Kerberos is a robust network authentication protocol designed to provide secure user verification across insecure networks by using secret-key cryptography. It protects your information by issuing time-limited tickets that grant access without transmitting passwords over the network. Discover how Kerberos enhances your network security and why it remains a critical component in modern authentication systems by reading the full article.
Table of Comparison
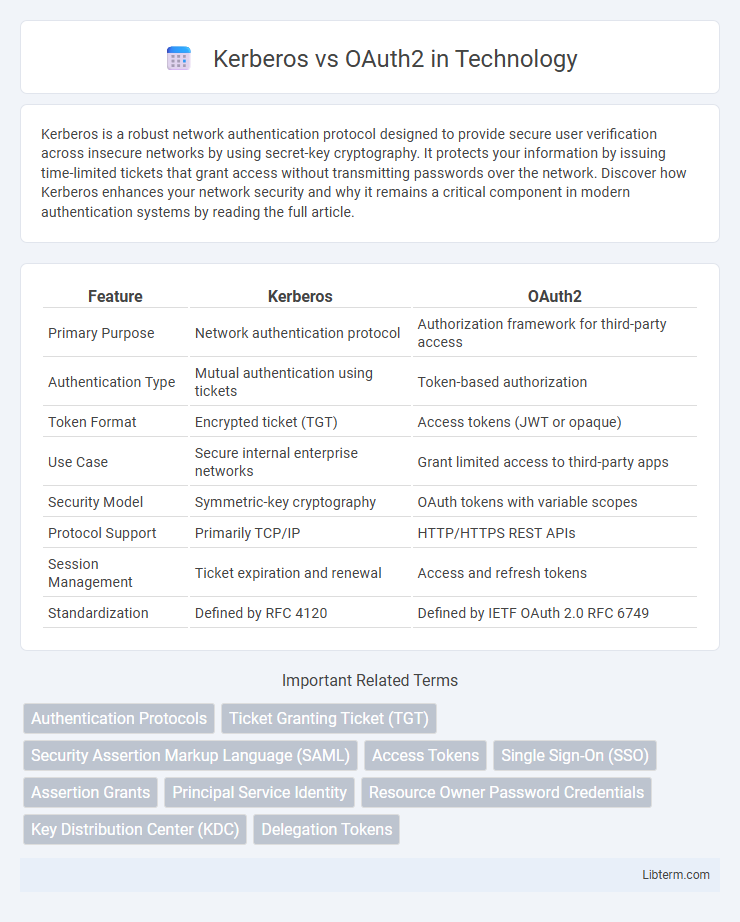
| Feature | Kerberos | OAuth2 |
|---|---|---|
| Primary Purpose | Network authentication protocol | Authorization framework for third-party access |
| Authentication Type | Mutual authentication using tickets | Token-based authorization |
| Token Format | Encrypted ticket (TGT) | Access tokens (JWT or opaque) |
| Use Case | Secure internal enterprise networks | Grant limited access to third-party apps |
| Security Model | Symmetric-key cryptography | OAuth tokens with variable scopes |
| Protocol Support | Primarily TCP/IP | HTTP/HTTPS REST APIs |
| Session Management | Ticket expiration and renewal | Access and refresh tokens |
| Standardization | Defined by RFC 4120 | Defined by IETF OAuth 2.0 RFC 6749 |
Introduction to Kerberos and OAuth2
Kerberos is a network authentication protocol designed to provide secure authentication using secret-key cryptography, primarily within trusted domains. OAuth2 is an authorization framework that enables third-party applications to obtain limited access to a user's resources without exposing credentials. Both protocols enhance security but serve distinct purposes: Kerberos focuses on identity verification within secure environments, while OAuth2 governs delegated access across web-based services.
Core Principles and Architecture
Kerberos operates on a trusted third-party authentication model using ticket-granting tickets (TGT) within a secure Key Distribution Center (KDC) to enable mutual authentication between clients and servers. OAuth2 employs an authorization framework where resource owners grant access tokens to clients via an authorization server without sharing credentials, supporting delegated access across web and mobile applications. Kerberos relies on symmetric key cryptography and time-stamped tickets for secure identity verification, whereas OAuth2 uses URL-based token exchange protocols with bearer tokens to manage access scopes and permissions.
