Data flow analysis examines the movement and transformation of data within a software program, enabling optimization and error detection during development. By tracking variables and their values at different points, it enhances code quality and efficiency. Explore the rest of the article to understand how data flow analysis can improve your programming process.
Table of Comparison
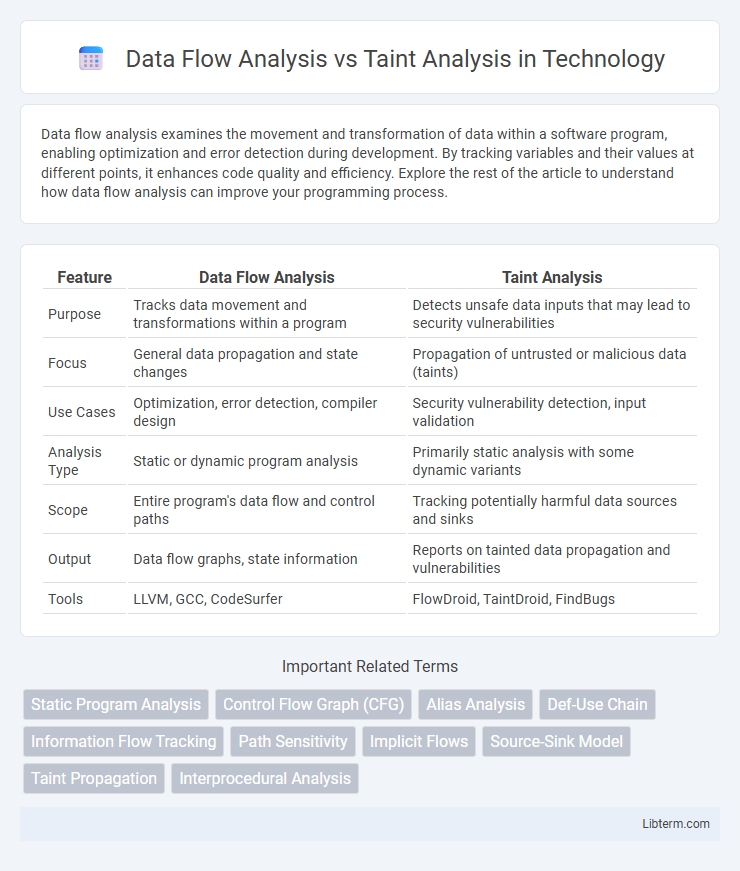
| Feature | Data Flow Analysis | Taint Analysis |
|---|---|---|
| Purpose | Tracks data movement and transformations within a program | Detects unsafe data inputs that may lead to security vulnerabilities |
| Focus | General data propagation and state changes | Propagation of untrusted or malicious data (taints) |
| Use Cases | Optimization, error detection, compiler design | Security vulnerability detection, input validation |
| Analysis Type | Static or dynamic program analysis | Primarily static analysis with some dynamic variants |
| Scope | Entire program's data flow and control paths | Tracking potentially harmful data sources and sinks |
| Output | Data flow graphs, state information | Reports on tainted data propagation and vulnerabilities |
| Tools | LLVM, GCC, CodeSurfer | FlowDroid, TaintDroid, FindBugs |
Introduction to Data Flow Analysis and Taint Analysis
Data Flow Analysis examines how data values propagate through program variables and statements, tracking definitions and uses to detect potential errors or optimize code. Taint Analysis specifically monitors untrusted or user-controlled inputs, marking them as "tainted" and tracing their influence across the system to identify security vulnerabilities like injection attacks. Both techniques use graph-based representations but differ in their focus: general data movement for Data Flow Analysis versus security-oriented tracking of tainted data in Taint Analysis.
Defining Data Flow Analysis
Data Flow Analysis involves tracking the flow of data through a program to detect potential issues like variable misuse, dead code, and optimization opportunities by examining the paths data takes between definitions and uses. Unlike Taint Analysis, which specifically targets the propagation of untrusted or malicious inputs to sensitive parts of a system, Data Flow Analysis provides a broader overview of all data movements within the program. This method aids in understanding program behavior, improving code quality, and enhancing static code analysis for security and performance.
