Third-party risk involves potential vulnerabilities that arise when your organization relies on external vendors or service providers. These risks can include data breaches, compliance issues, and operational disruptions that may impact your business continuity and reputation. Explore the rest of the article to learn how to effectively assess and mitigate third-party risk for your organization.
Table of Comparison
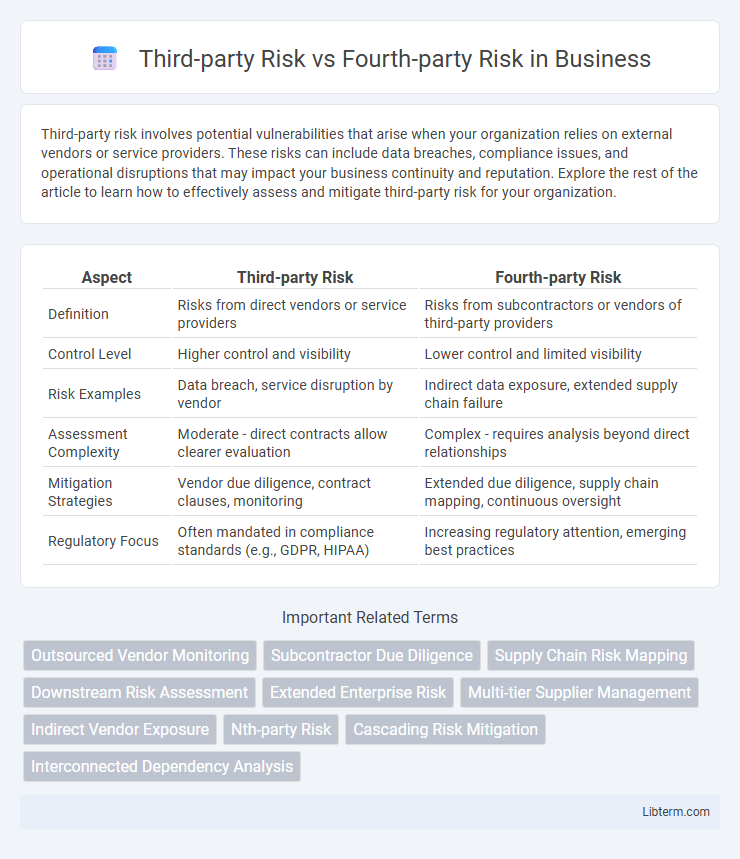
| Aspect | Third-party Risk | Fourth-party Risk |
|---|---|---|
| Definition | Risks from direct vendors or service providers | Risks from subcontractors or vendors of third-party providers |
| Control Level | Higher control and visibility | Lower control and limited visibility |
| Risk Examples | Data breach, service disruption by vendor | Indirect data exposure, extended supply chain failure |
| Assessment Complexity | Moderate - direct contracts allow clearer evaluation | Complex - requires analysis beyond direct relationships |
| Mitigation Strategies | Vendor due diligence, contract clauses, monitoring | Extended due diligence, supply chain mapping, continuous oversight |
| Regulatory Focus | Often mandated in compliance standards (e.g., GDPR, HIPAA) | Increasing regulatory attention, emerging best practices |
Introduction to Third-party and Fourth-party Risks
Third-party risk involves potential threats that arise from direct business relationships with external vendors, suppliers, or service providers, impacting an organization's security and compliance posture. Fourth-party risk extends this exposure by addressing the risks associated with the subcontractors and vendors that third parties rely on, often introducing hidden vulnerabilities beyond the primary vendor's control. Understanding both third-party and fourth-party risks is crucial for comprehensive supply chain risk management and ensuring robust cybersecurity defenses.
Defining Third-party Risk
Third-party risk refers to the potential threats and vulnerabilities an organization faces due to its direct relationships with external vendors, suppliers, or service providers. These risks can include data breaches, operational disruptions, compliance violations, and financial losses originating from third parties' weaknesses or failures. Understanding third-party risk is essential for effective supply chain management and cybersecurity strategies in today's interconnected business environment.
