Tokenization is the process of breaking down text into smaller units such as words, phrases, or symbols, which are essential for natural language processing tasks. This step allows your algorithms to understand and analyze the structure and meaning of language more effectively. Explore the rest of the article to learn how tokenization impacts various applications in AI and machine learning.
Table of Comparison
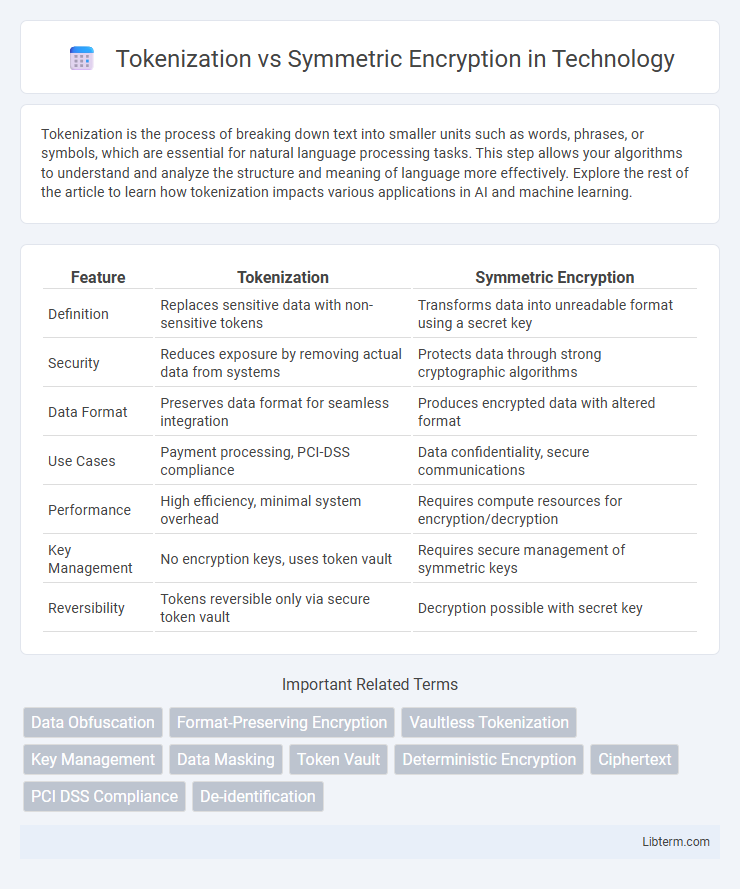
| Feature | Tokenization | Symmetric Encryption |
|---|---|---|
| Definition | Replaces sensitive data with non-sensitive tokens | Transforms data into unreadable format using a secret key |
| Security | Reduces exposure by removing actual data from systems | Protects data through strong cryptographic algorithms |
| Data Format | Preserves data format for seamless integration | Produces encrypted data with altered format |
| Use Cases | Payment processing, PCI-DSS compliance | Data confidentiality, secure communications |
| Performance | High efficiency, minimal system overhead | Requires compute resources for encryption/decryption |
| Key Management | No encryption keys, uses token vault | Requires secure management of symmetric keys |
| Reversibility | Tokens reversible only via secure token vault | Decryption possible with secret key |
Introduction to Data Protection Techniques
Tokenization replaces sensitive data with non-sensitive placeholders, minimizing exposure risk by storing actual data separately, while symmetric encryption transforms data into an unreadable format using a shared secret key for both encryption and decryption. Tokenization is widely used in payment processing to reduce PCI DSS scope, whereas symmetric encryption is essential for securing data in transit and at rest across various applications and industries. Both techniques are fundamental in modern data protection strategies, complementing each other to enhance overall information security.
What is Tokenization?
Tokenization is a data security process that replaces sensitive information with unique identification symbols called tokens, which have no intrinsic value or meaning outside the system. Unlike symmetric encryption, tokenization does not use a mathematical algorithm to transform data but instead maps the original data to a non-sensitive equivalent stored in a secure token vault. This method minimizes exposure to sensitive data, reducing the risk of data breaches by ensuring that tokens cannot be reverse-engineered to reveal the original content.