Understanding Taint Analysis
Taint Analysis is a specialized form of Data Flow Analysis that tracks the flow of untrusted or potentially malicious input through a program to identify security vulnerabilities such as injection attacks or data leaks. Unlike general Data Flow Analysis, which focuses on analyzing variable definitions and usages to optimize code or detect errors, Taint Analysis marks data from untrusted sources as "tainted" and monitors its propagation to sensitive sinks. This targeted approach helps in detecting how unsafe data can influence program behavior, providing crucial insights for securing applications against common exploits.
Key Objectives of Data Flow Analysis
Data Flow Analysis aims to determine how data values propagate through program variables and control structures to identify optimization opportunities, detect potential errors, and ensure correct variable usage. It tracks the definitions and uses of variables to optimize code execution and improve program reliability by preventing issues like uninitialized variables and dead code. Taint Analysis, in contrast, specifically focuses on tracking the flow of untrusted or malicious input data to prevent security vulnerabilities such as injection attacks.
Core Purposes of Taint Analysis
Taint analysis primarily aims to track the flow of untrusted or malicious input data through a program to identify security vulnerabilities such as injection attacks or data leaks. Unlike general data flow analysis, which examines all possible data paths for optimization or correctness, taint analysis specifically focuses on detecting the propagation of tainted (potentially harmful) data to sensitive operations or sinks. This core purpose ensures early detection of exploitable pathways, enhancing software security against input-based exploits.
Techniques Used in Data Flow Analysis
Data Flow Analysis employs techniques such as control flow graphs, lattice theory, and fixed-point iteration to track the flow of data values through program variables and statements. These methods enable detection of properties like reaching definitions, live variables, and available expressions to optimize code and identify potential errors. In contrast, Taint Analysis focuses on tracking untrusted input through explicit taint propagation rules to identify security vulnerabilities.
Methods Applied in Taint Analysis
Taint analysis employs techniques such as source-to-sink tracking, symbolic execution, and control flow analysis to identify how untrusted input propagates through a program. Methods like sanitization checking and taint propagation modeling are used to detect vulnerabilities caused by improper handling of tainted data. These approaches enable precise identification of security risks by focusing on data dependencies and potential injection points within software systems.
Comparative Applications in Software Security
Data Flow Analysis tracks the flow of data through program variables and control structures to detect vulnerabilities like buffer overflows and logic errors by examining how data values propagate. Taint Analysis specifically identifies untrusted or user-controlled inputs that can influence sensitive operations, preventing injection attacks such as SQL injection and cross-site scripting. While Data Flow Analysis offers a broad perspective on data movement, Taint Analysis provides targeted detection of input-originated threats, making both essential for comprehensive software security assessments.
Strengths and Limitations: Data Flow vs Taint Analysis
Data Flow Analysis excels in tracking the propagation of data values and control flow throughout a program, offering comprehensive insights into variable states and potential optimization opportunities but can be computationally intensive and prone to false positives in complex codebases. Taint Analysis specializes in identifying security vulnerabilities by tracing untrusted inputs through the system to sensitive sinks, providing precise detection of injection and data leakage risks, though it may suffer from incomplete coverage and false negatives if taint sources or sinks are not well-defined. Balancing Data Flow's broad program understanding with Taint Analysis's targeted security focus enables more effective detection of code issues across performance and safety dimensions.
Choosing the Right Analysis Technique for Your Project
Choosing the right analysis technique for your project depends on specific security goals and the type of data being evaluated. Data flow analysis excels in tracking the movement of data across complex program structures to identify potential vulnerabilities, while taint analysis specializes in detecting untrusted input that can lead to security breaches like SQL injection or cross-site scripting. Evaluate the criticality of input validation and the complexity of data interactions within your application to determine whether a comprehensive data flow approach or a focused taint analysis best suits your security requirements.
Data Flow Analysis Infographic
 libterm.com
libterm.com