An Intrusion Detection System (IDS) monitors network traffic to identify suspicious activities and potential security breaches by analyzing data patterns and anomalies. It plays a crucial role in safeguarding your organization's digital assets by providing real-time alerts to help prevent cyberattacks. Discover how implementing an effective IDS can enhance your security strategy by reading the rest of the article.
Table of Comparison
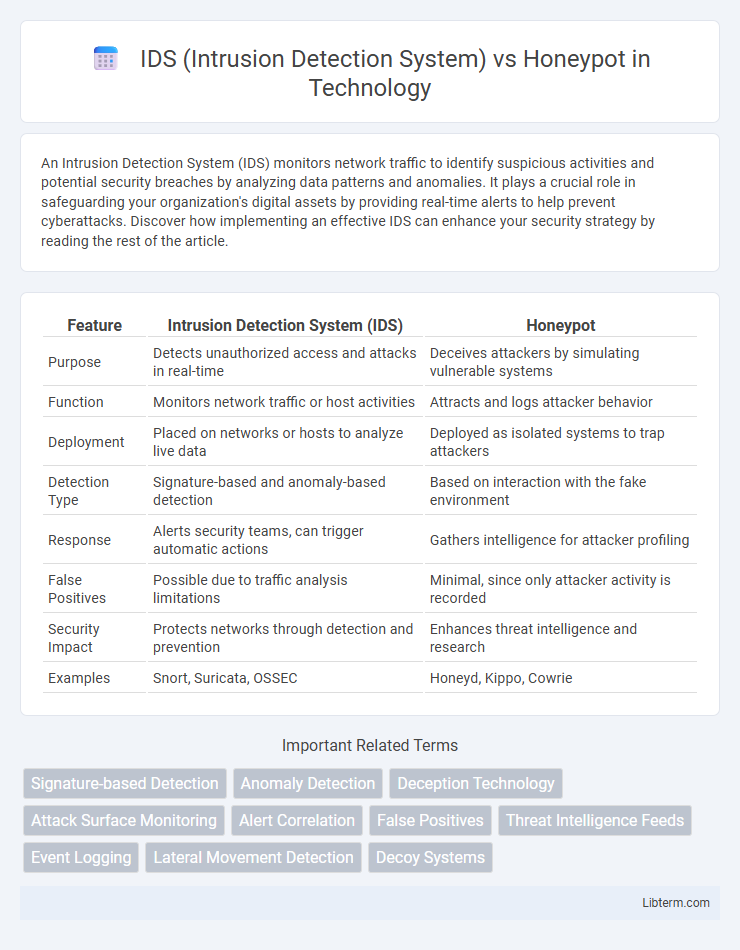
| Feature | Intrusion Detection System (IDS) | Honeypot |
|---|---|---|
| Purpose | Detects unauthorized access and attacks in real-time | Deceives attackers by simulating vulnerable systems |
| Function | Monitors network traffic or host activities | Attracts and logs attacker behavior |
| Deployment | Placed on networks or hosts to analyze live data | Deployed as isolated systems to trap attackers |
| Detection Type | Signature-based and anomaly-based detection | Based on interaction with the fake environment |
| Response | Alerts security teams, can trigger automatic actions | Gathers intelligence for attacker profiling |
| False Positives | Possible due to traffic analysis limitations | Minimal, since only attacker activity is recorded |
| Security Impact | Protects networks through detection and prevention | Enhances threat intelligence and research |
| Examples | Snort, Suricata, OSSEC | Honeyd, Kippo, Cowrie |
Introduction to Intrusion Detection Systems (IDS) and Honeypots
Intrusion Detection Systems (IDS) monitor network traffic to identify suspicious activities and potential security breaches, leveraging signature-based or anomaly-based detection methods to alert administrators of threats in real time. Honeypots are decoy systems designed to attract attackers, diverting malicious activity away from valuable assets while gathering intelligence on attack techniques and behavior. While IDS provides active monitoring and alerting, honeypots serve as proactive deception tools that enhance threat analysis and cybersecurity defense strategies.
