Hashing transforms data into fixed-size strings using algorithms that ensure data integrity and quick retrieval. It plays a crucial role in password security, digital signatures, and blockchain technology by enabling efficient data verification. Discover how hashing can enhance your security measures and optimize data management by reading the full article.
Table of Comparison
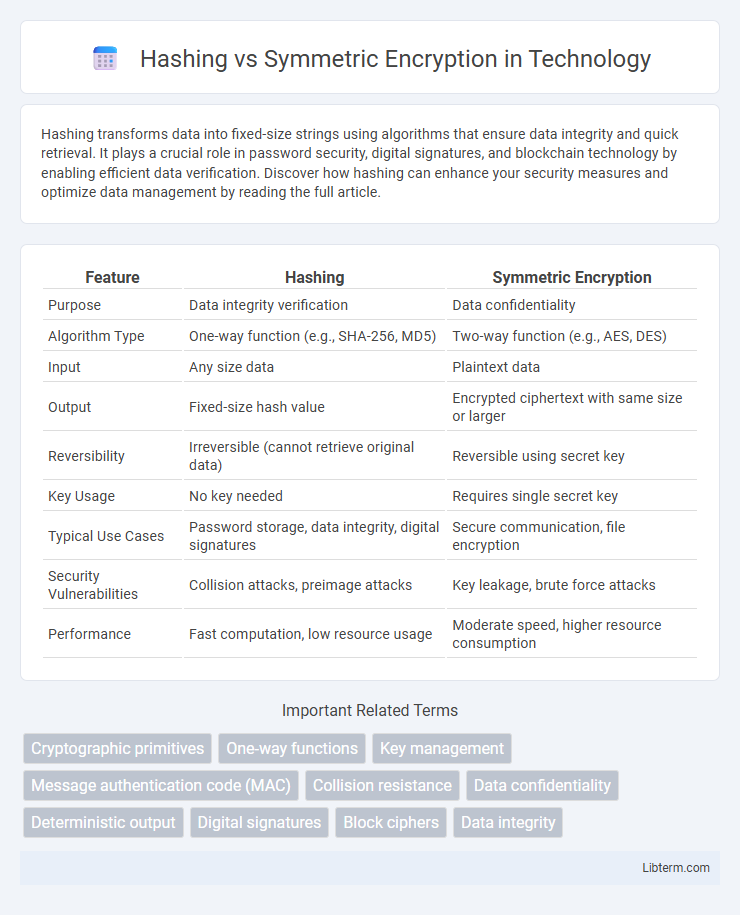
| Feature | Hashing | Symmetric Encryption |
|---|---|---|
| Purpose | Data integrity verification | Data confidentiality |
| Algorithm Type | One-way function (e.g., SHA-256, MD5) | Two-way function (e.g., AES, DES) |
| Input | Any size data | Plaintext data |
| Output | Fixed-size hash value | Encrypted ciphertext with same size or larger |
| Reversibility | Irreversible (cannot retrieve original data) | Reversible using secret key |
| Key Usage | No key needed | Requires single secret key |
| Typical Use Cases | Password storage, data integrity, digital signatures | Secure communication, file encryption |
| Security Vulnerabilities | Collision attacks, preimage attacks | Key leakage, brute force attacks |
| Performance | Fast computation, low resource usage | Moderate speed, higher resource consumption |
Introduction to Data Protection Techniques
Hashing transforms data into a fixed-size string of characters, ensuring data integrity by detecting alterations without revealing the original content. Symmetric encryption uses a single secret key for both encryption and decryption, safeguarding data confidentiality during transmission or storage. Both techniques are fundamental in data protection, with hashing primarily supporting verification processes and symmetric encryption enabling secure communication.
What is Hashing?
Hashing is a cryptographic process that converts input data into a fixed-size string of characters, typically a hash value or digest, which uniquely represents the original information. Unlike symmetric encryption, hashing is a one-way function, making it irreversible and suitable for verifying data integrity and storing passwords securely. Common hashing algorithms include SHA-256, MD5, and SHA-1, which are widely used in data verification and digital signature applications.
