Strong passwords protect your online accounts by making it difficult for hackers to gain unauthorized access. Using a combination of letters, numbers, and special characters enhances security and reduces the risk of identity theft. Explore the article to discover effective strategies for creating and managing your passwords safely.
Table of Comparison
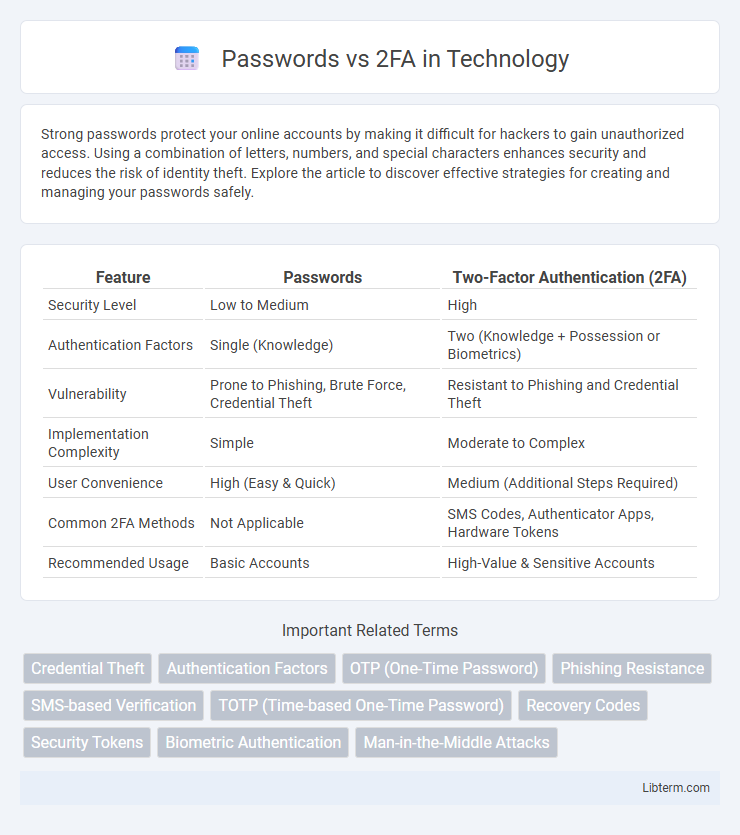
| Feature | Passwords | Two-Factor Authentication (2FA) |
|---|---|---|
| Security Level | Low to Medium | High |
| Authentication Factors | Single (Knowledge) | Two (Knowledge + Possession or Biometrics) |
| Vulnerability | Prone to Phishing, Brute Force, Credential Theft | Resistant to Phishing and Credential Theft |
| Implementation Complexity | Simple | Moderate to Complex |
| User Convenience | High (Easy & Quick) | Medium (Additional Steps Required) |
| Common 2FA Methods | Not Applicable | SMS Codes, Authenticator Apps, Hardware Tokens |
| Recommended Usage | Basic Accounts | High-Value & Sensitive Accounts |
Understanding Passwords: The Basics
Passwords serve as the primary authentication method by requiring a secret combination of characters known only to the user, functioning as the first line of defense against unauthorized access. However, passwords are vulnerable to threats such as phishing, brute force attacks, and credential stuffing, making them insufficient when used alone. Understanding the basics of passwords involves creating strong, unique combinations that include uppercase letters, numbers, and special characters to enhance security.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) enhances security by requiring users to provide two different types of identification before accessing an account: something they know (like a password) and something they have (such as a smartphone or hardware token). This extra layer of protection significantly reduces the risk of unauthorized access caused by stolen or weak passwords. Common 2FA methods include SMS codes, authenticator apps, and biometric verification, ensuring a robust defense against cyber threats.
Comparing Security Levels: Passwords vs 2FA
Passwords alone offer basic protection but are vulnerable to phishing, brute force attacks, and credential leaks. Two-factor authentication (2FA) significantly enhances security by requiring an additional verification step, such as a one-time code or biometric check, reducing the risk of unauthorized access. Implementing 2FA can block over 99.9% of account compromise attempts, making it substantially more secure than relying on passwords alone.
Common Vulnerabilities of Password-Only Systems
Password-only systems are highly vulnerable to attacks such as phishing, brute force, and credential stuffing, often resulting from weak or reused passwords. These systems lack protection against unauthorized access when passwords are compromised through data breaches or social engineering. Implementing Two-Factor Authentication (2FA) enhances security by requiring an additional verification step, significantly reducing the risk of unauthorized account access.
How 2FA Mitigates Password Risks
Two-factor authentication (2FA) significantly mitigates password risks by requiring an additional verification step, such as a one-time code or biometric confirmation, that hackers cannot easily replicate even if passwords are compromised. This extra layer of security protects user accounts from common threats like phishing, credential stuffing, and brute-force attacks. By combining something the user knows (password) with something the user has or is (token, smartphone, or fingerprint), 2FA effectively reduces unauthorized access and enhances overall cybersecurity.
User Experience: Ease of Use and Accessibility
Passwords provide straightforward access but often suffer from weak security due to reuse and complexity requirements, impacting user experience negatively. Two-factor authentication (2FA) enhances security by requiring a second verification method, which can introduce additional steps but is increasingly streamlined through biometric and push-notification methods. Accessibility varies as 2FA may pose challenges for users without smartphones or with disabilities, making inclusive design and alternative options critical for user adoption.
Implementing Passwords and 2FA Together
Implementing passwords alongside two-factor authentication (2FA) significantly enhances account security by requiring both something the user knows (password) and something they have or are (2FA method), such as a mobile authenticator or biometric scan. This layered security approach reduces the risk of unauthorized access due to stolen or weak passwords, effectively mitigating phishing attacks and credential reuse vulnerabilities. Combining strong, unique passwords with 2FA protocols like TOTP (Time-based One-Time Password) or U2F (Universal 2nd Factor) tokens optimizes protection against evolving cyber threats.
Real-World Examples of Security Breaches
High-profile security breaches at companies like Yahoo and LinkedIn highlight the weaknesses of relying solely on passwords, where billions of user credentials were exposed due to poor password hygiene and lack of additional authentication layers. In contrast, organizations implementing two-factor authentication (2FA), such as Google and Microsoft, have drastically reduced unauthorized account access even when passwords were compromised. Real-world data shows 2FA can block over 99.9% of account takeover attempts, emphasizing its critical role in strengthening digital security beyond traditional passwords.
Best Practices for Strong Authentication
Strong authentication relies on combining passwords with two-factor authentication (2FA) to significantly enhance security by requiring both something you know and something you have. Passwords should be complex, unique, and regularly updated, using passphrases or a combination of letters, numbers, and symbols to resist brute force and dictionary attacks. Implementing 2FA methods like authenticator apps, hardware tokens, or biometric verification provides an additional layer of protection against phishing, credential theft, and unauthorized access.
The Future of Digital Security: Beyond Passwords and 2FA
The future of digital security is shifting toward passwordless authentication methods that leverage biometrics, behavioral analysis, and hardware tokens to enhance protection beyond traditional passwords and two-factor authentication (2FA). Innovations such as decentralized identity frameworks and zero-trust architectures reduce reliance on static credentials by continuously verifying user identity in real-time. These advancements aim to address evolving cyber threats by combining stronger security with seamless user experience, ultimately transforming digital access control.
Passwords Infographic
 libterm.com
libterm.com