Custom Resource Definitions (CRDs) extend Kubernetes functionality by allowing you to create your own resource types, enabling tailored resource management beyond the built-in options. These custom resources integrate seamlessly with Kubernetes APIs, providing flexibility to define and manage application-specific configurations. Explore the full article to understand how CRDs can empower your Kubernetes environment with enhanced customization.
Table of Comparison
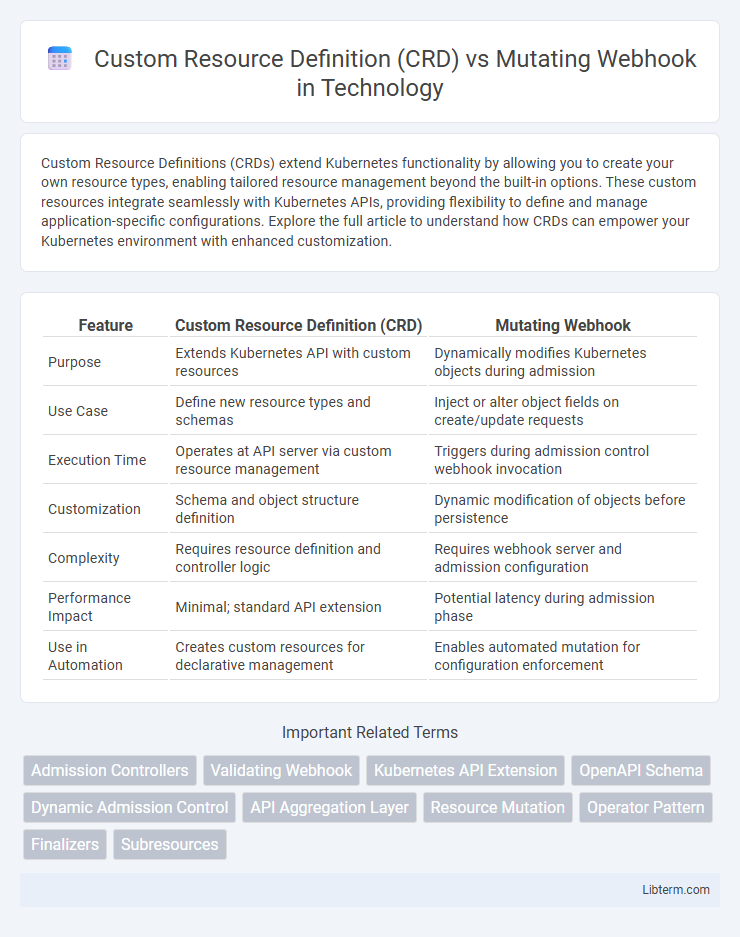
| Feature | Custom Resource Definition (CRD) | Mutating Webhook |
|---|---|---|
| Purpose | Extends Kubernetes API with custom resources | Dynamically modifies Kubernetes objects during admission |
| Use Case | Define new resource types and schemas | Inject or alter object fields on create/update requests |
| Execution Time | Operates at API server via custom resource management | Triggers during admission control webhook invocation |
| Customization | Schema and object structure definition | Dynamic modification of objects before persistence |
| Complexity | Requires resource definition and controller logic | Requires webhook server and admission configuration |
| Performance Impact | Minimal; standard API extension | Potential latency during admission phase |
| Use in Automation | Creates custom resources for declarative management | Enables automated mutation for configuration enforcement |
Understanding Custom Resource Definitions (CRDs)
Custom Resource Definitions (CRDs) enable Kubernetes users to create their own API objects, extending the Kubernetes API with custom resources tailored to specific application needs. Unlike Mutating Webhooks, which modify resources during admission requests, CRDs define new resource types that are stored and managed by the Kubernetes API server. Understanding CRDs is essential for building extensible Kubernetes applications by enabling declarative and versioned custom resource management.
Exploring Mutating Webhooks
Mutating Webhooks dynamically modify Kubernetes API requests, enabling automatic injection or alteration of pod specifications without manual intervention, enhancing operational flexibility. Unlike Custom Resource Definitions (CRDs), which extend Kubernetes with new resource types, Mutating Webhooks act at request time to enforce policies and inject sidecars, such as Istio proxies or security agents. This capability is crucial for seamless integration of custom logic and automation workflows in cloud-native environments, optimizing resource management and lifecycle consistency.
