A checksum is a value used to verify data integrity by detecting errors in digital information. It is calculated through algorithms that generate a unique code based on the contents of a file or message, ensuring your data has not been altered during transmission. Discover how checksums can protect your information and improve security by reading the rest of this article.
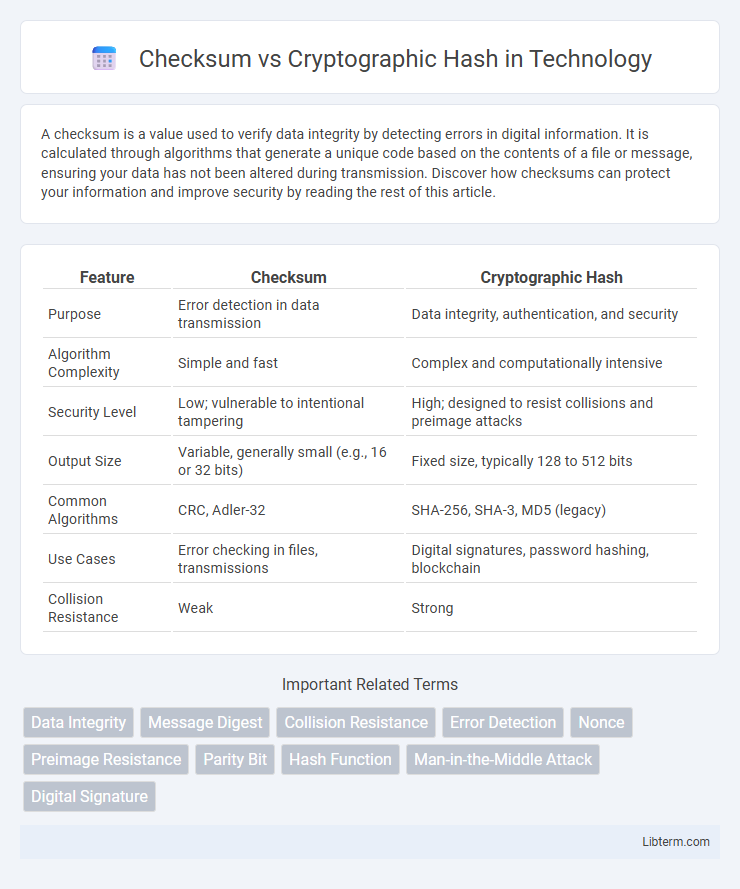
Table of Comparison
| Feature | Checksum | Cryptographic Hash |
|---|---|---|
| Purpose | Error detection in data transmission | Data integrity, authentication, and security |
| Algorithm Complexity | Simple and fast | Complex and computationally intensive |
| Security Level | Low; vulnerable to intentional tampering | High; designed to resist collisions and preimage attacks |
| Output Size | Variable, generally small (e.g., 16 or 32 bits) | Fixed size, typically 128 to 512 bits |
| Common Algorithms | CRC, Adler-32 | SHA-256, SHA-3, MD5 (legacy) |
| Use Cases | Error checking in files, transmissions | Digital signatures, password hashing, blockchain |
| Collision Resistance | Weak | Strong |
Introduction to Checksums and Cryptographic Hashes
Checksums are simple error-detection codes used to verify data integrity by producing a fixed-size value from a data block, primarily detecting accidental errors in transmission or storage. Cryptographic hashes generate a unique, fixed-length output designed to securely represent data, ensuring data authenticity and resistance to tampering through properties like collision resistance and preimage resistance. While checksums prioritize speed and error detection, cryptographic hashes focus on security, making them essential in digital signatures, password hashing, and data verification.
Definition: What is a Checksum?
A checksum is a value calculated from a data set used primarily for error detection in data transmission or storage, ensuring data integrity by identifying accidental changes. Unlike cryptographic hashes, checksums are generally simpler algorithms, such as CRC or Adler-32, designed for speed rather than security. They help verify data accuracy by detecting common errors but lack resistance to intentional manipulation or collisions common in cryptographic hash functions like SHA-256.
