Access Control Lists (ACLs) are essential for managing network security by defining rules that control incoming and outgoing traffic based on IP addresses, protocols, and ports. They help prevent unauthorized access and can be tailored to fit specific security policies for enhanced protection. Explore the article to learn how ACLs can safeguard your network effectively.
Table of Comparison
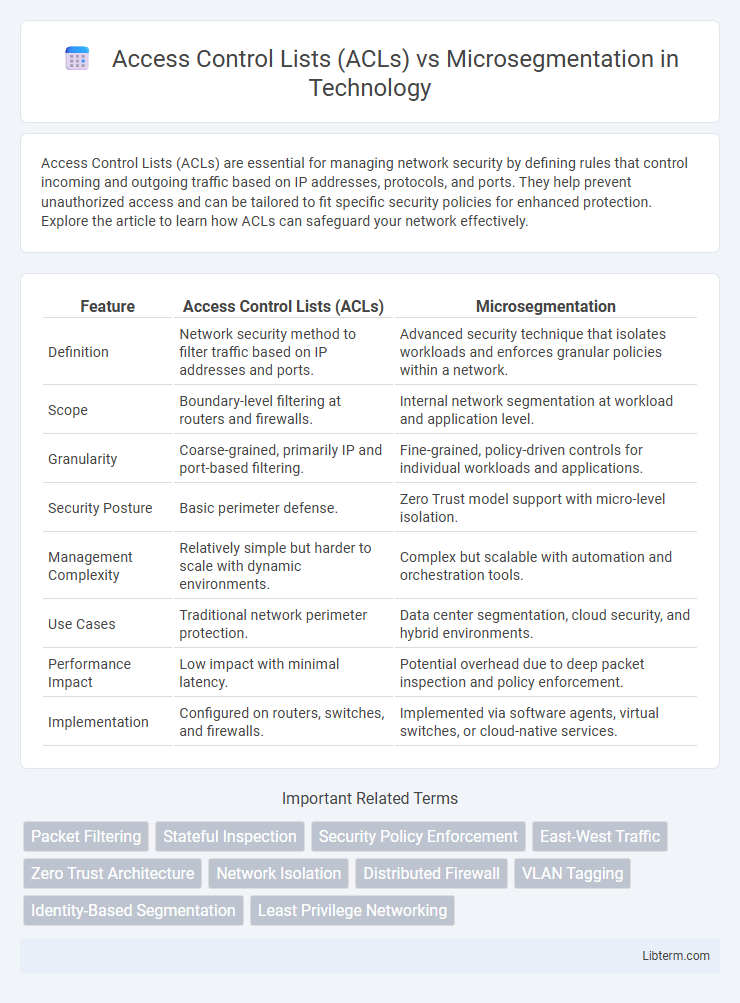
| Feature | Access Control Lists (ACLs) | Microsegmentation |
|---|---|---|
| Definition | Network security method to filter traffic based on IP addresses and ports. | Advanced security technique that isolates workloads and enforces granular policies within a network. |
| Scope | Boundary-level filtering at routers and firewalls. | Internal network segmentation at workload and application level. |
| Granularity | Coarse-grained, primarily IP and port-based filtering. | Fine-grained, policy-driven controls for individual workloads and applications. |
| Security Posture | Basic perimeter defense. | Zero Trust model support with micro-level isolation. |
| Management Complexity | Relatively simple but harder to scale with dynamic environments. | Complex but scalable with automation and orchestration tools. |
| Use Cases | Traditional network perimeter protection. | Data center segmentation, cloud security, and hybrid environments. |
| Performance Impact | Low impact with minimal latency. | Potential overhead due to deep packet inspection and policy enforcement. |
| Implementation | Configured on routers, switches, and firewalls. | Implemented via software agents, virtual switches, or cloud-native services. |
Introduction to Network Security: ACLs and Microsegmentation
Access Control Lists (ACLs) function by defining explicit rules that permit or deny network traffic at the router or firewall level, offering primary perimeter security. Microsegmentation enhances this approach by creating granular security zones within the network, isolating workloads and controlling east-west traffic to prevent lateral movement of threats. Combining ACLs with microsegmentation delivers layered defense, improving network security posture through both access management and internal traffic segmentation.
