An Admission Controller is a critical component in Kubernetes that intercepts requests to the API server and enforces custom policies before objects are persisted. It ensures security, compliance, and resource management by validating or mutating requests based on predefined rules. Explore this article to understand how Admission Controllers can enhance your Kubernetes cluster management.
Table of Comparison
| Feature | Admission Controller | Mutating Webhook |
|---|---|---|
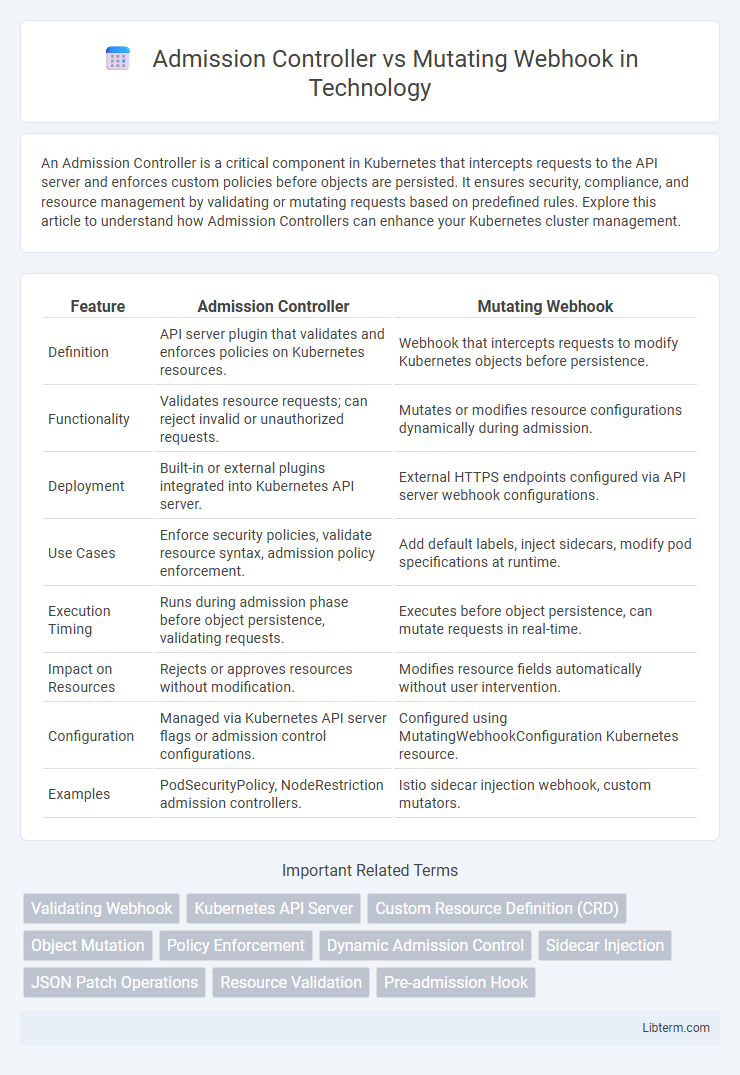
| Definition | API server plugin that validates and enforces policies on Kubernetes resources. | Webhook that intercepts requests to modify Kubernetes objects before persistence. |
| Functionality | Validates resource requests; can reject invalid or unauthorized requests. | Mutates or modifies resource configurations dynamically during admission. |
| Deployment | Built-in or external plugins integrated into Kubernetes API server. | External HTTPS endpoints configured via API server webhook configurations. |
| Use Cases | Enforce security policies, validate resource syntax, admission policy enforcement. | Add default labels, inject sidecars, modify pod specifications at runtime. |
| Execution Timing | Runs during admission phase before object persistence, validating requests. | Executes before object persistence, can mutate requests in real-time. |
| Impact on Resources | Rejects or approves resources without modification. | Modifies resource fields automatically without user intervention. |
| Configuration | Managed via Kubernetes API server flags or admission control configurations. | Configured using MutatingWebhookConfiguration Kubernetes resource. |
| Examples | PodSecurityPolicy, NodeRestriction admission controllers. | Istio sidecar injection webhook, custom mutators. |
Introduction to Kubernetes Admission Controllers
Kubernetes Admission Controllers are essential components that intercept API requests to enforce policies and validate resource configurations before persistence. Mutating Webhooks serve as dynamic Admission Controllers that modify or mutate resource objects during the admission process, enabling custom resource transformations. Unlike static Admission Controllers built into Kubernetes, Mutating Webhooks offer flexibility by allowing user-defined logic to adapt resource definitions in real time.
