The Resource Owner Password Credentials Grant allows users to provide their username and password directly to an application, which then exchanges these credentials for an access token. This method is suitable for trusted applications but carries higher security risks compared to other OAuth 2.0 flows. Explore the full article to understand when and how to implement this grant safely in your projects.
Table of Comparison
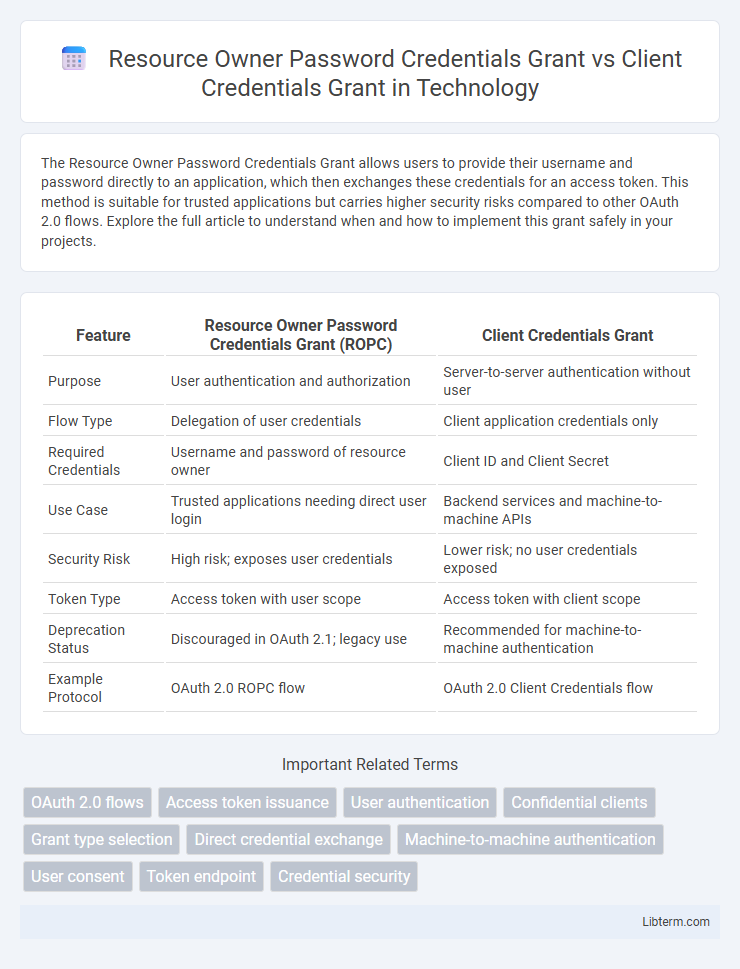
| Feature | Resource Owner Password Credentials Grant (ROPC) | Client Credentials Grant |
|---|---|---|
| Purpose | User authentication and authorization | Server-to-server authentication without user |
| Flow Type | Delegation of user credentials | Client application credentials only |
| Required Credentials | Username and password of resource owner | Client ID and Client Secret |
| Use Case | Trusted applications needing direct user login | Backend services and machine-to-machine APIs |
| Security Risk | High risk; exposes user credentials | Lower risk; no user credentials exposed |
| Token Type | Access token with user scope | Access token with client scope |
| Deprecation Status | Discouraged in OAuth 2.1; legacy use | Recommended for machine-to-machine authentication |
| Example Protocol | OAuth 2.0 ROPC flow | OAuth 2.0 Client Credentials flow |
Introduction to OAuth 2.0 Grant Types
Resource Owner Password Credentials Grant allows users to provide their username and password directly to the client application to obtain an access token, suitable for trusted applications with high-risk considerations. Client Credentials Grant enables machine-to-machine authentication by allowing the client to use its own credentials to request an access token without user involvement, ideal for server-to-server communication. Both grant types serve distinct purposes within OAuth 2.0, balancing security and usability for different authorization scenarios.
What is the Resource Owner Password Credentials Grant?
The Resource Owner Password Credentials Grant is an OAuth 2.0 authorization flow in which the user provides their username and password directly to the client application, enabling the app to obtain an access token on behalf of the user. This grant type is typically used in highly trusted applications where the client can securely handle user credentials, bypassing the need for redirect-based authorization. Unlike the Client Credentials Grant, which issues access tokens based on client authentication without user context, the Resource Owner Password Credentials Grant involves user authentication to access protected resources.
