Hardware Security Modules (HSMs) provide a robust physical and logical safeguard for your cryptographic keys, ensuring secure key generation, storage, and management. These tamper-resistant devices are essential for protecting sensitive data and meeting compliance standards in industries where security is paramount. Learn more about how HSMs can enhance your data protection strategies in the rest of this article.
Table of Comparison
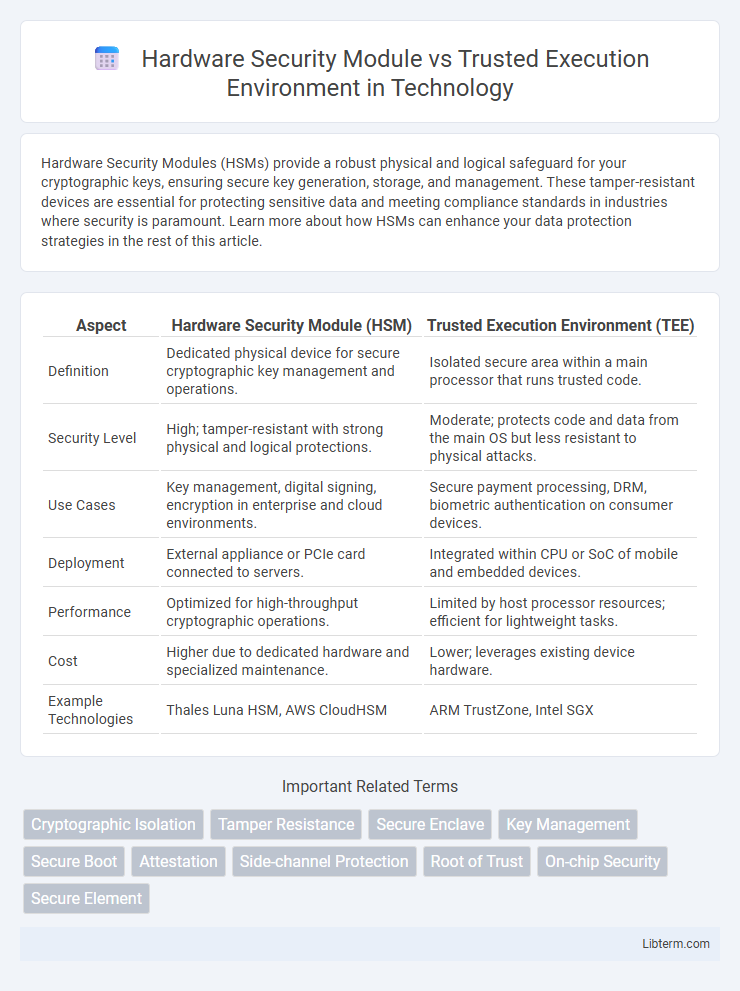
| Aspect | Hardware Security Module (HSM) | Trusted Execution Environment (TEE) |
|---|---|---|
| Definition | Dedicated physical device for secure cryptographic key management and operations. | Isolated secure area within a main processor that runs trusted code. |
| Security Level | High; tamper-resistant with strong physical and logical protections. | Moderate; protects code and data from the main OS but less resistant to physical attacks. |
| Use Cases | Key management, digital signing, encryption in enterprise and cloud environments. | Secure payment processing, DRM, biometric authentication on consumer devices. |
| Deployment | External appliance or PCIe card connected to servers. | Integrated within CPU or SoC of mobile and embedded devices. |
| Performance | Optimized for high-throughput cryptographic operations. | Limited by host processor resources; efficient for lightweight tasks. |
| Cost | Higher due to dedicated hardware and specialized maintenance. | Lower; leverages existing device hardware. |
| Example Technologies | Thales Luna HSM, AWS CloudHSM | ARM TrustZone, Intel SGX |
Introduction to Hardware Security Module (HSM) and Trusted Execution Environment (TEE)
Hardware Security Modules (HSMs) are dedicated physical devices designed to generate, store, and manage cryptographic keys within a highly secure, tamper-resistant environment, ensuring strong hardware-based protection for sensitive data and cryptographic operations. Trusted Execution Environments (TEEs) provide isolated, secure areas within a device's main processor that protect code and data from unauthorized access or modification, enabling secure execution of trusted applications. Both HSMs and TEEs enhance data security by safeguarding cryptographic processes, but while HSMs operate as separate hardware units, TEEs function as isolated environments embedded within existing processors.
Core Functions: HSM vs TEE
Hardware Security Modules (HSMs) provide dedicated cryptographic processing with strong key management, secure key storage, and tamper-resistant hardware designed to protect sensitive data and perform encryption, decryption, and digital signing operations. Trusted Execution Environments (TEEs) create isolated environments within processors, enabling secure execution of code and protection of data confidentiality and integrity in real-time applications. While HSMs focus on external cryptographic services and large-scale key management, TEEs emphasize internal trusted computing for mobile devices and embedded systems.
