employs traffic filtering, rate limiting, and traffic redirection to ensure service availability during attack events. The core difference lies in IDS's role in threat detection and alerting, contrasted with DDoS mitigation's active defense and traffic management to maintain operational continuity.
Deployment Scenarios for IDS and DDoS Solutions
Intrusion Detection Systems (IDS) are typically deployed across network segments to monitor traffic for anomalous or malicious activity, often placed at key points such as network perimeters, internal network segments, and cloud environments to ensure comprehensive threat detection. DDoS mitigation solutions are commonly implemented at the network edge or within cloud-based scrubbing centers to absorb and filter large volumes of attack traffic before it reaches critical infrastructure, ensuring service availability. Both IDS and DDoS mitigation systems complement each other by providing layered security: IDS focuses on detecting unauthorized access or behavior, while DDoS solutions prevent service disruption from volumetric attacks.
Challenges in Detecting and Preventing DDoS Attacks
Detecting and preventing DDoS attacks presents significant challenges due to the high volume and distribution of malicious traffic, which often mimics legitimate user behavior, making it difficult for traditional Intrusion Detection Systems (IDS) to differentiate between normal and attack patterns. The scalability of DDoS attacks, leveraging thousands of compromised devices across diverse networks, complicates real-time analysis and response, demanding advanced threat intelligence and behavioral analytics. Effective DDoS mitigation requires integrating multi-layered defense mechanisms, including traffic filtering, rate limiting, and automated response systems, to minimize downtime and maintain service availability.
Integrating IDS with DDoS Mitigation Strategies
Integrating Intrusion Detection Systems (IDS) with DDoS mitigation strategies enhances network security by enabling real-time identification and response to malicious traffic patterns. IDS monitors network packets for signs of intrusion, while DDoS mitigation systems analyze traffic volume and behavior to filter out distributed denial-of-service attacks effectively. Combining these technologies leverages threat intelligence and automated filtering, reducing downtime and improving resilience against complex, multi-vector DDoS attacks.
Best Practices for Comprehensive Network Security
Intrusion detection systems (IDS) monitor network traffic for suspicious activity, enabling early identification of potential cyber threats, while DDoS mitigation involves specialized techniques to prevent denial-of-service attacks from overwhelming network resources. Best practices for comprehensive network security integrate IDS with real-time threat intelligence and automated response mechanisms to detect and isolate intrusions promptly, alongside scalable DDoS mitigation solutions such as traffic filtering, rate limiting, and cloud-based scrubbing services. Maintaining updated signatures, continuous monitoring, and coordinated incident response ensures robust defense against both intrusion attempts and volumetric attack vectors.
Intrusion Detection Infographic
 libterm.com
libterm.com