A sandbox environment allows developers and testers to experiment with software in a risk-free setting, preventing any impact on live systems. This controlled space fosters innovation by isolating changes and debugging processes, ensuring your applications run smoothly when deployed. Explore the rest of the article to discover how sandboxing can enhance your development workflow and security.
Table of Comparison
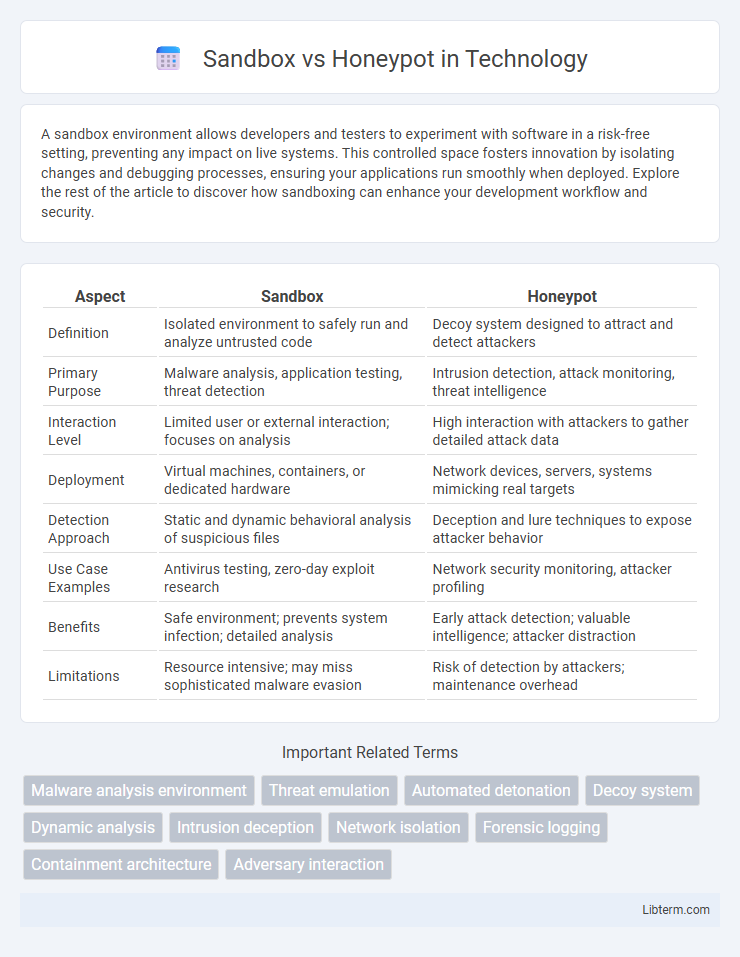
| Aspect | Sandbox | Honeypot |
|---|---|---|
| Definition | Isolated environment to safely run and analyze untrusted code | Decoy system designed to attract and detect attackers |
| Primary Purpose | Malware analysis, application testing, threat detection | Intrusion detection, attack monitoring, threat intelligence |
| Interaction Level | Limited user or external interaction; focuses on analysis | High interaction with attackers to gather detailed attack data |
| Deployment | Virtual machines, containers, or dedicated hardware | Network devices, servers, systems mimicking real targets |
| Detection Approach | Static and dynamic behavioral analysis of suspicious files | Deception and lure techniques to expose attacker behavior |
| Use Case Examples | Antivirus testing, zero-day exploit research | Network security monitoring, attacker profiling |
| Benefits | Safe environment; prevents system infection; detailed analysis | Early attack detection; valuable intelligence; attacker distraction |
| Limitations | Resource intensive; may miss sophisticated malware evasion | Risk of detection by attackers; maintenance overhead |
Introduction to Sandbox and Honeypot Technologies
Sandbox technology isolates suspicious files or programs in a controlled, secure environment to analyze behavior without risking the host system, enhancing malware detection and prevention. Honeypot systems act as decoy targets to attract attackers, capturing intrusion attempts and gathering intelligence on threat vectors to improve cybersecurity defenses. Both technologies play crucial roles in proactive threat analysis and network security monitoring.