Architecture and Design Differences
Hardware Security Modules (HSMs) are standalone physical devices designed to provide secure key management and cryptographic processing with tamper-resistant hardware architecture, featuring dedicated secure processors and isolated cryptographic engines. Trusted Execution Environments (TEEs), integrated within general-purpose processors, create isolated runtime environments through hardware-enforced secure enclaves, relying on processor extensions like Intel SGX or ARM TrustZone to protect code and data integrity from the main operating system. HSMs emphasize physical security and compliance with standards such as FIPS 140-2, while TEEs offer flexible, software-driven isolation optimized for confidential computing within existing hardware platforms.
Security Features Comparison
Hardware Security Modules (HSMs) provide robust cryptographic key management with tamper-resistant hardware and physical security controls, ensuring secure key storage and cryptographic operations. Trusted Execution Environments (TEEs) offer isolated execution environments within a device's main processor, protecting sensitive data and code from unauthorized access and software attacks. While HSMs excel in high-assurance key protection and compliance standards, TEEs deliver flexible, software-level security for secure code execution and data confidentiality on consumer devices.
Key Use Cases for HSM and TEE
Hardware Security Modules (HSMs) are primarily used for cryptographic key management, secure key storage, and digital signing in enterprise environments, protecting keys from unauthorized access with tamper-resistant hardware. Trusted Execution Environments (TEEs) enable secure execution of code and data isolated from the main operating system, commonly used in mobile devices and IoT for protecting sensitive operations such as biometric authentication and digital rights management. Enterprises leverage HSMs for compliance and securing transaction processing, while TEEs provide a trusted platform for running secure applications in consumer devices and cloud computing.
Performance and Scalability Considerations
Hardware Security Modules (HSMs) deliver high cryptographic performance with dedicated hardware acceleration, enabling rapid processing of encryption, decryption, and key management tasks, which is crucial for enterprise-level scalability. Trusted Execution Environments (TEEs) offer moderate performance benefits by isolating sensitive code within the CPU, but their scalability is constrained by the underlying processor's capacity and shared resource limitations. HSMs scale more effectively in environments requiring consistent high-throughput cryptographic operations, while TEEs suit scenarios with moderate security needs and limited performance demands.
Integration and Deployment Scenarios
Hardware Security Modules (HSMs) offer dedicated, tamper-resistant devices designed for secure key management and cryptographic operations, ideal for enterprise environments requiring centralized, high-assurance security integration. Trusted Execution Environments (TEEs) provide isolated, trustworthy processing areas within general-purpose CPUs, enabling flexible deployment on endpoint devices like smartphones and IoT systems without additional hardware. Integration of HSMs suits data centers with stringent compliance needs, while TEEs enable scalable security on client devices, supporting decentralized applications and embedded systems.
Compliance and Regulatory Perspectives
Hardware Security Modules (HSMs) provide robust cryptographic key management and secure storage, widely recognized by compliance standards like FIPS 140-2/3 and PCI DSS, making them essential for meeting stringent regulatory requirements. Trusted Execution Environments (TEEs) offer isolated environments within processors to protect data and code integrity, supporting compliance by enabling secure execution of sensitive operations, though they may lack explicit certifications compared to HSMs. Organizations balancing compliance demands often deploy HSMs for critical key management while leveraging TEEs for flexible, hardware-based security that complements regulatory frameworks.
Cost Implications and ROI Analysis
Hardware Security Modules (HSMs) generally involve higher upfront costs due to specialized physical devices and maintenance requirements, making them a significant investment for enterprises seeking robust cryptographic key management. Trusted Execution Environments (TEEs) offer a cost-effective alternative by leveraging existing device hardware to create isolated environments, reducing capital expenses but potentially providing lower assurance levels for highly sensitive operations. ROI analysis reveals that while HSMs deliver superior security and compliance benefits translating into long-term savings on risk mitigation, TEEs provide quicker deployment and operational cost advantages that are suitable for less critical applications.
Choosing the Right Solution: HSM or TEE
Selecting between a Hardware Security Module (HSM) and a Trusted Execution Environment (TEE) depends on the specific security needs and deployment context. HSMs offer dedicated cryptographic processing with tamper-resistant hardware, ideal for high-assurance key management and regulatory compliance in enterprise environments. TEEs provide isolated, secure execution within general-purpose processors, suitable for protecting application code and data on consumer devices with lower cost and greater flexibility.
Hardware Security Module Infographic
 libterm.com
libterm.com