Defining Access Control Lists (ACLs)
Access Control Lists (ACLs) are rule-based filters applied to network devices that determine which packets are allowed or denied based on IP addresses, protocols, and ports, providing coarse-grained traffic control primarily at the perimeter. ACLs operate on Layer 3 and Layer 4 data, enabling basic traffic filtering but lacking granular application or user-level visibility. In contrast, microsegmentation divides the network into highly specific segments using software-defined policies, enabling fine-grained access control at the workload or application layer for enhanced security and reduced attack surface.
Understanding Microsegmentation
Microsegmentation enhances network security by creating granular, software-based security zones within data centers and cloud environments, limiting lateral movement of threats. Unlike Access Control Lists (ACLs) that primarily filter traffic based on IP addresses and ports at the perimeter level, microsegmentation enforces policies at the workload level, providing precise access control. This dynamic segmentation approach improves visibility and control over east-west traffic, reducing attack surfaces and complying with zero-trust security models.
Core Differences Between ACLs and Microsegmentation
Access Control Lists (ACLs) primarily manage network traffic by defining explicit rules at the router or firewall level to allow or deny access based on IP addresses, ports, and protocols, operating mainly at the perimeter or subnet boundaries. Microsegmentation, by contrast, implements granular security policies at the workload or application level within data centers or cloud environments, isolating individual workloads regardless of underlying network topology. The core difference lies in ACLs offering coarse-grained, perimeter-focused access control, while microsegmentation enables fine-grained, internal network segmentation to reduce attack surfaces and contain lateral movement within the network.
Use Cases: When to Use ACLs
Access Control Lists (ACLs) are ideal for enforcing straightforward, rule-based network access controls at the perimeter or within specific network segments, providing packet filtering based on IP addresses, protocols, and ports. ACLs are commonly used in scenarios requiring basic traffic filtering, such as allowing or denying specific IP ranges access to resources or restricting traffic based on protocol types in traditional network architectures. Enterprises employing ACLs benefit from their simplicity and efficiency in managing access control policies without the complexity of microsegmentation.
Use Cases: When to Opt for Microsegmentation
Microsegmentation excels in securing dynamic cloud environments and multi-tenant infrastructures by enforcing granular, workload-level policies that minimize lateral movement of threats. Access Control Lists (ACLs) are suitable for traditional network perimeter defense, controlling traffic between defined network segments but lack the fine-grained control required for modern, east-west traffic within data centers. Enterprises should opt for microsegmentation when visibility, security, and compliance demand precise internal segmentation across virtualized or containerized applications.
Security Benefits: ACLs vs Microsegmentation
Access Control Lists (ACLs) provide fundamental security benefits by filtering network traffic based on IP addresses, protocols, and ports, effectively controlling access at the perimeter or between network segments. Microsegmentation enhances security by creating granular, policy-driven isolation within the network, limiting lateral movement of threats and enforcing strict security boundaries down to individual workloads or applications. While ACLs are effective for broad traffic control, microsegmentation offers superior protection against sophisticated attacks by enabling dynamic, context-aware enforcement of security policies across the entire network infrastructure.
Scalability and Flexibility Comparison
Access Control Lists (ACLs) offer straightforward scalability by managing permissions at a network or device level but can become cumbersome in complex, dynamic environments due to rigid rule sets and limited context awareness. Microsegmentation provides granular, workload-specific security policies that scale efficiently across distributed, cloud-native infrastructures, enabling dynamic adjustment to changing application needs. The flexibility of microsegmentation surpasses ACLs by allowing adaptive, identity-based controls that enhance security posture without sacrificing operational agility.
Implementation Challenges and Best Practices
Access Control Lists (ACLs) face implementation challenges such as scalability limitations and complexity in managing large rule sets across diverse network devices, often leading to policy inconsistencies and administrative overhead. Microsegmentation demands granular visibility and continuous monitoring, requiring integration with orchestration tools and detailed workload-level policies, which can be resource-intensive and complex to maintain in dynamic environments. Best practices include combining ACLs with microsegmentation for layered security, leveraging automation for policy enforcement, and regularly auditing rules to ensure accuracy and compliance.
Choosing the Right Approach for Your Organization
Access Control Lists (ACLs) provide a traditional method for regulating network traffic by defining explicit permissions at the device or interface level, suitable for organizations with straightforward network architectures. Microsegmentation offers granular security by isolating workloads within a network using software-defined policies, ideal for complex environments requiring enhanced threat containment and compliance. Selecting the right approach depends on factors such as network complexity, desired security posture, and scalability requirements, with many organizations adopting a hybrid strategy to balance simplicity and advanced protection.
Access Control Lists (ACLs) Infographic
 libterm.com
libterm.com