PBKDF2 (Password-Based Key Derivation Function 2) is a cryptographic algorithm designed to securely derive keys from passwords by applying multiple iterations of a hashing function, which significantly increases the resistance against brute-force attacks. It is widely used for hashing passwords in authentication systems, ensuring that your sensitive data remains protected even if the database is compromised. Explore the rest of the article to understand how PBKDF2 strengthens security and how to implement it effectively.
Table of Comparison
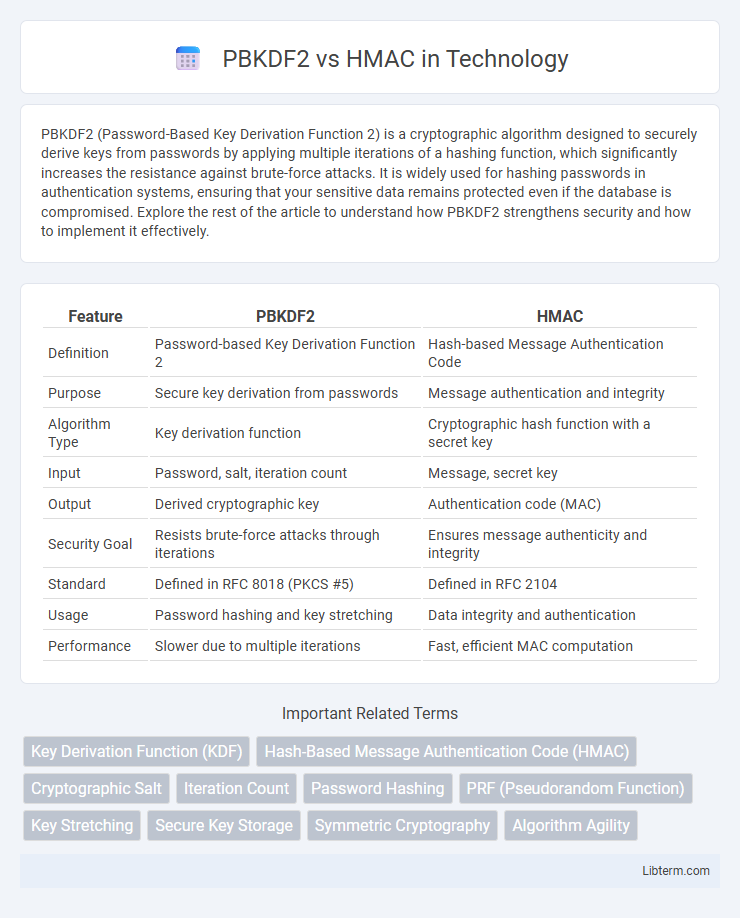
| Feature | PBKDF2 | HMAC |
|---|---|---|
| Definition | Password-based Key Derivation Function 2 | Hash-based Message Authentication Code |
| Purpose | Secure key derivation from passwords | Message authentication and integrity |
| Algorithm Type | Key derivation function | Cryptographic hash function with a secret key |
| Input | Password, salt, iteration count | Message, secret key |
| Output | Derived cryptographic key | Authentication code (MAC) |
| Security Goal | Resists brute-force attacks through iterations | Ensures message authenticity and integrity |
| Standard | Defined in RFC 8018 (PKCS #5) | Defined in RFC 2104 |
| Usage | Password hashing and key stretching | Data integrity and authentication |
| Performance | Slower due to multiple iterations | Fast, efficient MAC computation |
Introduction to PBKDF2 and HMAC
PBKDF2 (Password-Based Key Derivation Function 2) is a cryptographic algorithm designed to securely derive keys from passwords by applying a pseudorandom function, such as HMAC, repeatedly to resist brute-force attacks. HMAC (Hash-based Message Authentication Code) is a specific construction for creating a message authentication code using a cryptographic hash function combined with a secret key, ensuring data integrity and authenticity. PBKDF2 leverages HMAC's hashing mechanism iteratively to enhance password security through computational work factors and salting.
Understanding the Basics: What is PBKDF2?
PBKDF2 (Password-Based Key Derivation Function 2) is a key derivation function designed to strengthen weak passwords by applying a pseudorandom function, such as HMAC, repeatedly to produce a cryptographic key. PBKDF2 uses HMAC as its underlying pseudorandom function to generate derived keys with increased computational cost, enhancing resistance against brute-force attacks. This process ensures secure storage and usage of passwords in cryptographic applications by increasing the effort required to guess the original password.