Fundamental Principles: IDS vs Honeypot
An Intrusion Detection System (IDS) monitors network traffic or system activities to identify suspicious behaviors and potential security breaches by analyzing patterns and anomalies in real-time data. A Honeypot serves as a decoy system designed to attract attackers, diverting their efforts from critical assets while gathering intelligence on attack methods and tools. The fundamental principle of IDS lies in passive detection and alerting, whereas Honeypots proactively engage attackers to study threat vectors and enhance defensive strategies.
Types of Intrusion Detection Systems
Intrusion Detection Systems (IDS) include Network-based IDS (NIDS), Host-based IDS (HIDS), Signature-based IDS, and Anomaly-based IDS, each designed to detect unauthorized access through different monitoring techniques. Honeypots act as decoy systems to lure attackers and gather intelligence, rather than directly detecting intrusions like IDS solutions. NIDS analyzes network traffic for suspicious patterns, while HIDS monitors individual host activities, making them complementary to the deception tactics employed by honeypots in cybersecurity frameworks.
Honeypot Architectures and Classifications
Honeypot architectures are designed to simulate vulnerable systems, attracting attackers to gather intelligence and analyze attack vectors without compromising real assets. They are classified into low-interaction, medium-interaction, and high-interaction honeypots, each varying in complexity and level of attacker engagement; low-interaction honeypots emulate basic services, while high-interaction honeypots provide real operating systems for comprehensive attack analysis. Unlike IDS (Intrusion Detection Systems) that monitor and alert on suspicious activity passively, honeypots actively engage attackers, serving as controlled environments for threat research and improving overall security posture.
Key Differences: IDS and Honeypot Functionality
Intrusion Detection Systems (IDS) monitor network traffic and system activities to identify suspicious behavior or policy violations, alerting administrators to potential security breaches. Honeypots, by contrast, are decoy systems designed to attract attackers, allowing security teams to analyze attack methods and gather intelligence without risking actual assets. While IDS functions primarily as a detection and alert tool, honeypots serve as proactive traps to study attacker behavior and improve overall security posture.
Deployment Scenarios: IDS vs Honeypot
Intrusion Detection Systems (IDS) are typically deployed within network infrastructure to monitor real-time traffic and detect suspicious activities, making them suitable for broad surveillance in enterprise environments. Honeypots are strategically placed as decoys to attract attackers, allowing for in-depth analysis of attack methods and malicious behavior in controlled environments. While IDSs provide proactive alerting across multiple points, honeypots enable detailed threat intelligence by engaging attackers directly, often complementing IDS deployment in layered security architectures.
Strengths and Limitations of IDS
Intrusion Detection Systems (IDS) excel at monitoring and analyzing network traffic to identify potential security breaches in real-time, providing timely alerts for suspicious activities. However, IDS often generate false positives and require regular updates and tuning to effectively detect evolving threats. Unlike honeypots, which bait attackers to study their tactics, IDS primarily focuses on detection rather than deception or attacker engagement.
Advantages and Disadvantages of Honeypots
Honeypots provide an effective means to detect and analyze attacker behaviors by deliberately simulating vulnerable systems, which helps gather detailed intelligence without impacting production environments. Their primary advantage lies in reducing false positives compared to IDS, as any interaction with a honeypot is inherently suspicious, but they require significant maintenance and can be bypassed by sophisticated attackers aware of honeypot tactics. Disadvantages include the risk of the honeypot being used as a launchpad for further attacks if compromised, and limited coverage since honeypots only capture activity directed at themselves, missing broader network threats detectable by IDS.
Integration Strategies: IDS and Honeypot Combined
Integrating IDS and honeypot systems enhances network security by leveraging IDS's real-time threat detection with the honeypot's ability to lure and analyze sophisticated attacks. This combined strategy improves incident response accuracy through correlated alerts and enriched data, enabling deeper forensic analysis and faster remediation. Effective integration requires synchronized logging, automated alert sharing, and a centralized management platform to streamline threat intelligence and minimize false positives.
Selecting the Right Security Solution for Your Needs
Choosing between an Intrusion Detection System (IDS) and a honeypot depends on your security goals and network architecture. IDS monitors real-time traffic to detect suspicious activities and alert administrators, making it ideal for broad threat detection across a network. Honeypots act as decoy systems designed to lure attackers, providing deep insights into attack methods but requiring careful deployment to avoid risk and ensure relevant threat intelligence for targeted defense strategies.
IDS (Intrusion Detection System) Infographic
 libterm.com
libterm.com