Understanding Fourth-party Risk
Fourth-party risk refers to the vulnerabilities and potential threats posed by an organization's subcontractors or service providers beyond their direct third-party vendors, creating an extended supply chain risk. Understanding fourth-party risk involves mapping these indirect relationships, assessing their cybersecurity posture, and ensuring compliance with regulatory standards to prevent cascading impacts from vulnerabilities in less visible tiers. Effective management requires continuous monitoring, comprehensive due diligence, and integration of advanced risk assessment tools to mitigate exposure throughout the entire supply chain.
Key Differences between Third-party and Fourth-party Risks
Third-party risk involves direct relationships between an organization and its external vendors or suppliers, where risks stem from these immediate partners. Fourth-party risk arises from the vendors or subcontractors that third parties engage, creating an indirect exposure that is often less visible but critical to manage. Key differences include the directness of control and visibility, with third-party risks allowing for more straightforward oversight, while fourth-party risks require extended supply chain risk management and deeper due diligence.
Importance of Identifying All Risk Tiers
Identifying all risk tiers, including third-party and fourth-party risks, is essential for comprehensive supply chain security and operational resilience. Third-party risk involves direct vendors and suppliers, while fourth-party risk extends to subcontractors and service providers of those third parties. Understanding these interconnected risk layers enables businesses to implement effective mitigation strategies and maintain regulatory compliance.
Third-party Risk Management Strategies
Effective third-party risk management strategies involve thorough vendor due diligence, continuous monitoring, and clear contractual agreements to mitigate risks associated with external suppliers. Implementing robust risk assessment frameworks and leveraging technology solutions such as automated risk scoring enhances the identification and control of potential vulnerabilities. Regular audits and integration of third-party risk management within enterprise risk governance ensure proactive mitigation of threats originating from suppliers and service providers.
Fourth-party Risk Monitoring Approaches
Fourth-party risk monitoring involves assessing the cybersecurity and operational risks posed by vendors' subcontractors, which requires comprehensive visibility into the extended supply chain beyond direct suppliers. Effective fourth-party risk management utilizes continuous monitoring tools, automated data integration from multiple sources, and detailed contractual assessments to identify vulnerabilities that could impact the primary organization. Leveraging advanced analytics and real-time risk intelligence platforms enhances the ability to detect, evaluate, and mitigate fourth-party threats proactively.
Challenges in Managing Extended Supply Chain Risks
Managing extended supply chain risks involves complex challenges such as limited visibility beyond third-party vendors, making it difficult to identify and mitigate fourth-party risks effectively. Organizations struggle with the lack of direct control and transparency over fourth-party entities, increasing exposure to cyber threats, compliance issues, and operational disruptions. Ensuring comprehensive risk assessments and continuous monitoring requires advanced tools and collaboration across multiple supply chain tiers to safeguard business continuity and regulatory adherence.
Regulatory Compliance for Third and Fourth-party Risks
Regulatory compliance for third-party risk involves ensuring vendors adhere to data protection laws, industry standards, and contractual obligations to prevent legal penalties and safeguard organizational integrity. Fourth-party risk extends this responsibility by requiring organizations to evaluate the supply chain's subcontractors, ensuring they also comply with relevant regulations such as GDPR, HIPAA, or SOX. Failure to manage both third- and fourth-party risks effectively can result in significant regulatory fines, reputational damage, and operational disruptions.
Future Trends in Risk Management Practices
Future trends in risk management increasingly emphasize the differentiation between third-party and fourth-party risks due to expanding supply chain complexities and digital dependencies. Advanced technologies like AI-driven analytics and blockchain are being integrated to enhance real-time monitoring, predictive risk assessments, and transparency across both third-party vendors and their sub-tier suppliers. Organizations are also adopting comprehensive frameworks that incorporate multi-tier risk evaluations, ensuring a proactive strategy in identifying and mitigating cascading disruptions from fourth-party entities.
Third-party Risk Infographic
 libterm.com
libterm.com