What Are Mutating Webhooks?
Mutating webhooks are admission controller plugins in Kubernetes that intercept API server requests to modify or mutate the objects before they are persisted. These webhooks allow dynamic alteration of pod specifications or other resource attributes during their creation or update, enabling automated configuration injection, such as sidecar containers or default labels. Unlike validating webhooks, mutating webhooks can change the incoming resource, enhancing flexibility and automation in cluster operations.
Core Functions of Admission Controllers
Admission Controllers enforce security policies and validate resource configurations before they are persisted in Kubernetes clusters, ensuring compliance and protecting cluster integrity. They operate at the API server level to accept, reject, or modify requests, while Mutating Webhooks specifically modify objects during admission to apply default settings or dynamic changes. Core functions of Admission Controllers include authentication enforcement, resource quota validation, and admission request mutation to streamline secure and consistent cluster operations.
Mutating Webhook: How It Works
Mutating Webhooks in Kubernetes intercept API server requests to modify or mutate objects before they are persisted. They are invoked during the admission phase, allowing dynamic changes such as injecting sidecar containers, adding labels, or setting default values. Configured via AdmissionController configurations, mutating webhooks enhance cluster behavior by enabling automated object transformations based on custom logic.
Key Differences Between Admission Controllers and Mutating Webhooks
Admission Controllers are built-in Kubernetes components that enforce policies during the API request processing, whereas Mutating Webhooks are customizable HTTP callbacks that modify requests dynamically. Admission Controllers primarily validate and enforce cluster-wide policies without altering requests, while Mutating Webhooks can intercept and modify pod specifications or other resources before they are persisted. The key difference lies in mutability: Admission Controllers mainly validate or reject requests, while Mutating Webhooks actively mutate resource definitions to inject configuration or defaults.
Use Cases for Admission Controllers
Admission Controllers enforce security, resource management, and policy compliance in Kubernetes by validating or rejecting requests before they persist in the cluster. They are essential for use cases such as enforcing namespace quotas, validating pod security policies, and controlling label or annotation standards across deployments. Mutating Webhooks modify API requests to inject default configurations or sidecars, but Admission Controllers provide consistent enforcement and compliance at the policy level.
When to Use Mutating Webhooks
Mutating Webhooks are ideal for modifying Kubernetes resource requests before they are persisted, particularly when automatic injection of sidecars, labels, or annotations is required. Use Mutating Webhooks when admission control must dynamically adjust resource definitions based on custom logic or policies, enhancing operational workflows without manual intervention. Admission Controllers are suitable for enforcing policies strictly, whereas Mutating Webhooks provide flexible modification capabilities during the admission process.
Security Considerations
Admission Controllers enforce security policies by validating requests before they reach Kubernetes API objects, ensuring only compliant changes are accepted. Mutating Webhooks modify resource configurations dynamically, which can introduce risks if not properly secured or validated, potentially leading to policy violations or privilege escalation. Both require stringent authentication, authorization, and audit logging to prevent unauthorized changes and maintain cluster integrity.
Performance and Scalability Aspects
Admission Controllers operate synchronously within the Kubernetes API server, providing faster decision-making and lower latency compared to Mutating Webhooks, which introduce network overhead due to external HTTP calls. Mutating Webhooks enable more dynamic, customizable resource processing but can become bottlenecks under high request loads, impacting cluster scalability. Optimizing webhook server performance and implementing retries or fallback mechanisms ensures scalability while maintaining efficient admission control workflows.
Choosing the Right Solution for Your Kubernetes Cluster
Admission Controllers enforce policies during Kubernetes API requests, providing built-in, static validations that are efficient and secure for common use cases. Mutating Webhooks offer dynamic, customizable request modifications, enabling advanced control such as injecting sidecars or altering pod specs at runtime, ideal for complex or evolving environments. Select Admission Controllers for simplicity and lower latency, while Mutating Webhooks suit scenarios requiring flexible, on-the-fly changes to resource definitions.
Admission Controller Infographic
 libterm.com
libterm.com