Repeatable actions and processes are essential for achieving consistency and efficiency in any project or task. Establishing clear, repeatable steps helps reduce errors and saves time by creating a reliable framework that can be followed with precision. Explore the rest of this article to discover how implementing repeatable methods can enhance your productivity and success.
Table of Comparison
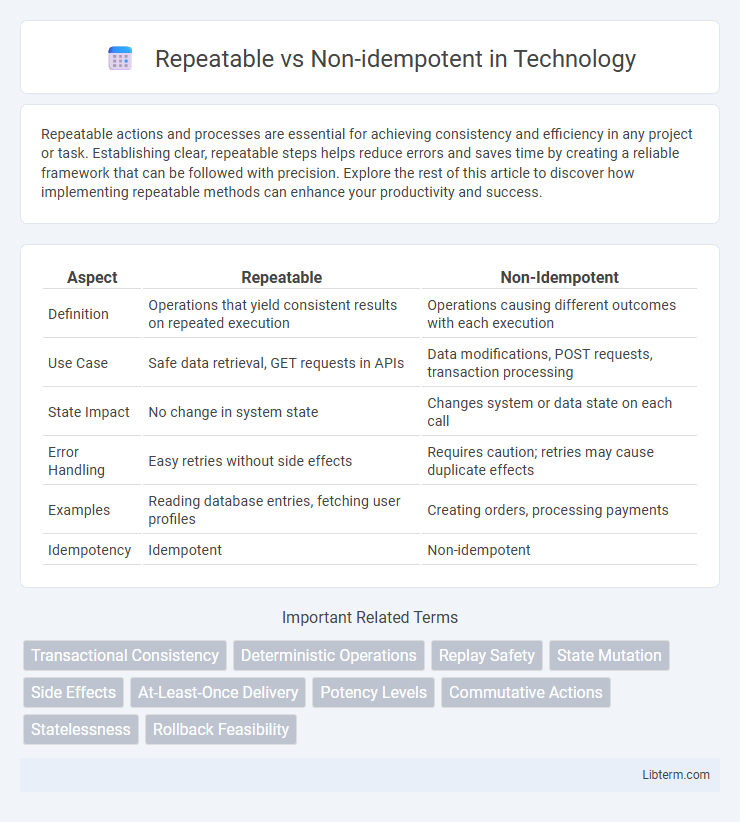
| Aspect | Repeatable | Non-Idempotent |
|---|---|---|
| Definition | Operations that yield consistent results on repeated execution | Operations causing different outcomes with each execution |
| Use Case | Safe data retrieval, GET requests in APIs | Data modifications, POST requests, transaction processing |
| State Impact | No change in system state | Changes system or data state on each call |
| Error Handling | Easy retries without side effects | Requires caution; retries may cause duplicate effects |
| Examples | Reading database entries, fetching user profiles | Creating orders, processing payments |
| Idempotency | Idempotent | Non-idempotent |
Understanding Repeatable and Non-Idempotent Operations
Repeatable operations yield the same result and state after multiple executions with identical inputs, ensuring consistent outcomes, which is crucial for reliable system behavior and error recovery. Non-idempotent operations produce different results or alter the system state with each execution, often used in scenarios like transaction processing or data modification where each action has a unique effect. Understanding the distinction helps developers design APIs and functions that maintain data integrity and system stability under repeated requests or retries.
Key Differences Between Repeatable and Non-Idempotent Actions
Repeatable actions are idempotent, meaning they produce the same result regardless of how many times they are performed, ensuring consistency and safety in repeated execution. Non-idempotent actions change state with each execution, causing different outcomes and often side effects, which requires careful handling to avoid unintended consequences. Understanding these differences is crucial for designing reliable APIs, where repeatable operations support safe retries, while non-idempotent ones demand explicit management to maintain data integrity.
Importance of Repeatability in Software Systems
Repeatability in software systems ensures that operations can be executed multiple times with the same input, yielding consistent results without unintended side effects, which is critical for fault tolerance and system reliability. Non-idempotent operations, which produce different outcomes on repeated execution, increase the risk of errors and data corruption during retries or failures. Implementing repeatable, idempotent functions enhances system robustness, simplifies error recovery processes, and supports scalable distributed architectures.
Real-World Examples of Repeatable Operations
Repeatable operations in computing, such as HTTP GET requests for fetching user profile data or querying a product catalog, can be executed multiple times without causing changes to the server state, ensuring consistent outcomes and reliability. Financial systems demonstrate repeatable operations when retrieving account balances or transaction histories, which do not alter data despite repeated requests. This contrasts with non-idempotent operations like POST requests for submitting payment transactions, where each repetition may alter the database by creating duplicate entries or triggering multiple charges.
Common Scenarios for Non-Idempotent Functions
Non-idempotent functions often occur in scenarios involving financial transactions, such as processing payments or transferring funds, where repeated execution results in multiple charges or transfers. Other common cases include sending email notifications or updating inventory levels, where each action has a distinct and cumulative effect. Ensuring these operations are carefully managed prevents data inconsistency and unintended side effects in application workflows.
Risks Associated with Non-Idempotent Processes
Non-idempotent processes pose significant risks due to their potential to generate unintended side effects when repeated, such as data duplication, inconsistent system states, or financial discrepancies. Unlike repeatable idempotent operations that produce the same result regardless of how many times they are executed, non-idempotent actions require strict control measures to prevent errors from multiple submissions or retries. Ensuring transactional integrity and implementing safeguards like unique request identifiers are critical to mitigating these risks in non-idempotent workflows.
Best Practices for Designing Repeatable Workflows
Designing repeatable workflows requires ensuring idempotency, where repeated execution of the same operation yields consistent results without unintended side effects. Best practices include using unique transaction identifiers, implementing state checks to prevent duplicate processing, and designing operations to be side-effect free or compensatable. These approaches minimize errors and improve reliability in distributed systems and automated pipelines.
Ensuring Safety in Non-Idempotent Transactions
Ensuring safety in non-idempotent transactions requires implementing strict concurrency controls and robust error-handling mechanisms to prevent unintended side effects caused by repeated requests. Techniques such as distributed locks, transaction logs, and unique request identifiers help maintain data integrity and consistency in these scenarios. Monitoring and retry strategies are crucial for detecting partial failures and safely recovering without duplicating transaction effects.
Tools and Techniques to Achieve Repeatability
Tools like Terraform, Ansible, and Kubernetes ensure repeatability by defining infrastructure as code, enabling consistent environment provisioning. Techniques such as version control, automated testing, and immutable infrastructure prevent unintended changes, maintaining predictable deployments. Continuous integration and continuous deployment (CI/CD) pipelines standardize execution, minimizing errors in repeatable operations.
Choosing Between Repeatable and Non-Idempotent Approaches
Choosing between repeatable and non-idempotent approaches hinges on the need for consistency versus flexibility in operations. Repeatable methods ensure reliable outcomes by producing the same result with multiple executions, ideal for critical transactional systems requiring data integrity. Non-idempotent approaches allow varied outcomes, suitable for operations where state changes or side effects are necessary, such as generating unique identifiers or processing user interactions.
Repeatable Infographic
 libterm.com
libterm.com