OpenID Connect is a simple identity layer built on top of the OAuth 2.0 protocol, enabling secure authentication and seamless single sign-on across web and mobile applications. This standard allows your users to verify their identity without sharing sensitive credentials, enhancing security and user experience. Explore the rest of the article to understand how OpenID Connect can transform your authentication process.
Table of Comparison
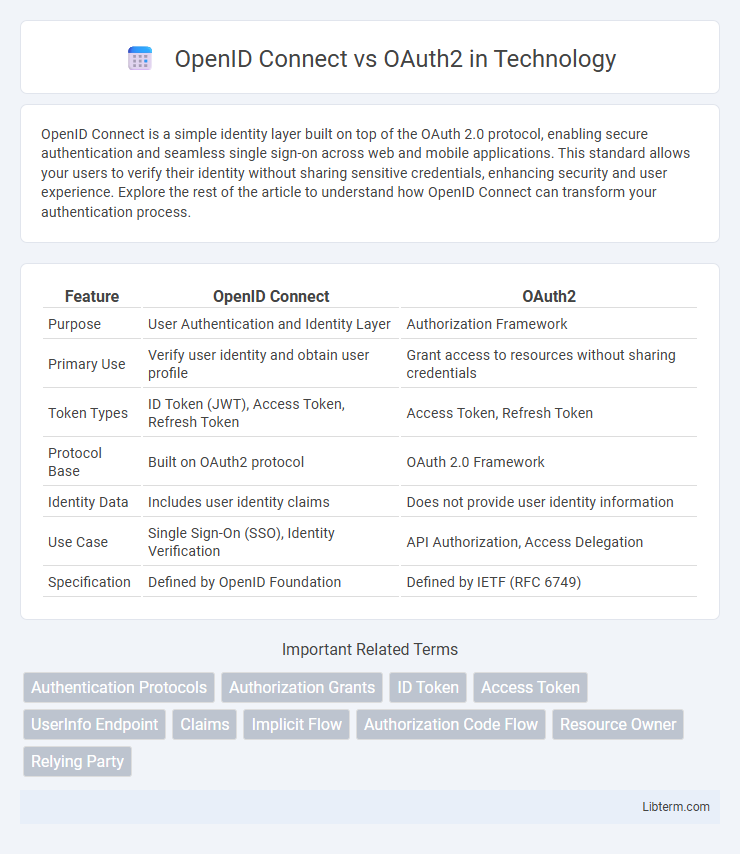
| Feature | OpenID Connect | OAuth2 |
|---|---|---|
| Purpose | User Authentication and Identity Layer | Authorization Framework |
| Primary Use | Verify user identity and obtain user profile | Grant access to resources without sharing credentials |
| Token Types | ID Token (JWT), Access Token, Refresh Token | Access Token, Refresh Token |
| Protocol Base | Built on OAuth2 protocol | OAuth 2.0 Framework |
| Identity Data | Includes user identity claims | Does not provide user identity information |
| Use Case | Single Sign-On (SSO), Identity Verification | API Authorization, Access Delegation |
| Specification | Defined by OpenID Foundation | Defined by IETF (RFC 6749) |
Introduction to OpenID Connect and OAuth2
OpenID Connect is an authentication protocol built on top of OAuth2, enabling secure user identity verification and single sign-on across multiple applications. OAuth2 is an authorization framework designed to grant limited access to user resources without sharing credentials, primarily focusing on delegated permissions. While OAuth2 handles authorization between clients and servers, OpenID Connect extends this by providing a standardized identity layer for authentication and user profile information.
Understanding OAuth2: Core Concepts
OAuth2 is an authorization framework designed to enable third-party applications limited access to user resources without exposing credentials. It involves key components such as resource owners, clients, authorization servers, and resource servers, each playing a specific role in the token exchange process. Tokens, including access tokens and refresh tokens, are critical for securely granting scoped permissions and maintaining session continuity within OAuth2 flows.
