Data encryption transforms your sensitive information into unreadable code, protecting it against unauthorized access and cyber threats. It uses complex algorithms to secure data both at rest and during transmission, ensuring confidentiality and integrity. Discover how to implement effective encryption techniques to safeguard your digital assets in the rest of this article.
Table of Comparison
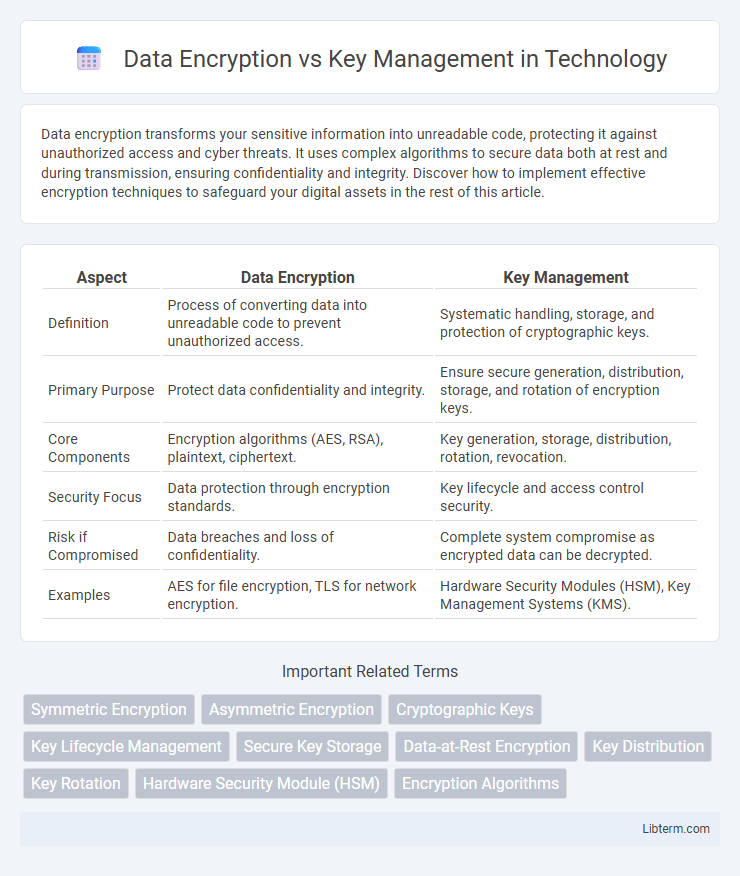
| Aspect | Data Encryption | Key Management |
|---|---|---|
| Definition | Process of converting data into unreadable code to prevent unauthorized access. | Systematic handling, storage, and protection of cryptographic keys. |
| Primary Purpose | Protect data confidentiality and integrity. | Ensure secure generation, distribution, storage, and rotation of encryption keys. |
| Core Components | Encryption algorithms (AES, RSA), plaintext, ciphertext. | Key generation, storage, distribution, rotation, revocation. |
| Security Focus | Data protection through encryption standards. | Key lifecycle and access control security. |
| Risk if Compromised | Data breaches and loss of confidentiality. | Complete system compromise as encrypted data can be decrypted. |
| Examples | AES for file encryption, TLS for network encryption. | Hardware Security Modules (HSM), Key Management Systems (KMS). |
Introduction to Data Encryption and Key Management
Data encryption transforms readable data into an unreadable format to protect sensitive information from unauthorized access. Key management involves the creation, distribution, storage, and destruction of cryptographic keys used in encryption processes to ensure data security. Effective encryption combined with robust key management safeguards confidentiality, integrity, and access control within digital communications and storage systems.
Importance of Protecting Sensitive Data
Protecting sensitive data requires robust encryption methods to secure information from unauthorized access and cyber threats. Effective key management ensures encryption keys are stored, distributed, and rotated properly to maintain the confidentiality and integrity of encrypted data. Combining strong data encryption with comprehensive key management safeguards sensitive information throughout its lifecycle, minimizing risks of data breaches and compliance violations.
Understanding Data Encryption: Definition and Methods
Data encryption involves converting plaintext into ciphertext using algorithms such as AES, RSA, or DES to protect information from unauthorized access. Common methods include symmetric encryption, which uses a single key for both encryption and decryption, and asymmetric encryption, utilizing a pair of public and private keys for secure data exchange. Understanding these methods is crucial for implementing effective security measures and ensuring data confidentiality in digital communication.
Key Management: Role and Significance
Key management is pivotal in securing encrypted data by generating, distributing, storing, and revoking cryptographic keys to maintain confidentiality and integrity. Effective key management mitigates risks such as unauthorized access and key compromise, ensuring that encryption remains robust against evolving cyber threats. Properly implemented key management systems, including Hardware Security Modules (HSMs) and key lifecycle policies, enable organizations to maintain control over sensitive data throughout its encrypted state.
Data Encryption Algorithms: Symmetric vs Asymmetric
Data encryption algorithms are categorized into symmetric and asymmetric types, both playing critical roles in data security. Symmetric encryption uses a single secret key for both encryption and decryption, offering high-speed performance suitable for large data volumes, with AES (Advanced Encryption Standard) as a widely adopted example. Asymmetric encryption relies on a pair of keys--a public key for encryption and a private key for decryption--enabling secure key exchange and digital signatures, with RSA and ECC (Elliptic Curve Cryptography) being prominent algorithms.
Key Management Best Practices
Effective key management is critical for ensuring the security of encrypted data, involving secure key generation, storage, rotation, and destruction processes to minimize exposure to unauthorized access. Organizations should implement hardware security modules (HSMs) for robust key storage, enforce strict access controls, and automate key rotation schedules to reduce the risk of key compromise. Adopting standardized protocols such as KMIP (Key Management Interoperability Protocol) enhances interoperability and auditability across diverse encryption systems.
Comparing Data Encryption and Key Management
Data encryption transforms plaintext into unreadable ciphertext using algorithms such as AES, ensuring data confidentiality during storage or transmission. Key management involves the generation, distribution, storage, and rotation of cryptographic keys, which are essential for maintaining encryption effectiveness and security. While data encryption protects the actual information, efficient key management prevents unauthorized access by safeguarding the keys that unlock encrypted data.
Common Challenges in Encryption and Key Management
Common challenges in data encryption and key management include secure key storage, effective key rotation, and ensuring encryption algorithms remain resistant to advanced cyber threats. Mismanagement of keys can lead to unauthorized data access, while inadequate encryption protocols increase vulnerability to breaches. Balancing ease of access with strong security controls is critical to maintaining data confidentiality and integrity.
Regulatory Compliance and Data Security
Data encryption ensures sensitive information remains confidential by converting it into unreadable ciphertext, which aligns with regulatory standards like GDPR and HIPAA requiring strong data protection measures. Effective key management controls the lifecycle of cryptographic keys, preventing unauthorized access and supporting audit trails critical for compliance audits. Together, robust encryption and key management frameworks mitigate data breaches and fulfill stringent regulatory requirements for data security.
Choosing the Right Solution: Key Takeaways
Effective data encryption requires robust key management to ensure encryption keys are securely generated, stored, and rotated. Choosing the right solution depends on factors such as compliance requirements, scalability, and integration with existing security infrastructure. Prioritizing automated key lifecycle management and strong access controls enhances overall data protection and reduces the risk of unauthorized access.
Data Encryption Infographic
 libterm.com
libterm.com