SHA-256 is a cryptographic hash function that generates a fixed 256-bit hash value from any input data, ensuring data integrity and security. It is widely used in blockchain technology, digital signatures, and password hashing to protect sensitive information against tampering. Discover how SHA-256 can enhance your cybersecurity measures by exploring the details in the rest of this article.
Table of Comparison
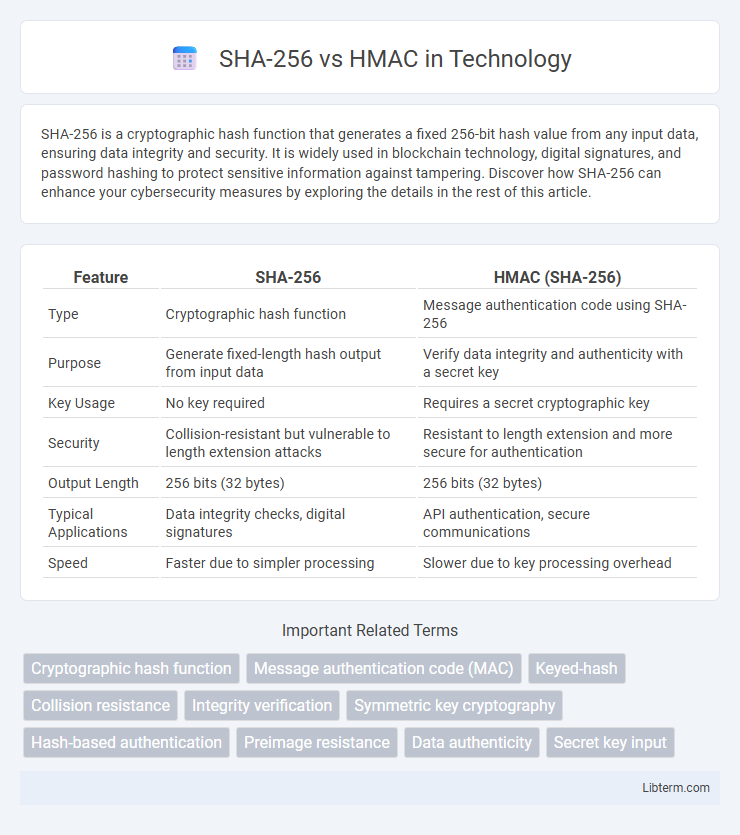
| Feature | SHA-256 | HMAC (SHA-256) |
|---|---|---|
| Type | Cryptographic hash function | Message authentication code using SHA-256 |
| Purpose | Generate fixed-length hash output from input data | Verify data integrity and authenticity with a secret key |
| Key Usage | No key required | Requires a secret cryptographic key |
| Security | Collision-resistant but vulnerable to length extension attacks | Resistant to length extension and more secure for authentication |
| Output Length | 256 bits (32 bytes) | 256 bits (32 bytes) |
| Typical Applications | Data integrity checks, digital signatures | API authentication, secure communications |
| Speed | Faster due to simpler processing | Slower due to key processing overhead |
Introduction to SHA-256 and HMAC
SHA-256 is a cryptographic hash function producing a fixed 256-bit output from arbitrary input data, widely used for data integrity and security verification. HMAC (Hash-based Message Authentication Code) combines a cryptographic hash function like SHA-256 with a secret key, providing both data integrity and authentication in message exchanges. The key difference lies in HMAC's use of a secret key, which enhances security by protecting against tampering and impersonation, unlike the standalone SHA-256 hash.
Understanding SHA-256: Core Principles
SHA-256, a member of the SHA-2 family, operates through a series of logical functions, bitwise operations, and modular additions to produce a fixed 256-bit hash value from variable-length input data. Its core principles include pre-processing steps like padding and parsing the message into 512-bit blocks, followed by iterative compression functions that ensure collision resistance and preimage resistance. Unlike HMAC, which combines a secret key with SHA-256 for message authentication, SHA-256 alone is primarily designed for data integrity and cryptographic hashing without built-in keying mechanisms.
