Brute force attack involves systematically trying all possible password combinations to gain unauthorized access to a system, making it one of the most straightforward yet effective hacking methods. Cybersecurity experts emphasize the importance of strong, complex passwords and multi-factor authentication to defend against these persistent attempts. Explore the rest of the article to learn how to protect your digital assets from brute force attacks.
Table of Comparison
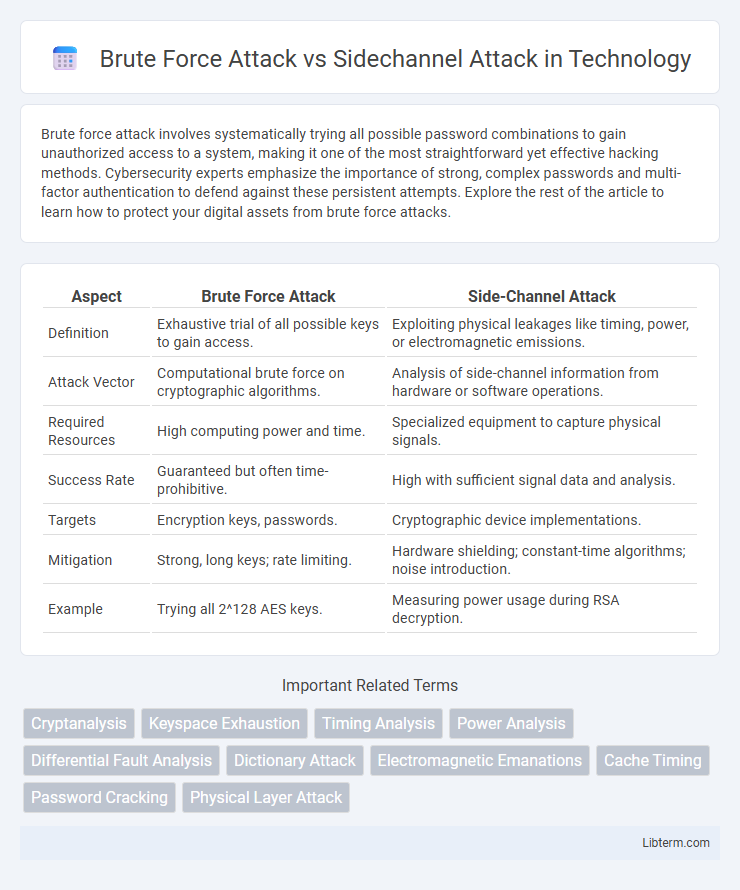
| Aspect | Brute Force Attack | Side-Channel Attack |
|---|---|---|
| Definition | Exhaustive trial of all possible keys to gain access. | Exploiting physical leakages like timing, power, or electromagnetic emissions. |
| Attack Vector | Computational brute force on cryptographic algorithms. | Analysis of side-channel information from hardware or software operations. |
| Required Resources | High computing power and time. | Specialized equipment to capture physical signals. |
| Success Rate | Guaranteed but often time-prohibitive. | High with sufficient signal data and analysis. |
| Targets | Encryption keys, passwords. | Cryptographic device implementations. |
| Mitigation | Strong, long keys; rate limiting. | Hardware shielding; constant-time algorithms; noise introduction. |
| Example | Trying all 2^128 AES keys. | Measuring power usage during RSA decryption. |
Introduction to Cybersecurity Attack Vectors
Brute force attacks involve systematically guessing passwords or encryption keys by trying all possible combinations until the correct one is found, exploiting weak authentication mechanisms. Side-channel attacks target the physical implementation of a system, extracting sensitive information such as cryptographic keys by analyzing timing, power consumption, or electromagnetic leaks. Both attack vectors highlight critical vulnerabilities in cybersecurity, emphasizing the need for robust encryption algorithms and secure hardware design.
Defining Brute Force Attacks
Brute force attacks involve systematically attempting every possible combination of passwords or encryption keys until the correct one is found, making them a direct and exhaustive method of breaking security. These attacks rely heavily on computational power and time, often targeting weak or short passwords vulnerable to exhaustive search. Unlike side-channel attacks that exploit physical or implementation weaknesses, brute force attacks focus purely on algorithmic and combinatorial manipulation to breach security systems.