Definition: What is a Cryptographic Hash?
A cryptographic hash is a fixed-length string generated from input data using a hash function designed for security applications, ensuring properties like collision resistance and preimage resistance. It produces a unique digital fingerprint, making it nearly impossible to derive the original input or find two distinct inputs with the same output. Unlike simple checksum algorithms, cryptographic hashes play a crucial role in data integrity, digital signatures, and authentication processes.
Core Differences between Checksums and Cryptographic Hashes
Checksums primarily verify data integrity by detecting accidental errors during transmission or storage, using simple algorithms like CRC or Adler-32 that produce fixed-size values. Cryptographic hashes serve security purposes, generating unique digests resistant to collisions and preimage attacks through complex functions such as SHA-256 or SHA-3. The core difference lies in cryptographic hashes ensuring both data integrity and authentication, while checksums only provide basic error detection without security guarantees.
Common Algorithms Used in Checksums and Cryptographic Hashes
Common checksum algorithms include CRC32, Adler-32, and simple parity checks, designed primarily for error detection in data transmission. Cryptographic hash functions such as SHA-256, SHA-3, and MD5 provide data integrity and security by producing fixed-size, collision-resistant hashes essential for authentication and digital signatures. While checksums prioritize speed and error detection, cryptographic hashes emphasize resistance to pre-image attacks and collision vulnerabilities, making them suitable for secure applications.
Use Cases for Checksums
Checksums are primarily used for error detection in data transmission and storage, ensuring data integrity by identifying accidental changes or corruption. Common applications include file verification, network packet validation, and integrity checks on disks or databases. Unlike cryptographic hashes, checksums are not designed for security but provide fast, simple mechanisms for detecting accidental data errors.
Use Cases for Cryptographic Hashes
Cryptographic hashes are essential for securing data integrity in applications like digital signatures, password storage, and blockchain technology. Unlike simple checksums, cryptographic hashes produce unique, fixed-size outputs resistant to collisions and preimage attacks, ensuring reliable authenticity verification. They are widely used in cybersecurity to detect tampering, authenticate messages, and generate secure keys for encryption protocols.
Security Implications: Checksums vs Cryptographic Hashes
Checksums provide basic error detection primarily for data integrity in transmission or storage but are vulnerable to intentional manipulation due to their simplicity and lack of collision resistance. Cryptographic hashes, such as SHA-256 or SHA-3, offer strong security properties including collision resistance and preimage resistance, making them essential for verifying data authenticity and protecting against tampering. The security implications highlight that cryptographic hashes are indispensable in secure applications like digital signatures, password storage, and blockchain, where checksum methods are insufficient to prevent attacks.
Performance Considerations and Efficiency Comparison
Checksums are designed for speed and low computational overhead, making them ideal for error-checking and basic data integrity verification in performance-sensitive environments. Cryptographic hashes, such as SHA-256 or SHA-3, involve more complex algorithms that provide stronger security guarantees but require significantly more processing power and time. When comparing efficiency, checksums excel in throughput and minimal resource use, whereas cryptographic hashes prioritize collision resistance and data authenticity at the cost of performance.
Best Practices for Choosing between Checksum and Cryptographic Hash
Selecting between checksum and cryptographic hash depends on security requirements and performance needs; checksums like CRC32 are optimal for detecting accidental data corruption due to their speed and simplicity, while cryptographic hashes such as SHA-256 provide robust resistance against intentional tampering and collision attacks. Best practices recommend using checksums for error-checking in non-adversarial environments and cryptographic hashes for data integrity verification when security is paramount. Implementations should consider factors like collision resistance, computational overhead, and vulnerability to attacks to ensure appropriate algorithm choice aligns with the application's threat model.
Checksum Infographic
 libterm.com
libterm.com