HMAC: Definition and Purpose
HMAC (Hash-based Message Authentication Code) is a cryptographic technique that combines a cryptographic hash function, such as SHA-256, with a secret key to provide message integrity and authentication. Unlike SHA-256, which is a standalone hashing algorithm producing fixed-size outputs, HMAC uses the hash function within a specific construction that prevents forgery and ensures that only parties with the secret key can generate or verify the MAC. The primary purpose of HMAC is to authenticate the origin and integrity of a message, making it essential in secure communications and data integrity verification.
Key Differences Between SHA-256 and HMAC
SHA-256 is a cryptographic hash function producing a fixed 256-bit output from any input, primarily used for data integrity verification. HMAC (Hash-based Message Authentication Code) incorporates a secret key with a hash function like SHA-256 to provide both data integrity and authentication, ensuring the message originates from a verified sender. The key difference lies in SHA-256 being solely a hashing algorithm, while HMAC combines hashing with a secret key for enhanced security against tampering and forgery.
Cryptographic Strength: SHA-256 vs HMAC
SHA-256 is a cryptographic hash function that produces a fixed 256-bit output, offering collision resistance and preimage resistance essential for data integrity. HMAC (Hash-based Message Authentication Code) combines SHA-256 with a secret key to provide enhanced cryptographic strength, including message authenticity and integrity, protecting against length-extension and replay attacks. While SHA-256 alone ensures data fingerprinting, HMAC with SHA-256 secures communication channels by verifying both data integrity and origin authentication.
Use Cases: When to Use SHA-256 or HMAC
SHA-256 is ideal for generating fixed-size cryptographic hashes in applications like data integrity verification and digital signatures where data authenticity isn't a concern. HMAC, combining SHA-256 with a secret key, is best suited for message authentication in secure communication protocols such as TLS, ensuring both data integrity and authenticity. Use SHA-256 for simple fingerprinting, while HMAC is essential in scenarios requiring protection against tampering and replay attacks.
Implementation Examples of SHA-256 and HMAC
SHA-256 is a cryptographic hash function that produces a fixed 256-bit hash value from input data, commonly implemented using libraries like OpenSSL or hashlib in Python with simple function calls such as `hashlib.sha256(data).hexdigest()`. HMAC (Hash-based Message Authentication Code) uses a secret key combined with SHA-256 to provide data integrity and authentication, typically implemented with code like `hmac.new(key, message, hashlib.sha256).hexdigest()` in Python. Both implementations emphasize secure handling of inputs and keys, with SHA-256 alone suited for hashing and HMAC designed for verifying message authenticity.
Performance Comparison: SHA-256 vs HMAC
SHA-256 is a cryptographic hash function that processes data quickly with a fixed 256-bit output, providing high-speed performance for data integrity checks. HMAC, which combines SHA-256 with a secret key, introduces additional computational steps for enhanced security, resulting in slightly higher latency than raw SHA-256. Performance benchmarks typically show SHA-256 executing faster due to its simpler structure, while HMAC prioritizes authentication strength over raw throughput.
Security Vulnerabilities and Risks
SHA-256 is a cryptographic hash function vulnerable to length extension attacks, making it unsuitable for standalone authentication. HMAC combines SHA-256 with a secret key to mitigate these risks, providing robust protection against collision and preimage attacks. Despite HMAC's resilience, improper key management or reuse can still expose systems to security vulnerabilities.
Conclusion: Choosing the Right Algorithm
SHA-256 provides a robust cryptographic hash function ideal for data integrity verification, while HMAC combines SHA-256 with a secret key to deliver enhanced authentication and message integrity. Selecting between SHA-256 and HMAC depends on whether the primary goal is simple hashing or secure key-based authentication. For applications requiring verification against tampering and unauthorized access, HMAC with SHA-256 is the optimal choice.
SHA-256 Infographic
 libterm.com
libterm.com