Key Differences Between CRDs and Mutating Webhooks
Custom Resource Definitions (CRDs) extend Kubernetes API by enabling users to define new resource types, providing structured declarative configuration and lifecycle management within the cluster. Mutating Webhooks intercept and modify Kubernetes API requests dynamically, allowing real-time changes to resource specifications before persistence without altering the resource types themselves. The core difference lies in CRDs creating new resource kinds for extensibility, whereas Mutating Webhooks function as admission controllers that mutate existing resources during API request processing.
Use Cases for CRDs in Kubernetes
Custom Resource Definitions (CRDs) in Kubernetes extend the API by allowing users to create and manage custom resources, enabling the automation of application-specific configurations and workflows. Use cases for CRDs include managing complex application states, implementing operator patterns for lifecycle management, and defining domain-specific configurations that Kubernetes does not natively support. Mutating Webhooks, by contrast, are primarily used for dynamically modifying Kubernetes API requests, making CRDs essential for declarative state management and custom resource modeling.
Use Cases for Mutating Webhooks
Mutating Webhooks are primarily used to dynamically modify Kubernetes API objects during creation or update, enabling automation of default value injection, label or annotation adjustments, and security policy enforcement without altering the original manifest. Unlike Custom Resource Definitions (CRDs) that extend Kubernetes with new resource types, Mutating Webhooks provide real-time object transformation, supporting use cases like injecting sidecar containers, setting resource limits, or modifying pod specifications based on organizational policies. Their ability to enforce cluster-wide customization at runtime makes them essential for operational consistency, compliance, and automated workflow orchestration within complex Kubernetes environments.
CRDs: Advantages and Limitations
Custom Resource Definitions (CRDs) enable Kubernetes users to extend the Kubernetes API by defining their own resource types, providing native integration, reuse of Kubernetes control loop mechanisms, and simplified management of application-specific data. One advantage of CRDs is their declarative nature, allowing versioning, validation, and native support within kubectl and other Kubernetes tools, enhancing developer productivity and consistency. However, CRDs can introduce limitations such as slower propagation of changes compared to admission webhooks, potential complexity in lifecycle management, and lack of dynamic mutation capabilities that Mutating Webhooks provide for request-time modifications.
Mutating Webhooks: Pros and Cons
Mutating Webhooks in Kubernetes enable dynamic modification of API requests, allowing automatic injection or alteration of object fields during creation or update, enhancing automation and consistency in cluster management. Pros include flexibility in enforcing policies and customizing resources without requiring direct controller implementation, while cons involve increased complexity, potential latency in API server responses, and risks of webhook failures impacting resource operations. Compared to Custom Resource Definitions (CRDs), which extend the Kubernetes API with new resource types, Mutating Webhooks focus on behavior modification, making them ideal for subtle, real-time changes but less suited for defining entirely new resource schemas.
When to Choose CRD over Mutating Webhook
Choose Custom Resource Definition (CRD) when you need to extend the Kubernetes API with new resource types that require declarative management and versioning support. CRDs are ideal for defining custom objects with structured schemas, enabling native kubectl interactions and validation. Mutating Webhooks are better suited for dynamic, runtime modifications to existing Kubernetes objects without creating new resource types.
Security Implications: CRD vs Mutating Webhook
Custom Resource Definitions (CRDs) extend Kubernetes APIs by allowing users to define new resource types, which can introduce security risks if custom controllers lack proper validation, leading to privilege escalation or unauthorized access. Mutating Webhooks modify API server requests dynamically, enabling granular policy enforcement and security controls, but pose risks if webhook servers are compromised or improperly configured, potentially allowing malicious mutations. Both mechanisms require rigorous RBAC management and auditing to mitigate vulnerabilities inherent in extending or intercepting Kubernetes API behaviors.
Best Practices for Implementing CRDs and Mutating Webhooks
Implementing Custom Resource Definitions (CRDs) should follow best practices such as defining clear schema validation using OpenAPI v3 to ensure data integrity and using proper versioning strategies to handle API evolution smoothly. Mutating Webhooks require careful handling of dependency and failure policies to avoid cascading errors and must strictly validate and mutate objects efficiently to reduce latency and prevent admission-time failures. Both CRDs and Mutating Webhooks benefit from thorough testing in staging environments, comprehensive logging, and adherence to Kubernetes API conventions to ensure reliability and maintainability.
Custom Resource Definition (CRD) Infographic
 libterm.com
libterm.com