Buffer overflow occurs when a program writes more data to a buffer than it can hold, leading to memory corruption and potential security vulnerabilities. Exploiting this flaw, attackers can execute malicious code, causing system crashes or unauthorized access. Discover how understanding buffer overflow can strengthen your cybersecurity measures by reading the rest of the article.
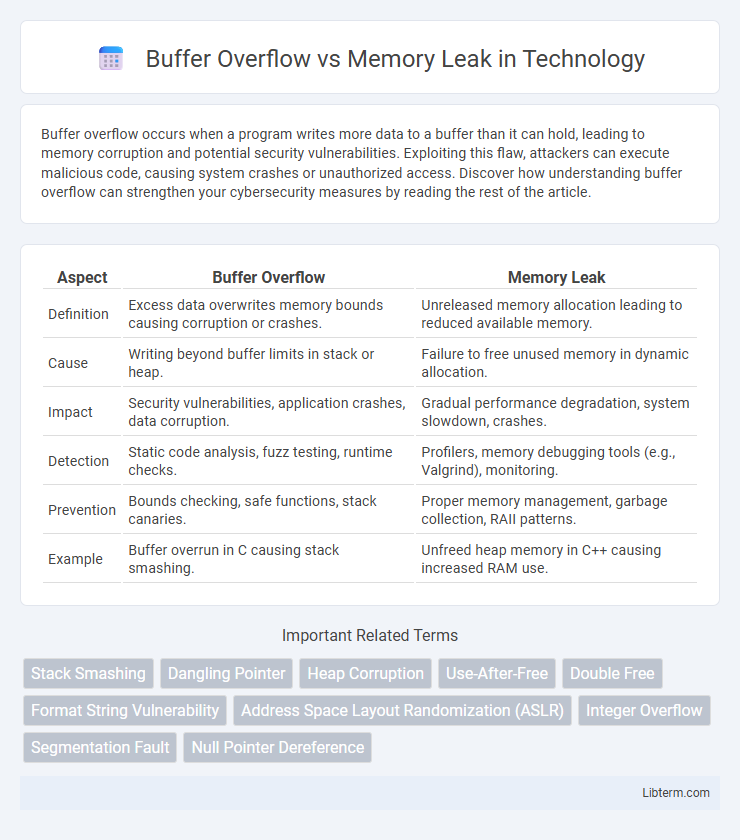
Table of Comparison
| Aspect | Buffer Overflow | Memory Leak |
|---|---|---|
| Definition | Excess data overwrites memory bounds causing corruption or crashes. | Unreleased memory allocation leading to reduced available memory. |
| Cause | Writing beyond buffer limits in stack or heap. | Failure to free unused memory in dynamic allocation. |
| Impact | Security vulnerabilities, application crashes, data corruption. | Gradual performance degradation, system slowdown, crashes. |
| Detection | Static code analysis, fuzz testing, runtime checks. | Profilers, memory debugging tools (e.g., Valgrind), monitoring. |
| Prevention | Bounds checking, safe functions, stack canaries. | Proper memory management, garbage collection, RAII patterns. |
| Example | Buffer overrun in C causing stack smashing. | Unfreed heap memory in C++ causing increased RAM use. |
Introduction to Buffer Overflow and Memory Leak
Buffer overflow occurs when a program writes more data to a buffer than it can hold, causing adjacent memory to be overwritten and leading to potential crashes or security vulnerabilities. Memory leak happens when a program allocates memory but fails to release it back to the system, resulting in reduced available memory and degraded performance over time. Both issues impact program stability, with buffer overflow primarily causing immediate faults and memory leaks causing gradual resource exhaustion.
Understanding Buffer Overflow
Buffer overflow occurs when a program writes more data to a buffer than it can hold, causing adjacent memory to be overwritten and potentially leading to crashes or security vulnerabilities. This flaw often arises from improper input validation or unsafe memory operations in languages like C and C++. Understanding buffer overflow is crucial for secure coding practices and preventing exploits such as code injection or denial of service.
Exploring Memory Leak
Memory leaks occur when a program allocates memory but fails to release it after use, gradually exhausting available resources and causing degraded system performance or crashes. Unlike buffer overflow, which involves writing data beyond allocated memory boundaries leading to potential security vulnerabilities, memory leaks primarily result in inefficient memory utilization and application slowdown. Detecting memory leaks involves monitoring memory usage patterns, using tools like Valgrind or AddressSanitizer to identify unreleased memory blocks during program execution.
Causes of Buffer Overflow
Buffer overflow occurs when a program writes more data to a buffer than it can hold, exceeding its allocated memory space. Common causes include improper input validation, lack of boundary checking, and vulnerable functions like strcpy and gets that do not enforce size limits. This leads to overwriting adjacent memory, which can cause crashes, data corruption, or exploitation by attackers.
Causes of Memory Leak
Memory leaks occur primarily due to improper management of dynamic memory allocation where allocated memory is not released after use, typically caused by missing deallocation commands like free() or delete in languages such as C and C++. Retaining references to unused objects in languages with garbage collection, like Java or Python, prevents reclaiming memory, leading to leaks. Repeatedly allocating memory in loops or recursive functions without corresponding deallocations further exacerbates memory leak issues.
Key Differences Between Buffer Overflow and Memory Leak
Buffer overflow occurs when a program writes more data to a buffer than it can hold, leading to adjacent memory corruption and potential security vulnerabilities, while a memory leak involves the failure to release allocated memory, causing increased memory consumption and degraded system performance. Buffer overflows typically result from improper input validation and can allow code execution exploits, whereas memory leaks stem from programming errors where allocated memory is not freed, leading to resource exhaustion. Understanding these distinct issues is critical for secure coding and efficient memory management in software development.
Security Implications of Buffer Overflow
Buffer overflow vulnerabilities enable attackers to overwrite adjacent memory, potentially injecting malicious code and executing arbitrary commands, which compromises system integrity and confidentiality. Such exploits can lead to privilege escalation, unauthorized access, and denial-of-service attacks, posing critical risks to software security and user data protection. In contrast, memory leaks degrade system performance over time but typically do not allow direct code execution or immediate security breaches.
Impact of Memory Leak on Performance
Memory leaks degrade system performance by continually consuming available RAM, leading to increased memory usage and eventual exhaustion of resources, which can cause applications to slow down or crash. The unfreed memory fragments reduce the efficiency of the memory allocator, causing fragmentation that hampers optimal memory utilization. Over time, unresolved memory leaks escalate latency, decrease throughput, and may require system restarts to recover, significantly impacting overall application stability and user experience.
Prevention and Mitigation Techniques
Buffer overflow prevention techniques include bounds checking, using safe functions like strncpy instead of strcpy, and implementing stack canaries and address space layout randomization (ASLR) to protect memory regions. Memory leak mitigation relies on proper resource management through manual deallocation, automatic garbage collection, and employing tools like Valgrind or AddressSanitizer to detect leaks during development. Both vulnerabilities benefit from secure coding practices, rigorous code reviews, and continuous monitoring to identify and rectify issues early in the software lifecycle.
Conclusion: Choosing Robust Coding Practices
Buffer overflow and memory leak represent critical security and performance vulnerabilities in software development, demanding vigilant attention to memory management. Adopting robust coding practices such as bounds checking, using safe libraries, and implementing automatic memory management can effectively mitigate these risks. Prioritizing secure coding standards not only enhances application stability but also protects against exploitation and resource exhaustion.
Buffer Overflow Infographic
 libterm.com
libterm.com