Defining Sandboxes: Purpose and Functionality
Sandboxes serve as isolated environments designed to safely execute, analyze, and test untrusted code or applications without risking the host system or network integrity. Their primary purpose is to detect malware behavior and vulnerabilities by closely monitoring program activities in a controlled setting, enabling security professionals to understand threats before deployment. Unlike honeypots, which aim to attract and capture attackers by masquerading as vulnerable targets, sandboxes focus on containment and behavior analysis of suspicious software.
Understanding Honeypots: Types and Objectives
Honeypots are cybersecurity tools designed to detect, deflect, or study unauthorized access by mimicking real systems to attract attackers. They come in various types, including production honeypots focused on diverting threats away from critical assets and research honeypots aimed at gathering intelligence on attack methods and behavior. The primary objectives of honeypots involve early threat detection, attack analysis, and gaining insights to improve overall security defenses.
Key Differences Between Sandboxes and Honeypots
Sandboxes isolate suspicious files or code in a controlled environment to analyze behavior without risking system security, while honeypots lure attackers by mimicking vulnerable systems to detect and study intrusion attempts. Sandboxes are primarily used for malware analysis and behavior monitoring, whereas honeypots focus on threat intelligence and attacker profiling. The key difference lies in sandbox environments being preventive and analytical, while honeypots are deceptive tools designed to attract and monitor real attacker activity.
Use Cases: When to Implement a Sandbox
Sandboxes are ideal for safely analyzing unknown or suspicious files and software in an isolated environment to detect malware behavior without risking production systems. They are implemented in advanced threat detection scenarios where dynamic analysis reveals zero-day exploits and polymorphic malware characteristics. Organizations prioritize sandboxes for automated, large-scale threat intelligence collection and forensic investigations of potentially malicious code.
Use Cases: When to Deploy a Honeypot
Honeypots are ideal for detecting and analyzing sophisticated cyber threats by mimicking real systems to attract attackers and gather intelligence on their methods. Deploying a honeypot is effective in environments where proactive threat detection and attacker behavior research are essential, such as enterprise networks or critical infrastructure systems. Unlike sandboxes, which focus on analyzing individual files or malware execution in isolation, honeypots provide ongoing monitoring of attacker interactions within a controlled environment.
Benefits of Using Sandboxes in Cybersecurity
Sandboxes provide a controlled environment to safely analyze and detect malicious software behavior without risking system integrity, enabling rapid identification of zero-day threats. By isolating suspicious code execution, sandboxes prevent malware from spreading, improving overall threat containment and response efficiency. This proactive approach enhances cybersecurity defenses by allowing detailed behavioral analysis and automated threat mitigation before attacks impact critical infrastructure.
Advantages of Incorporating Honeypots
Incorporating honeypots enhances cybersecurity by providing early detection of novel and targeted cyber threats, allowing organizations to gather critical intelligence on attacker techniques without risking critical systems. Honeypots reduce false positives by isolating adversary activity within a controlled environment, which improves incident response accuracy and efficiency. They also serve as a proactive defense mechanism by diverting attackers away from valuable assets, buying time for cybersecurity teams to analyze threats and strengthen network defenses.
Challenges and Limitations of Each Approach
Sandbox environments face challenges such as limited visibility into sophisticated malware behaviors that detect virtualization, and resource-intensive analysis that can slow down system performance. Honeypots struggle with attracting realistic threat activity without exposing legitimate systems to risk, often resulting in limited data that may not represent widespread attack patterns. Both approaches require continual updates to effectively identify evolving threats and avoid evasion tactics by advanced adversaries.
Choosing the Right Solution: Sandbox, Honeypot, or Both?
Selecting the ideal cybersecurity approach depends on organizational goals: sandboxes analyze suspicious files or code in isolated environments for threat detection, while honeypots attract attackers to study their methods and gather intelligence. Enterprises targeting real-time malware analysis and behavior profiling benefit from sandboxes, whereas those aiming to gather extensive attacker data and improve intrusion detection leverage honeypots. Combining both solutions enhances defense-in-depth strategies by providing comprehensive threat visibility and proactive incident response capabilities.
Sandbox Infographic
 libterm.com
libterm.com