Authorization ensures that only individuals with the appropriate permissions can access specific resources or perform designated actions, enhancing security and compliance. It works by verifying credentials and enforcing access control policies tailored to your needs. Explore the rest of the article to understand how effective authorization processes protect your data and optimize system integrity.
Table of Comparison
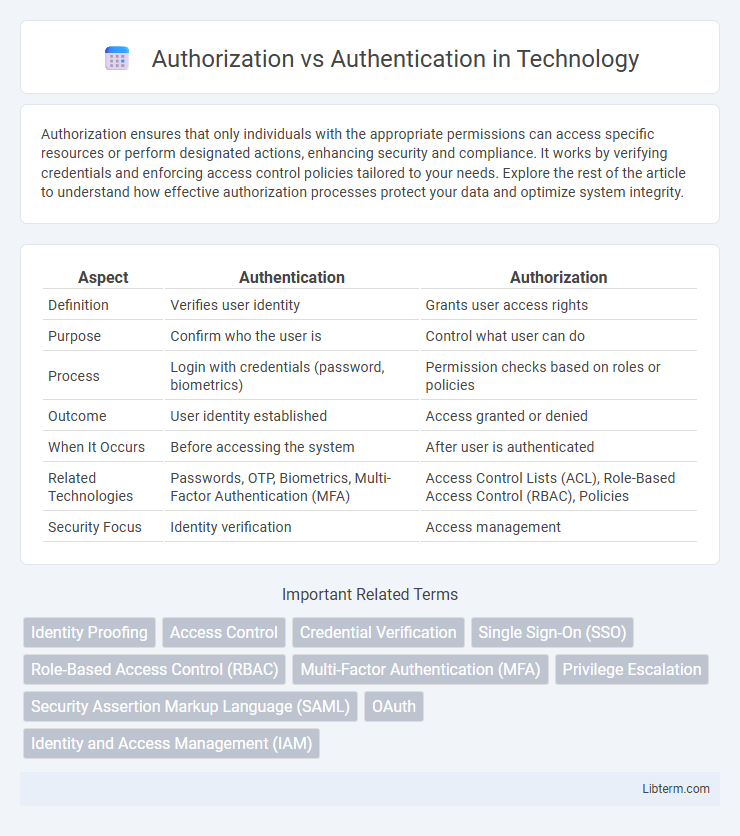
| Aspect | Authentication | Authorization |
|---|---|---|
| Definition | Verifies user identity | Grants user access rights |
| Purpose | Confirm who the user is | Control what user can do |
| Process | Login with credentials (password, biometrics) | Permission checks based on roles or policies |
| Outcome | User identity established | Access granted or denied |
| When It Occurs | Before accessing the system | After user is authenticated |
| Related Technologies | Passwords, OTP, Biometrics, Multi-Factor Authentication (MFA) | Access Control Lists (ACL), Role-Based Access Control (RBAC), Policies |
| Security Focus | Identity verification | Access management |
Introduction to Authorization and Authentication
Authentication verifies the identity of a user or system by validating credentials such as passwords, biometrics, or tokens. Authorization determines the access levels and permissions granted to the authenticated user, controlling what resources or actions they can perform. Effective security frameworks rely on both authentication and authorization to protect sensitive data and ensure proper access control.
Defining Authentication
Authentication verifies the identity of a user or system by requiring credentials such as passwords, biometrics, or security tokens. This process ensures that only legitimate users gain access to systems or data, forming the first line of defense in cybersecurity. Authentication protocols include multi-factor authentication (MFA), single sign-on (SSO), and biometric verification, enhancing security by confirming user identity before authorization grants permissions.
Defining Authorization
Authorization determines user permissions by defining access levels to resources and actions within a system. It enforces security policies by granting or denying rights based on roles, credentials, and predefined privileges. Effective authorization ensures users interact only with permitted data, maintaining system integrity and confidentiality.
Key Differences Between Authorization and Authentication
Authentication verifies a user's identity by confirming credentials such as passwords, biometrics, or tokens, while authorization determines the access level and permissions granted to that authenticated user within a system. Authentication occurs before authorization and is essential to establishing a secure user identity, whereas authorization controls resource access based on policies and roles. Key differences include the purpose--authentication confirms who you are, authorization defines what you can do--and the process flow, where authentication precedes authorization in security frameworks.
How Authentication Works
Authentication verifies the identity of a user or system by requiring credentials such as passwords, biometrics, or security tokens. It typically involves processes like multi-factor authentication (MFA), where two or more verification methods are combined to enhance security. Authentication protocols such as OAuth, SAML, and OpenID Connect facilitate secure validation by exchanging tokens and assertions between users and service providers.
How Authorization Works
Authorization works by defining and enforcing access control policies that determine user permissions for resources or actions within a system. It relies on verifying user roles, privileges, and security tokens after identity has been authenticated, typically using methods like role-based access control (RBAC) or attribute-based access control (ABAC). This process ensures users gain only the necessary access levels to protect sensitive data and system integrity.
Importance in Cybersecurity
Authentication verifies the identity of users or systems by validating credentials such as passwords, biometrics, or tokens, forming the first line of defense in cybersecurity. Authorization determines the access rights and privileges assigned to authenticated entities, ensuring that users can only access resources they are permitted to use, which minimizes the risk of data breaches. Together, robust authentication and precise authorization are crucial for preventing unauthorized access, protecting sensitive data, and maintaining regulatory compliance in cybersecurity frameworks.
Common Authentication Methods
Common authentication methods include passwords, biometrics, multi-factor authentication (MFA), and token-based systems. These methods verify a user's identity by requiring credentials such as something they know (password), something they have (security token), or something they are (fingerprint or facial recognition). Authentication establishes identity before authorization grants access to specific resources or actions in a system.
Types of Authorization Mechanisms
Authorization mechanisms control user access to resources based on permissions, with common types including Role-Based Access Control (RBAC), which assigns access rights according to user roles, and Attribute-Based Access Control (ABAC), which uses policies based on user attributes, resource attributes, and environment conditions. Discretionary Access Control (DAC) allows owners to set access policies for their resources, while Mandatory Access Control (MAC) enforces system-wide policies typically used in high-security environments. OAuth and OpenID Connect provide modern, token-based authorization frameworks for secure delegated access across web applications and APIs.
Best Practices for Implementing Both
Implement robust multi-factor authentication (MFA) to enhance security by verifying user identities through multiple credentials before access is granted. Implement role-based access control (RBAC) to ensure users only have permissions necessary for their job functions, reducing the risk of unauthorized data exposure. Regularly audit and review authorization policies and authentication logs to detect anomalies and maintain compliance with security standards such as ISO 27001 and NIST.
Authorization Infographic
 libterm.com
libterm.com