A firewall acts as a critical security barrier designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. It protects your devices from unauthorized access, cyber threats, and malicious attacks by filtering potentially harmful data packets. Discover how implementing an effective firewall strategy can safeguard your digital environment by exploring the full article.
Table of Comparison
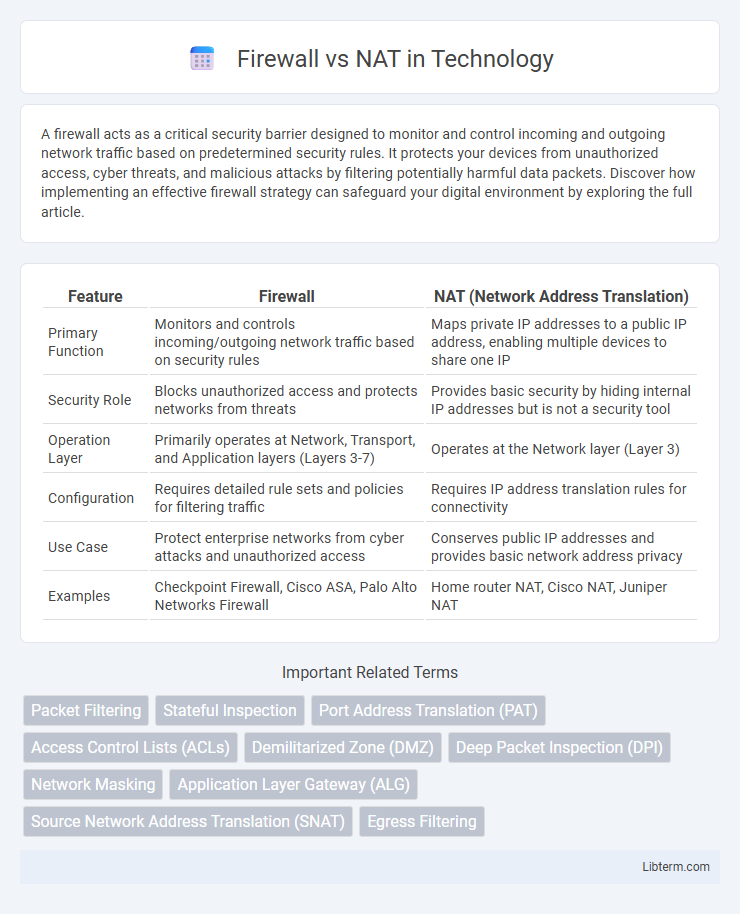
| Feature | Firewall | NAT (Network Address Translation) |
|---|---|---|
| Primary Function | Monitors and controls incoming/outgoing network traffic based on security rules | Maps private IP addresses to a public IP address, enabling multiple devices to share one IP |
| Security Role | Blocks unauthorized access and protects networks from threats | Provides basic security by hiding internal IP addresses but is not a security tool |
| Operation Layer | Primarily operates at Network, Transport, and Application layers (Layers 3-7) | Operates at the Network layer (Layer 3) |
| Configuration | Requires detailed rule sets and policies for filtering traffic | Requires IP address translation rules for connectivity |
| Use Case | Protect enterprise networks from cyber attacks and unauthorized access | Conserves public IP addresses and provides basic network address privacy |
| Examples | Checkpoint Firewall, Cisco ASA, Palo Alto Networks Firewall | Home router NAT, Cisco NAT, Juniper NAT |
Introduction to Firewall and NAT
Firewalls are network security devices designed to monitor and control incoming and outgoing traffic based on predetermined security rules, protecting networks from unauthorized access and threats. Network Address Translation (NAT) modifies IP address information in packet headers while in transit, enabling multiple devices on a local network to share a single public IP address and improving network security by hiding internal IP addresses. Both firewall and NAT play crucial roles in network security, with firewalls enforcing access policies and NAT providing IP address management and obscurity.
What is a Firewall?