Understanding Sidechannel Attacks
Sidechannel attacks exploit physical leakages from cryptographic devices, such as timing information, power consumption, or electromagnetic emissions, to extract secret keys without directly attacking the algorithms. Unlike brute force attacks that systematically try every possible key combination, sidechannel attacks leverage detailed measurements and analysis to significantly reduce the effort needed to break encryption. Understanding sidechannel attacks is critical for designing secure hardware and software resistant to these covert exploit techniques.
Mechanisms of Brute Force Attacks
Brute force attacks operate by systematically attempting every possible key or password combination until the correct one is found, leveraging computational power to expedite this exhaustive search. These attacks rely on the sheer volume of trial-and-error, often targeting encryption keys, passwords, or cryptographic hashes without exploiting any inherent system weakness. Unlike side-channel attacks that extract information from physical leakages like timing, power consumption, or electromagnetic emissions, brute force attacks depend purely on algorithmic perseverance and processing speed.
Techniques Used in Sidechannel Attacks
Sidechannel attacks exploit physical leakages such as power consumption, electromagnetic emissions, and timing information to infer secret data from cryptographic devices. Techniques include differential power analysis (DPA), where attackers analyze variations in power usage during encryption processes to recover keys, and electromagnetic analysis that captures signals emitted by hardware during computation. Unlike brute force attacks that rely on exhaustive key search, sidechannel methods leverage hardware imperfections to bypass algorithmic complexity and access sensitive information more efficiently.
Key Differences Between Brute Force and Sidechannel Attacks
Brute force attacks rely on systematically trying all possible keys or passwords until the correct one is found, making them resource-intensive and time-consuming but straightforward. Sidechannel attacks exploit physical or implementation vulnerabilities, such as timing information, power consumption, or electromagnetic leaks, to gather secret data indirectly without exhaustive key searching. The key difference lies in brute force attacks targeting the cryptographic algorithm itself by exhaustive search, while sidechannel attacks leverage real-world physical information to bypass cryptographic strength.
Real-World Examples of Brute Force Attacks
Brute force attacks involve systematically trying all possible password combinations to gain unauthorized access, exemplified by the 2012 LinkedIn breach where attackers exploited weak password hashes to expose millions of user credentials. These attacks contrast with side-channel attacks, which extract secret information through indirect means like power consumption or timing analysis. Real-world brute force incidents highlight the importance of implementing strong password policies and rate-limiting mechanisms to prevent exhaustive guessing attempts.
Notable Incidents Involving Sidechannel Attacks
Notable incidents involving sidechannel attacks include the 2010 attack on a smart card by researchers that extracted cryptographic keys using power analysis. In 2018, a sidechannel attack exploited electromagnetic emissions to compromise encryption on a widely used laptop model. These attacks demonstrate the practical vulnerabilities of devices to physical leakage methods, contrasting with brute force attacks that rely purely on systematic trial and error of passwords or keys.
Prevention and Mitigation Strategies
Implementing strong password policies and rate-limiting login attempts effectively prevent Brute Force Attacks by reducing the feasibility of exhaustive key searches. Mitigation of Sidechannel Attacks requires hardware-based countermeasures such as constant-time algorithms, masking techniques, and electromagnetic shielding to minimize information leakage. Combining multi-factor authentication with real-time anomaly detection further strengthens system resilience against both attack vectors.
Choosing the Right Defense Against Each Attack Type
Brute force attacks require robust cryptographic algorithms and strong password policies to mitigate risks, emphasizing the necessity of incorporating multi-factor authentication and rate limiting mechanisms. Side-channel attacks demand physical security measures and hardware-level countermeasures such as power analysis-resistant chips and constant-time algorithms to prevent leakage of sensitive information. Tailoring defenses to these attack vectors ensures a comprehensive security posture, combining software resilience with hardware safeguards.
Brute Force Attack Infographic
 libterm.com
libterm.com