What is HMAC? Key Concepts and Functions
HMAC (Hash-based Message Authentication Code) is a cryptographic algorithm that combines a cryptographic hash function with a secret key to provide data integrity and authentication. It operates by hashing the concatenation of the key and the message, ensuring that any change in the message or key results in a different hash output, which verifies authenticity. HMAC is widely used in various security protocols, including TLS and IPsec, for ensuring message integrity and authenticity without exposing the secret key.
Core Differences Between PBKDF2 and HMAC
PBKDF2 (Password-Based Key Derivation Function 2) is a key derivation function designed to securely generate cryptographic keys from passwords by applying a pseudorandom function, typically HMAC, in multiple iterations to increase computational workload. HMAC (Hash-based Message Authentication Code) is a specific construction for creating a message authentication code using a cryptographic hash function and a secret key to ensure data integrity and authenticity. The core difference lies in PBKDF2 using HMAC as a building block to derive keys with resistance to brute-force attacks, while HMAC independently serves as a mechanism for verifying message integrity and authenticity.
Use Cases: When to Use PBKDF2 vs HMAC
PBKDF2 is ideal for securely hashing passwords and generating cryptographic keys by applying multiple iterations to slow down brute-force attacks, making it suitable for password storage and key derivation in authentication systems. HMAC, on the other hand, provides message integrity and authentication by combining a cryptographic hash function with a secret key, making it optimal for verifying data integrity in protocols like TLS and API authentication. Use PBKDF2 when protecting sensitive credentials or generating keys; use HMAC for ensuring message authenticity and integrity in secure communications.
Security Strengths and Weaknesses Compared
PBKDF2 utilizes HMAC as its underlying pseudorandom function, combining multiple iterations to strengthen password hashing against brute-force attacks, while HMAC alone provides message integrity and authentication but is not designed for password hashing complexity. PBKDF2's security strength lies in its configurable iteration count, increasing computational cost and slowing down attackers, but it may be vulnerable to GPU-accelerated brute-force attacks if iteration parameters are too low. HMAC offers robust resistance to cryptographic attacks such as collision and length-extension, yet without key stretching, it lacks protection against offline dictionary attacks on passwords, making it less suitable than PBKDF2 for password hashing scenarios.
Performance and Efficiency Analysis
PBKDF2 relies on HMAC as its underlying pseudorandom function, combining iterative hashing to slow down brute-force attacks, which impacts its performance relative to raw HMAC. HMAC provides faster computation as a message authentication code, optimized for integrity verification rather than key derivation. In performance-critical applications, HMAC executes efficiently with lower CPU usage, while PBKDF2 trades speed for enhanced security through adjustable iteration counts, making it less efficient but more resilient against attacks.
Implementation Considerations
Implementing PBKDF2 requires careful selection of iteration count and salt length to balance security and performance, as it uses HMAC internally with a pseudorandom function for key stretching. HMAC implementation focuses on ensuring a constant-time calculation to prevent timing attacks, along with proper key management to maintain integrity and authentication. Both need optimized use of cryptographic libraries and hardware acceleration where possible to improve efficiency and resistance to side-channel attacks.
Best Practices for Secure Cryptographic Applications
PBKDF2 (Password-Based Key Derivation Function 2) is designed specifically for securely hashing passwords by incorporating a salt and multiple iterations to slow down brute-force attacks, whereas HMAC (Hash-based Message Authentication Code) provides data integrity and authentication but is not suitable alone for password hashing. Best practices for secure cryptographic applications recommend using PBKDF2 with a sufficiently high iteration count (e.g., 100,000+) and unique salts to protect stored passwords from rainbow table and brute-force attacks. Employing HMAC alongside PBKDF2 can enhance overall message integrity and authentication but should never replace dedicated password hashing functions in password storage scenarios.
Conclusion: PBKDF2 or HMAC – Which Should You Choose?
PBKDF2 and HMAC serve distinct cryptographic purposes: PBKDF2 is a key derivation function designed to securely hash passwords with configurable iterations and salt, while HMAC is a message authentication code used to verify data integrity and authenticity. Choose PBKDF2 when protecting passwords or generating cryptographic keys from passphrases, as its design mitigates brute-force attacks through computational cost. Opt for HMAC in scenarios requiring data integrity verification and authentication, leveraging its reliance on secure hash functions like SHA-256 for tamper-proof message validation.
PBKDF2 Infographic
 libterm.com
libterm.com