A firewall is a network security device that monitors and controls incoming and outgoing traffic based on predetermined security rules, acting as a barrier between trusted internal networks and untrusted external networks. It protects systems from unauthorized access, cyber threats, and malicious attacks by filtering data packets according to IP addresses, ports, and protocols. Firewalls operate at various layers of the OSI model, including network, transport, and application layers, to enforce security policies and maintain network integrity.
What is Network Address Translation (NAT)?
Network Address Translation (NAT) is a networking process that modifies IP address information in packet headers while transferring traffic across a routing device, typically a router or firewall. NAT enables multiple devices on a private network to share a single public IP address, enhancing security and conserving IPv4 addresses. Unlike firewalls that primarily filter and monitor traffic based on security rules, NAT focuses on IP address translation to facilitate communication between private and public networks.
Core Functions: Firewall vs NAT
Firewalls primarily function to monitor and control incoming and outgoing network traffic based on predetermined security rules, preventing unauthorized access and cyber threats. Network Address Translation (NAT) translates private IP addresses into a public IP address for internet connectivity, enabling multiple devices to share a single IP and enhancing IP address conservation. While firewalls enforce security policies, NAT focuses on IP address management and routing, often working together to secure and streamline network communication.
Types of Firewalls Explained
Firewalls are categorized into packet-filtering, stateful inspection, proxy, and next-generation types, each providing varying levels of network security by controlling data flow based on different criteria. Packet-filtering firewalls examine packet headers for IP addresses and ports, while stateful inspection firewalls track active connections and make decisions based on the state and context of traffic. Proxy firewalls act as intermediaries by processing requests and responses, and next-generation firewalls integrate deep packet inspection, intrusion prevention, and application awareness to enhance threat detection and control.
How NAT Works in Network Security
NAT (Network Address Translation) works by modifying IP address information in packet headers while they traverse a router or firewall, enabling multiple devices on a private network to share a single public IP address. This process enhances network security by hiding internal IP addresses from external networks, reducing the attack surface and preventing direct access to private devices. Unlike firewalls that actively filter and block unauthorized traffic based on security rules, NAT primarily focuses on IP address translation to maintain internal network confidentiality and facilitate communication with external networks.
Key Differences Between Firewall and NAT
Firewall serves as a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules, while NAT (Network Address Translation) modifies IP address information in packet headers to enable multiple devices to share a single public IP address. Firewalls enforce access control policies to prevent unauthorized access and cyber threats, whereas NAT primarily facilitates IP address conservation and internal network communication. Unlike NAT, firewalls provide deep packet inspection and stateful filtering for enhanced network security.
Use Cases: When to Use Firewall or NAT
Firewalls are essential for controlling inbound and outbound network traffic based on security rules, protecting internal networks from unauthorized access and cyber threats. NAT (Network Address Translation) is primarily used to enable multiple devices on a private network to share a single public IP address, optimizing IP address usage and facilitating connectivity in IPv4 networks. Use firewalls when enforcing security policies and monitoring traffic, while NAT is ideal for conserving IP addresses and managing internal-to-external network translation.
Security Considerations: Firewall vs NAT
Firewalls and NAT both enhance network security but serve different purposes: firewalls enforce strict access control policies by filtering incoming and outgoing traffic based on predefined rules, preventing unauthorized access and cyber threats. NAT (Network Address Translation) primarily hides internal IP addresses by translating them to a single public IP, reducing direct exposure to external attackers and complicating reconnaissance efforts. Effective security architectures often combine firewalls with NAT to provide robust perimeter defense and internal network obscurity.
Choosing the Right Solution for Your Network
Selecting the appropriate network security solution depends on your specific needs: firewalls provide robust traffic filtering and threat prevention by monitoring and controlling incoming and outgoing network packets, whereas NAT (Network Address Translation) primarily manages IP address translation for internal network devices. For networks requiring strong protection against unauthorized access and detailed packet inspection, firewalls are essential, while NAT is suitable for conserving public IP addresses and simplifying internal IP management. Combining both technologies often offers comprehensive security and efficient network functionality.
Firewall Infographic
 libterm.com
libterm.com