Session cookies temporarily store information about your activities on a website, enabling seamless navigation and personalized experiences. These cookies are deleted once you close your browser, ensuring your data remains secure during each visit. Discover how session cookies impact your online privacy and website functionality in the rest of this article.
Table of Comparison
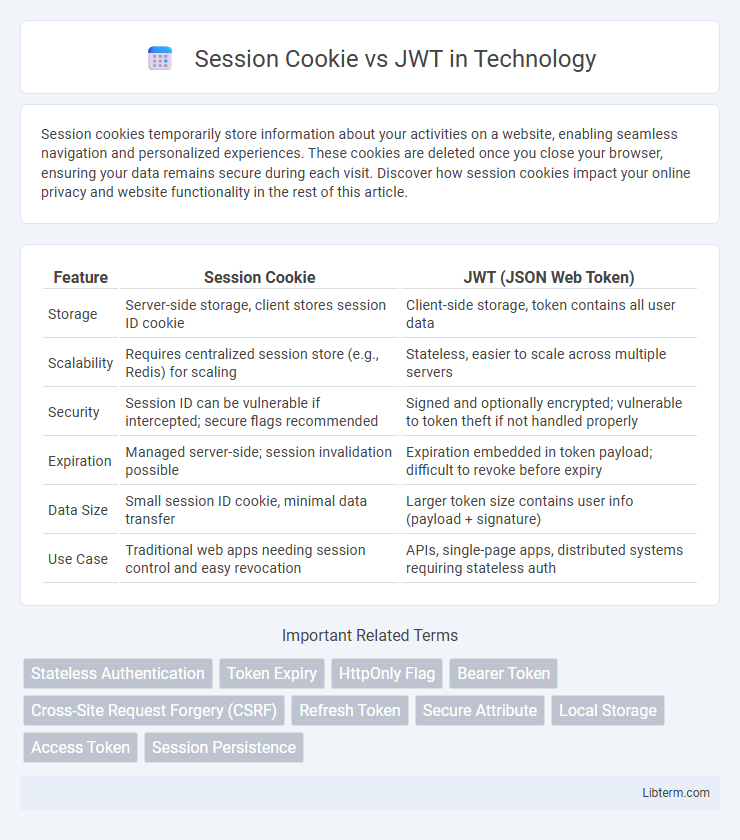
| Feature | Session Cookie | JWT (JSON Web Token) |
|---|---|---|
| Storage | Server-side storage, client stores session ID cookie | Client-side storage, token contains all user data |
| Scalability | Requires centralized session store (e.g., Redis) for scaling | Stateless, easier to scale across multiple servers |
| Security | Session ID can be vulnerable if intercepted; secure flags recommended | Signed and optionally encrypted; vulnerable to token theft if not handled properly |
| Expiration | Managed server-side; session invalidation possible | Expiration embedded in token payload; difficult to revoke before expiry |
| Data Size | Small session ID cookie, minimal data transfer | Larger token size contains user info (payload + signature) |
| Use Case | Traditional web apps needing session control and easy revocation | APIs, single-page apps, distributed systems requiring stateless auth |
Introduction to Session Cookies and JWT
Session cookies store user authentication data on the server and maintain session state through a unique session ID sent via browser cookies. JSON Web Tokens (JWT) contain encoded user information and claims, allowing stateless authentication by transmitting the token between client and server. Both methods enable secure user sessions but differ in storage approach and scalability, with session cookies relying on server memory and JWTs promoting decentralized validation.
What are Session Cookies?
Session cookies are small data files stored on a user's browser that maintain stateful information between client and server during a browsing session. These cookies typically hold a session identifier tied to server-side stored user data, enabling seamless authentication and personalization. Unlike JWTs, session cookies require server-side management and expiration handling to secure user sessions effectively.
What is JSON Web Token (JWT)?
JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as a JSON object, commonly used for authentication and authorization in web applications. It consists of three parts: a header, payload, and signature, enabling verification of data integrity and user identity without storing session data on the server. JWTs are stateless, allowing scalable client-server interactions by embedding user claims, such as user ID and expiration time, directly within the token.
How Session Cookies Work
Session cookies work by storing a unique session identifier on the client's browser, which is sent to the server with every HTTP request to maintain user state. The server keeps the session data in memory or a database, linking the session ID to user-specific information such as authentication status and preferences. This mechanism enables stateful sessions where the server manages the user's state, contrasting with stateless authentication methods like JWTs.
How JWT Authentication Works
JWT authentication works by encoding user information and claims into a JSON Web Token, which is digitally signed to ensure data integrity and authenticity. When a user logs in, the server generates a JWT and sends it to the client, which stores it typically in local storage or an HTTP header. For each subsequent request, the client includes the JWT, allowing the server to validate the token and authenticate the user without maintaining session state.
Key Differences Between Session Cookies and JWT
Session cookies store user authentication data on the server, creating stateful sessions that require server-side memory management, while JWTs (JSON Web Tokens) are stateless tokens containing encoded user information and claims that are stored client-side. Session cookies rely on a session ID transmitted between client and server, enhancing security by keeping sensitive data server-side, whereas JWTs carry all authentication data within the token, enabling scalability by reducing server load. The inherent difference in storage locations and validation methods leads to varied use cases regarding security, performance, and scalability in web authentication systems.
Security Considerations: Session Cookie vs JWT
Session cookies store user authentication data on the server, minimizing exposure to client-side attacks like token theft but requiring secure cookie flags (HttpOnly, Secure, SameSite) to prevent cross-site scripting (XSS) and cross-site request forgery (CSRF). JWTs store authentication data client-side in a signed token; they reduce server storage needs but increase risk if tokens are intercepted or improperly validated, necessitating strong encryption, short expiration times, and secure transmission via HTTPS. Both methods demand rigorous security measures, but session cookies generally offer better protection against token theft, while JWTs provide scalability and statelessness at the cost of increased complexity in securing token integrity.
Scalability and Performance Comparison
Session cookies store user data on the server, which can lead to scalability challenges as server memory usage increases with active sessions, impacting performance in large-scale applications. JSON Web Tokens (JWT) offload state management to the client by encoding user information within the token itself, enabling stateless authentication and better horizontal scalability without frequent server lookups. JWTs reduce server load and improve response times, making them more suitable for distributed architectures and microservices compared to traditional session cookies.
Use Cases: When to Choose Session Cookie or JWT
Session cookies are ideal for traditional web applications requiring server-side session management with tight control over user state and automatic handling of expiration and revocation. JSON Web Tokens (JWT) excel in stateless, distributed environments like microservices or single-page applications (SPA), where scalability and cross-domain authentication are critical. Choose session cookies for security-sensitive applications needing centralized session control, while JWT suits scenarios demanding decentralized, token-based authentication and flexible client-side storage.
Conclusion: Which Authentication Method is Best?
Session cookies offer robust security through server-side storage and easy invalidation, making them ideal for applications requiring strict access control and state management. JWTs provide scalability and stateless authentication, suitable for distributed systems and microservices due to their self-contained nature and reduced server load. Choosing the best method depends on application architecture, security requirements, and scalability needs, with session cookies excelling in secure environments and JWTs favored for flexible, high-performance implementations.
Session Cookie Infographic
 libterm.com
libterm.com