What is the Client Credentials Grant?
The Client Credentials Grant is an OAuth 2.0 authorization flow used for machine-to-machine authentication, where the client application directly authenticates with the authorization server using its own credentials without involving a resource owner. This grant type is ideal for server-to-server interactions, allowing applications to access resources or APIs securely based on their own identity. It is commonly used in scenarios such as backend services, automated processes, and microservices requiring access tokens for resource access without user context.
Key Differences Between Resource Owner Password and Client Credentials Grants
Resource Owner Password Credentials Grant involves the user directly providing their username and password to the client, enabling the client to obtain an access token on behalf of the user, primarily used when the client is highly trusted. In contrast, Client Credentials Grant does not involve user credentials but uses the client's own credentials to request an access token, suitable for machine-to-machine authentication without user context. Key differences include user involvement in authentication, the type of access token issued, and typical use cases--Resource Owner Password is for delegated access with user presence, while Client Credentials is for application-level access.
Use Cases for Resource Owner Password Credentials Grant
Resource Owner Password Credentials Grant is primarily used in highly trusted applications where the client can securely handle user credentials, such as legacy applications or first-party mobile apps requiring direct user authentication. This grant type enables the client to obtain an access token by directly exchanging the user's username and password, facilitating seamless access to resources without redirecting the user to an authorization server. It is not recommended for third-party applications due to security risks, while Client Credentials Grant is more suitable for machine-to-machine communication without user involvement.
Use Cases for Client Credentials Grant
Client Credentials Grant is ideal for server-to-server authentication where no user context is required, such as APIs accessing backend services or microservice communication. It is commonly used in service-to-service scenarios, batch jobs, or automated processes needing access tokens without user interaction. Unlike Resource Owner Password Credentials Grant, Client Credentials Grant does not involve user credentials, ensuring a more secure and streamlined approach for machine-to-machine authentication.
Security Considerations for Both Grant Types
Resource Owner Password Credentials Grant involves direct handling of user credentials, increasing risks related to credential exposure and requiring high trust in the client application, making it less secure for third-party clients. Client Credentials Grant, designed for machine-to-machine authentication, avoids user credentials by relying solely on client authentication, reducing exposure but still needing secure storage of client secrets to prevent unauthorized access. Both grant types demand strict implementation of secure storage, encrypted communication, and regular rotation of secrets to mitigate potential security vulnerabilities.
Advantages and Disadvantages of Each Grant
Resource Owner Password Credentials Grant provides direct user authentication by exchanging username and password for an access token, offering simplicity and quick implementation in trusted applications but risks exposing user credentials and lacks multifactor authentication. Client Credentials Grant enables server-to-server authentication using client ID and secret without user context, ensuring higher security and suitability for backend services but restricts access to resources owned by the client itself and cannot perform actions on behalf of a user. Both grants serve distinct use cases; Resource Owner Password is advantageous for trusted, first-party apps needing user delegation, while Client Credentials excels in secure service-to-service communication without user interaction.
Best Practices for Choosing the Right Grant Type
Resource Owner Password Credentials Grant suits scenarios requiring direct user authentication, typically when the client is highly trusted and the user experience demands immediate access. Client Credentials Grant is ideal for server-to-server interactions where no user context is involved, emphasizing security and simplicity in automated processes. Best practices recommend evaluating the trust level, user involvement, and security requirements to select the appropriate OAuth 2.0 grant type.
Conclusion: Selecting the Optimal OAuth 2.0 Grant
Resource Owner Password Credentials Grant is suitable for trusted applications where user credentials are directly handled, enabling access on behalf of the user with higher risk exposure. Client Credentials Grant is optimal for server-to-server communication, granting access based on the client application's credentials without involving user authentication. Choosing the optimal OAuth 2.0 grant depends on the security context and use case: use Resource Owner Password Credentials for delegated user access in trusted environments and Client Credentials for autonomous service access.
Resource Owner Password Credentials Grant Infographic
 libterm.com
libterm.com