OpenID Connect is a simple identity layer built on top of the OAuth 2.0 protocol that allows clients to verify the identity of end-users based on the authentication performed by an authorization server. It provides a standardized way to obtain user profile information while enhancing security and streamlining the login experience across multiple applications. Discover how OpenID Connect can improve your authentication processes and protect your digital identity by reading the rest of the article.
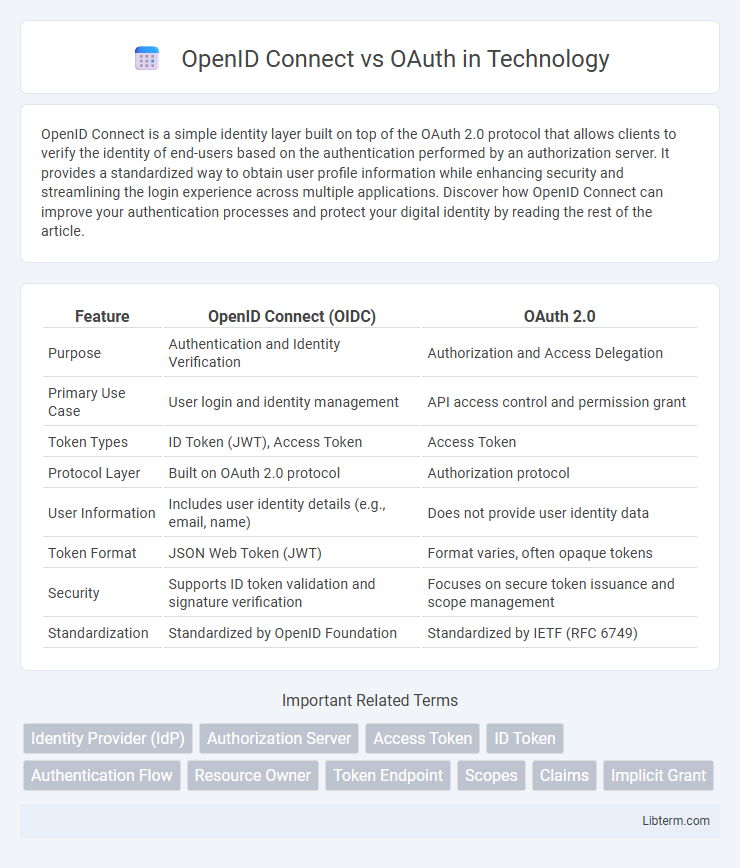
Table of Comparison
| Feature | OpenID Connect (OIDC) | OAuth 2.0 |
|---|---|---|
| Purpose | Authentication and Identity Verification | Authorization and Access Delegation |
| Primary Use Case | User login and identity management | API access control and permission grant |
| Token Types | ID Token (JWT), Access Token | Access Token |
| Protocol Layer | Built on OAuth 2.0 protocol | Authorization protocol |
| User Information | Includes user identity details (e.g., email, name) | Does not provide user identity data |
| Token Format | JSON Web Token (JWT) | Format varies, often opaque tokens |
| Security | Supports ID token validation and signature verification | Focuses on secure token issuance and scope management |
| Standardization | Standardized by OpenID Foundation | Standardized by IETF (RFC 6749) |
Understanding OpenID Connect and OAuth
OpenID Connect is an identity layer built on top of the OAuth 2.0 protocol that enables user authentication and provides user profile information. OAuth 2.0 primarily focuses on delegated authorization, allowing third-party applications to access user resources without sharing credentials. Understanding the distinction between OpenID Connect's authentication capabilities and OAuth's authorization framework is essential for implementing secure and efficient access management.
Key Differences Between OpenID Connect and OAuth
OpenID Connect extends OAuth 2.0 by adding an identity layer that enables authentication alongside authorization, allowing clients to verify user identity through ID tokens. OAuth is primarily designed for delegated access, providing secure authorization without sharing user credentials but does not handle user authentication. Key differences include OpenID Connect's use of standardized scopes like "openid" and ID tokens for identity information, whereas OAuth focuses solely on access tokens for resource delegation.
Core Components of OpenID Connect
OpenID Connect builds on the OAuth 2.0 protocol by adding an identity layer that provides authentication through core components such as the ID Token, UserInfo Endpoint, and Discovery Document. The ID Token is a JSON Web Token (JWT) that contains user identity information and is cryptographically signed to ensure integrity. The UserInfo Endpoint offers additional claims about the user, while the Discovery Document allows clients to dynamically obtain configuration details for interacting with the OpenID Connect provider.
Core Components of OAuth
OAuth's core components include the Resource Owner, Client, Authorization Server, and Resource Server, each playing a distinct role in secure access delegation. The Authorization Server issues access tokens after authenticating the Resource Owner, while the Client uses these tokens to access resources on the Resource Server. OpenID Connect builds on OAuth by adding an Identity Layer that provides authentication and user identity information alongside OAuth's authorization framework.
Use Cases: When to Choose OpenID Connect
OpenID Connect is ideal for authentication scenarios where verifying user identity and obtaining basic profile information are required, such as single sign-on (SSO) for web and mobile applications. OAuth is primarily designed for delegated authorization, enabling applications to access user resources without exposing credentials, making it suitable for API access and third-party integrations. Choose OpenID Connect when user authentication and identity verification are the main goals, especially in user-facing applications needing secure login and identity data.
Use Cases: When to Choose OAuth
OAuth is ideal for delegated access scenarios where users grant third-party applications limited permissions to their resources without sharing credentials, such as integrating social media login or accessing APIs on their behalf. It excels in enterprise environments needing secure access to APIs, enabling fine-grained authorization for services like cloud infrastructure management or payment processing. OAuth's token-based authorization suits mobile and web applications requiring scalable and secure resource sharing across diverse platforms.
Security Features Comparison
OpenID Connect extends OAuth 2.0 by adding identity verification and authentication capabilities, providing ID Tokens (JWT) that include user identity information, which OAuth lacks. OAuth primarily focuses on authorization and access delegation without guaranteeing user identity, making OpenID Connect essential for secure authentication workflows. Security features in OpenID Connect include nonce and state parameters to prevent replay and CSRF attacks, while OAuth relies on scopes and tokens for access control, ensuring robust security when combined.
Implementation Challenges and Considerations
Implementing OpenID Connect presents challenges such as ensuring proper token validation, handling ID token security, and managing user authentication flows that require integration with existing OAuth 2.0 frameworks. OAuth focuses primarily on authorization, so developers must address the gaps in identity verification and secure token exchange when extending it with OpenID Connect. Considerations include choosing appropriate scopes, managing session lifecycles, and protecting against token replay and phishing attacks to maintain robust security.
Real-World Examples and Scenarios
OpenID Connect enhances OAuth 2.0 by providing user authentication alongside authorization, making it ideal for single sign-on scenarios seen in Google's identity platform, where users authenticate and authorize third-party apps seamlessly. OAuth alone is commonly used in delegated access situations, such as when a user grants a photo app access to their Facebook photos without sharing login credentials. Enterprises implement OpenID Connect for secure access to internal applications, while OAuth enables third-party integrations like fitness apps accessing health data via APIs.
Choosing the Right Protocol for Your Application
OpenID Connect extends OAuth 2.0 by adding an identity layer, making it ideal for authentication and user identity verification in applications. OAuth 2.0 focuses on authorization, enabling secure delegated access to resources without exposing user credentials. Choosing the right protocol depends on whether your application requires authentication (OpenID Connect) or solely needs to manage access permissions (OAuth 2.0).
OpenID Connect Infographic
 libterm.com
libterm.com