Authentication vs Authorization
Kerberos is primarily designed for strong authentication using secret-key cryptography to verify user identities within trusted networks, providing secure ticket-based access control. OAuth2 focuses on authorization by granting limited access tokens that allow third-party applications to act on behalf of users without sharing credentials. While Kerberos ensures authenticated identity verification within enterprise environments, OAuth2 enables delegated access management across web and mobile platforms.
Workflow Comparison: How Each Protocol Operates
Kerberos operates through a ticket-based authentication system where clients obtain a Ticket Granting Ticket (TGT) from the Authentication Server, then use the TGT to request service tickets from the Ticket Granting Server, enabling access to various services without re-authenticating. OAuth2 follows an authorization delegation workflow where a client obtains an access token from the authorization server by presenting user credentials or authorization grants, then uses the token to access protected resources from the resource server. The Kerberos workflow emphasizes secure, mutual authentication within a trusted network using symmetric keys, while OAuth2 prioritizes flexible authorization delegation suitable for third-party app access via bearer tokens.
Use Cases: When to Use Kerberos or OAuth2
Kerberos is ideal for secure internal network authentication in enterprise environments, providing strong mutual authentication between clients and servers within a trusted domain. OAuth2 excels in delegated authorization scenarios, enabling third-party applications to access user resources on web and mobile platforms without sharing credentials. Use Kerberos for on-premises, intranet-based security, and OAuth2 for cloud-based services requiring scalable, user-consented access control.
Security Features and Mechanisms
Kerberos utilizes symmetric key cryptography and a trusted third-party Key Distribution Center (KDC) to provide mutual authentication between clients and servers, ensuring secure ticket-based access without transmitting passwords over the network. OAuth2 relies on token-based authorization with access tokens issued by an authorization server, supporting scopes and refresh tokens for delegated access and limited permissions. Kerberos offers strong protection against replay and eavesdropping attacks through time-stamped tickets, while OAuth2 emphasizes secure token storage and transport using HTTPS to prevent token interception and misuse.
Integration with Applications and Services
Kerberos provides seamless integration with enterprise applications through its ticket-based authentication, enabling secure single sign-on (SSO) across trusted network services using symmetric key cryptography. OAuth2 facilitates delegated authorization by allowing third-party applications to access user resources via token-based access without exposing user credentials, enhancing secure API integrations and mobile app interoperability. Both protocols support scalable authentication frameworks, but Kerberos excels in internal network environments, while OAuth2 is optimized for web-based and cloud service integrations.
Scalability and Performance Considerations
Kerberos offers robust security with a centralized authentication server but can face scalability challenges in large, distributed environments due to ticket management overhead and reliance on synchronized time. OAuth2, designed for web-scale applications, excels in scalability by allowing decentralized token issuance and stateless authentication mechanisms, reducing latency and server load. Performance in Kerberos is optimized for internal networks, while OAuth2 is better suited for internet-scale services requiring flexible, scalable access delegation.
Pros and Cons: Kerberos vs OAuth2
Kerberos offers robust mutual authentication using symmetric key cryptography, making it highly secure for internal network environments but relies heavily on a centralized Key Distribution Center, which can be a single point of failure. OAuth2 provides flexible delegated access to resources via tokens, supporting a wide range of clients and APIs, but its reliance on bearer tokens introduces risks like token theft and requires careful implementation of token expiration and refresh mechanisms. While Kerberos excels in enterprise internal authentication with minimal user interaction, OAuth2 is preferred for web-based and mobile applications catering to diverse third-party integrations.
Conclusion: Choosing the Right Protocol
Kerberos excels in secure, single sign-on authentication within trusted network environments, offering strong mutual authentication using ticket-based protocols. OAuth2 provides flexible authorization for third-party app access, enabling resource owners to grant limited permissions without sharing credentials, ideal for modern web and mobile applications. Selecting the right protocol depends on whether the priority is secure network authentication (Kerberos) or delegated access control for distributed systems (OAuth2).
Kerberos Infographic
 libterm.com
libterm.com