OpenID Connect: Extending OAuth2 for Authentication
OpenID Connect extends OAuth2 by adding an identity layer for secure user authentication, enabling applications to verify user identities via ID tokens alongside OAuth2's access tokens. This protocol builds on OAuth2's authorization framework, using JSON Web Tokens (JWT) to provide user profile information and ensure robust, interoperable authentication across platforms. OpenID Connect simplifies single sign-on (SSO) implementations and supports scopes like "openid" for streamlined identity management and enhanced security.
Key Differences Between OAuth2 and OpenID Connect
OAuth2 is an authorization framework designed to grant third-party applications limited access to user resources without exposing user credentials, focusing on delegated access control. OpenID Connect builds on OAuth2 by adding a standardized identity layer that provides authentication, enabling clients to verify the end-user's identity and obtain profile information via ID tokens. The primary difference lies in OAuth2's role in authorization versus OpenID Connect's inclusion of authentication with identity verification through JSON Web Tokens (JWT).
Use Cases: When to Choose OAuth2
OAuth2 excels in delegation scenarios where applications require limited access to user resources without exposing credentials, such as granting third-party apps permission to access APIs. It is ideal for authorization flows in mobile apps, single-page applications, and services interacting with resource servers, focusing on obtaining access tokens. Opt for OAuth2 when the primary goal is to authorize clients rather than authenticate users or obtain user identity information.
Use Cases: When to Choose OpenID Connect
OpenID Connect is ideal for user authentication scenarios where verifying identity and obtaining user profile information is crucial, such as single sign-on (SSO) for web and mobile applications. Unlike OAuth2, which focuses on delegated authorization to access resources, OpenID Connect builds on OAuth2 to provide an identity layer with standardized ID tokens and userinfo endpoints. Choose OpenID Connect when seamless user login, identity verification, and enhanced security are required for consumer-facing applications.
Security Considerations for OAuth2 and OpenID Connect
OAuth2 primarily focuses on authorization without specifying how to securely authenticate users, which can lead to vulnerabilities if token issuance and validation are not properly implemented. OpenID Connect, built on top of OAuth2, introduces ID tokens and standardized user authentication flows, enhancing security by enabling token signature verification and nonce parameters to prevent replay attacks. Properly configuring OAuth2 and OpenID Connect with HTTPS, token expiration, and secure storage mechanisms is critical to mitigating risks such as token theft, impersonation, and authorization code interception.
Implementation Challenges and Best Practices
Implementing OpenID Connect involves managing identity verification alongside OAuth2's token-based authorization, requiring careful integration of ID tokens and user authentication flows to ensure secure and seamless user experience. Common challenges include handling token validation, managing session states, and preventing token replay or misuse, which demand robust security measures such as JWT signature verification and proper nonce handling. Best practices emphasize adopting standardized libraries, leveraging well-documented endpoints for user info retrieval, and regularly updating protocols to comply with evolving security standards like PKCE for enhanced authorization security.
Real-World Examples and Industry Adoption
OpenID Connect extends OAuth2 by adding identity verification, enabling applications like Google Sign-In and Microsoft Azure AD to authenticate users seamlessly while authorizing access. Major enterprises such as Netflix and Salesforce rely on OpenID Connect for secure single sign-on (SSO) experiences, leveraging OAuth2's authorization framework to control resource access. Industry adoption favors OpenID Connect in scenarios requiring both authentication and authorization, whereas OAuth2 alone is typically implemented for delegated access without user identity assertions.
Conclusion: Selecting the Right Protocol for Your Application
Choosing between OpenID Connect and OAuth2 depends on your application's authentication and authorization needs. OpenID Connect extends OAuth2 by adding identity verification and user profile information, making it ideal for applications requiring secure user authentication. For purely authorization purposes without user identity management, OAuth2 remains the preferred protocol.
OpenID Connect Infographic
 libterm.com
libterm.com