A Web Application Firewall (WAF) protects websites by filtering and monitoring HTTP traffic between a web application and the internet to prevent cyberattacks such as SQL injection, cross-site scripting, and data breaches. Implementing a WAF enhances your security posture, ensuring sensitive information remains safe from malicious threats while maintaining website performance. Explore the rest of the article to learn how a WAF can safeguard your web assets effectively.
Table of Comparison
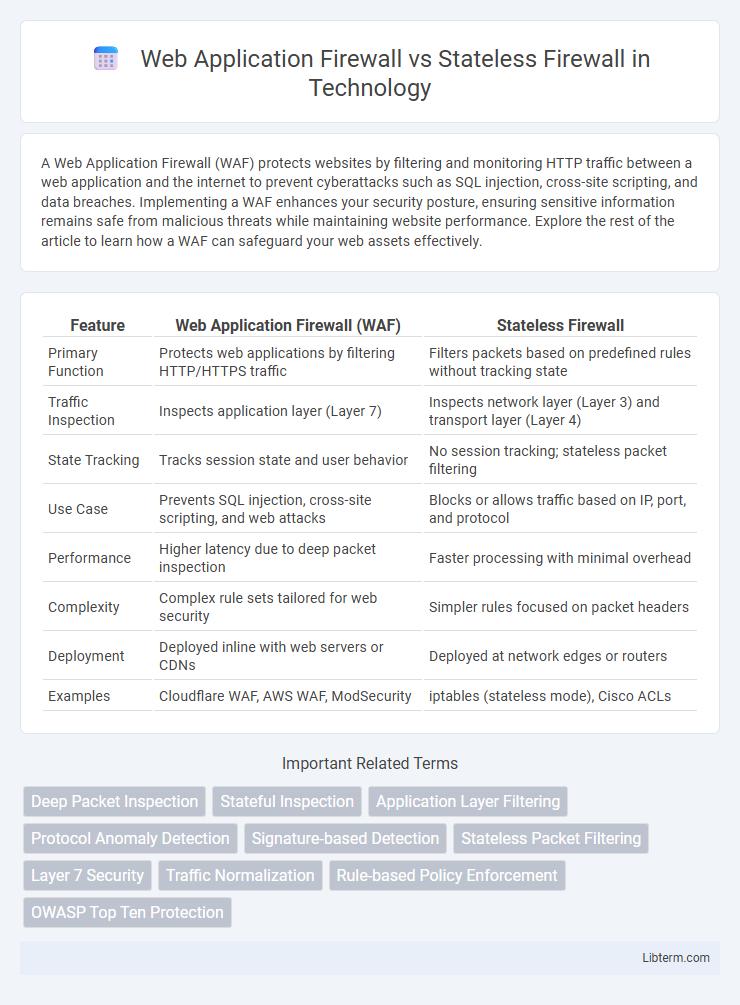
| Feature | Web Application Firewall (WAF) | Stateless Firewall |
|---|---|---|
| Primary Function | Protects web applications by filtering HTTP/HTTPS traffic | Filters packets based on predefined rules without tracking state |
| Traffic Inspection | Inspects application layer (Layer 7) | Inspects network layer (Layer 3) and transport layer (Layer 4) |
| State Tracking | Tracks session state and user behavior | No session tracking; stateless packet filtering |
| Use Case | Prevents SQL injection, cross-site scripting, and web attacks | Blocks or allows traffic based on IP, port, and protocol |
| Performance | Higher latency due to deep packet inspection | Faster processing with minimal overhead |
| Complexity | Complex rule sets tailored for web security | Simpler rules focused on packet headers |
| Deployment | Deployed inline with web servers or CDNs | Deployed at network edges or routers |
| Examples | Cloudflare WAF, AWS WAF, ModSecurity | iptables (stateless mode), Cisco ACLs |
Introduction to Web Application Firewalls
Web Application Firewalls (WAFs) specifically protect web applications by filtering, monitoring, and blocking HTTP traffic to and from a web service, targeting threats such as SQL injection, cross-site scripting, and zero-day exploits. Unlike stateless firewalls that inspect packets individually without context, WAFs analyze the content of web requests at the application layer, enabling more granular security against complex cyberattacks. Deploying a WAF enhances protection by understanding and enforcing rules based on web application behavior and vulnerabilities, thereby improving overall cybersecurity posture.
Understanding Stateless Firewalls
Stateless firewalls inspect packets independently without considering the context of prior traffic, making them faster but less effective against complex threats. They filter network traffic based solely on predefined rules like IP addresses, ports, and protocols, lacking the capability to track connection states or detect sophisticated attacks. Understanding this limitation highlights why stateless firewalls are often complemented by Web Application Firewalls (WAFs), which provide deep packet inspection and protect web applications from layer 7 attacks.