What is Symmetric Encryption?
Symmetric encryption is a cryptographic technique where the same key is used for both encryption and decryption of data, ensuring confidentiality by transforming plaintext into ciphertext. It relies on secret key algorithms such as AES (Advanced Encryption Standard) to protect sensitive information from unauthorized access. Unlike tokenization, symmetric encryption secures data by mathematically altering it, making the original data retrievable only with the secret key.
Key Differences Between Tokenization and Symmetric Encryption
Tokenization replaces sensitive data with non-sensitive placeholders called tokens, eliminating the need for key management, while symmetric encryption transforms data using a secret key that must be securely stored and managed. Unlike symmetric encryption, tokenization does not rely on mathematical algorithms to protect data but relies on a secure token vault to map tokens back to original data. Symmetric encryption provides strong confidentiality through cryptographic means, while tokenization enhances data security by minimizing the scope of sensitive data exposure and reducing compliance burdens like PCI DSS.
Use Cases for Tokenization
Tokenization is widely used in payment processing systems to replace sensitive cardholder data with unique non-sensitive tokens, reducing the risk of data breaches. It is essential in industries like finance and healthcare for securing personally identifiable information (PII) without altering data format, enabling compliance with PCI-DSS and HIPAA standards. Unlike symmetric encryption, tokenization simplifies data protection by eliminating the need for complex key management while maintaining seamless integration with existing systems.
Use Cases for Symmetric Encryption
Symmetric encryption is widely used for securing data in applications where fast processing and efficient key management are critical, such as encrypting large volumes of data in databases, securing communication channels like TLS, and protecting sensitive information in cloud storage. It excels in scenarios requiring confidentiality with limited key distribution complexity, making it ideal for internal system encryption and bulk data transfer. High-performance environments such as VPNs, disk encryption, and IoT devices also rely on symmetric encryption for real-time data protection.
Security Implications: Tokenization vs Symmetric Encryption
Tokenization replaces sensitive data with non-sensitive tokens, minimizing exposure and reducing the risk of data breaches by storing actual data in a secure vault. Symmetric encryption secures data by transforming it into ciphertext using a single key, but the key management poses a critical vulnerability if compromised. Tokenization limits the attack surface by isolating sensitive information, while symmetric encryption requires rigorous key protection to maintain confidentiality and integrity.
Compliance and Regulatory Considerations
Tokenization reduces the risk of sensitive data exposure by substituting sensitive data with non-sensitive tokens, simplifying compliance with regulations like PCI DSS and GDPR. Symmetric encryption secures data through cryptographic algorithms requiring key management, which mandates stringent controls under standards such as HIPAA and SOC 2 to prevent unauthorized access. Organizations often favor tokenization for compliance efficiency, while symmetric encryption is essential where data confidentiality and integrity must be maintained throughout processing and storage.
Performance and Scalability Factors
Tokenization offers superior performance and scalability compared to symmetric encryption by replacing sensitive data with non-sensitive tokens, reducing the computational overhead during data processing. Symmetric encryption requires intensive cryptographic operations for both encryption and decryption, which can slow down systems under high transaction volumes. Tokenization systems can scale horizontally more efficiently since token lookup and replacement demand less CPU resources, enhancing throughput in large-scale environments.
Choosing the Right Solution for Your Organization
Tokenization reduces the risk of data exposure by replacing sensitive information with non-sensitive tokens, making it ideal for payment processing and compliance with PCI DSS. Symmetric encryption secures data by converting it into unreadable ciphertext using a secret key, offering strong protection for data at rest and in transit but requires robust key management. Choosing the right solution depends on your organization's regulatory requirements, performance needs, and the specific type of sensitive data being protected.
Tokenization Infographic
 libterm.com
libterm.com