What is Symmetric Encryption?
Symmetric encryption is a cryptographic method where the same secret key is used for both encryption and decryption of data, enabling fast and efficient secure communication. It relies on algorithms like AES (Advanced Encryption Standard) and DES (Data Encryption Standard) to transform plaintext into ciphertext, ensuring confidentiality. Unlike hashing, which is one-way and irreversible, symmetric encryption allows the original data to be recovered using the shared secret key.
Core Differences Between Hashing and Symmetric Encryption
Hashing generates a fixed-size string of characters from input data, ensuring data integrity through irreversible transformation, while symmetric encryption uses a single key to both encrypt and decrypt data, preserving confidentiality. Hashing produces a unique digest that cannot be reversed to obtain the original input, whereas symmetric encryption allows recovery of the original plaintext from the ciphertext using the shared secret key. The primary difference lies in hashing being a one-way process for verification and symmetric encryption being a two-way process for secure communication.
Use Cases of Hashing
Hashing is primarily used for data integrity verification, password storage, and digital signatures, ensuring that information remains unchanged and secure. Unlike symmetric encryption, which encrypts and decrypts data using the same key for confidentiality, hashing generates a fixed-size output from variable data, making it ideal for quick data comparison and tamper detection. Common use cases include verifying file integrity during downloads, storing hashed passwords in authentication systems, and enabling blockchain transaction verification.
Use Cases of Symmetric Encryption
Symmetric encryption is widely used for securing large volumes of data due to its efficiency and speed, making it ideal for encrypting files, databases, and communication channels like VPNs and TLS. Common applications include protecting sensitive information in financial transactions, securing data at rest on hard drives and cloud storage, and enabling encrypted messaging in real-time communication apps. Unlike hashing, symmetric encryption allows data to be decrypted and retrieved, supporting confidentiality in scenarios where data recovery is necessary.
Security Considerations for Each Method
Hashing provides data integrity and non-repudiation by generating fixed-size, irreversible digests, ensuring message authenticity without revealing original content, but it does not support data confidentiality. Symmetric encryption secures confidentiality by using a single secret key for both encryption and decryption, making key management and secure key distribution critical to prevent unauthorized access. While hashing resists collision and pre-image attacks, symmetric encryption relies on strong algorithms like AES and proper key length to withstand brute-force and cryptanalysis threats.
Performance and Efficiency Comparison
Hashing algorithms, designed for data integrity verification, typically offer faster processing speeds and lower computational overhead compared to symmetric encryption, which requires complex key management and multiple rounds of transformation for data confidentiality. Symmetric encryption, while generally slower due to encryption and decryption processes, provides reversible data protection essential for secure communication, making its efficiency dependent on the algorithm (e.g., AES) and key size used. Performance in hashing excels in scenarios requiring rapid data verification, whereas symmetric encryption balances speed and security for protecting sensitive information in bulk data transmission.
Common Algorithms in Hashing vs. Symmetric Encryption
Popular hashing algorithms include SHA-256, SHA-3, and MD5, designed for data integrity verification by producing fixed-size hash values from arbitrary input. Symmetric encryption algorithms such as AES (Advanced Encryption Standard), DES (Data Encryption Standard), and ChaCha20 focus on securing data confidentiality by using the same key for both encryption and decryption processes. While hashing algorithms are one-way functions used primarily for integrity checks, symmetric encryption algorithms enable two-way transformations essential for secure communication.
Choosing the Right Technique for Your Needs
Hashing provides a one-way transformation ideal for verifying data integrity and storing passwords securely, while symmetric encryption offers two-way encryption suitable for protecting sensitive data in transit or at rest. Choosing the right technique depends on the goal: use hashing for authentication and integrity checks, and symmetric encryption when data must be decrypted and accessed later. Algorithms like SHA-256 are preferred for hashing, whereas AES remains a widely adopted standard for symmetric encryption due to its balance of security and performance.
Hashing Infographic
 libterm.com
libterm.com