Core Functions of a Web Application Firewall
A Web Application Firewall (WAF) primarily protects web applications by filtering and monitoring HTTP/HTTPS traffic to block threats like SQL injection, cross-site scripting (XSS), and other application-layer attacks. Unlike stateless firewalls that focus on individual packets without context, WAFs analyze the full web transaction, enabling detection of malicious payloads and enforcing security policies based on application-specific behavior. Core functions of WAFs include input validation, session protection, and protection against zero-day vulnerabilities by inspecting traffic for known and emerging threats.
Key Features of Stateless Firewalls
Stateless firewalls operate by examining each packet independently without considering the state of active connections, making them faster and less resource-intensive than Web Application Firewalls (WAFs). Key features include simple packet filtering based on predefined rules like IP addresses, ports, and protocols, enabling efficient blocking of unauthorized traffic at the network layer. Unlike WAFs, stateless firewalls lack deep inspection capabilities and cannot analyze application-layer data, which limits their ability to detect complex web attacks or protect against application-level vulnerabilities.
Security Capabilities: WAF vs Stateless Firewall
Web Application Firewalls (WAFs) provide advanced security capabilities by inspecting HTTP/HTTPS traffic to detect and block web application attacks such as SQL injection, cross-site scripting (XSS), and zero-day exploits. In contrast, Stateless Firewalls operate at the network layer using predefined rules to filter packets based solely on IP addresses, ports, and protocols without tracking connection states, limiting their ability to analyze or mitigate application-layer threats. WAFs offer granular control and protection tailored for web applications, while Stateless Firewalls primarily enforce basic network access policies without deep packet inspection or behavioral analysis.
Advantages of Web Application Firewalls
Web Application Firewalls (WAFs) provide advanced protection by filtering, monitoring, and blocking malicious HTTP/S traffic targeting web applications, defending against threats such as SQL injection, cross-site scripting, and zero-day exploits. Unlike Stateless Firewalls that focus on packet filtering based solely on IP addresses and ports, WAFs analyze the context and content of web requests, offering granular security tailored to application-layer vulnerabilities. This deep inspection capability enhances security posture, reduces false positives, and improves compliance with industry standards like OWASP Top Ten and PCI DSS.
Benefits of Using Stateless Firewalls
Stateless firewalls offer faster packet processing by examining each packet individually without maintaining session state, significantly reducing latency and improving network performance. They require less memory and computational resources, making them highly scalable for large-volume traffic environments and suitable for high-speed data transfer. Stateless firewalls provide simplicity in configuration and are effective at enforcing broad, rule-based security policies, benefiting organizations with straightforward traffic filtering needs.
Common Use Cases and Deployment Scenarios
Web Application Firewalls (WAFs) are primarily deployed to protect web applications from Layer 7 attacks such as SQL injection, cross-site scripting, and application-layer DDoS, making them ideal for e-commerce sites, APIs, and SaaS platforms requiring deep packet inspection and custom rule sets. Stateless firewalls operate at Layer 3 and Layer 4, filtering packets based on IP addresses, ports, and protocols without retaining session information, which suits high-throughput environments like data centers or cloud networks needing fast, low-latency packet filtering. Enterprises often deploy WAFs inline alongside web servers for granular traffic analysis, while stateless firewalls are commonly positioned at network perimeters or between VLANs to enforce basic access control and reduce attack surfaces without the complexity of session management.
Choosing the Right Firewall: Factors to Consider
Choosing the right firewall involves evaluating security needs, traffic type, and deployment environment. Web Application Firewalls (WAFs) specialize in protecting HTTP/HTTPS traffic by filtering malicious web traffic, mitigating application-layer attacks like SQL injection and cross-site scripting. Stateless Firewalls, by contrast, offer high-speed packet filtering without session awareness, suitable for basic network traffic control but less effective against complex application attacks.
Conclusion: WAF vs Stateless Firewall – Which to Choose?
Choosing between a Web Application Firewall (WAF) and a Stateless Firewall depends on specific security needs and application environments. WAFs provide advanced protection by inspecting HTTP/HTTPS traffic and blocking web-based attacks such as SQL injection and cross-site scripting, making them ideal for safeguarding web applications. Stateless Firewalls, on the other hand, offer fast packet filtering based on IP addresses and ports but lack deep inspection capabilities, suitable for simple access control rather than comprehensive web security.
Web Application Firewall Infographic
 libterm.com
libterm.com