Deterministic systems operate under fixed rules, producing predictable and consistent outcomes every time given the same initial conditions. Understanding deterministic processes is crucial for fields like computer science, physics, and engineering, where precise control and replication are essential. Dive into the rest of the article to explore how deterministic principles impact various technologies and your daily life.
Table of Comparison
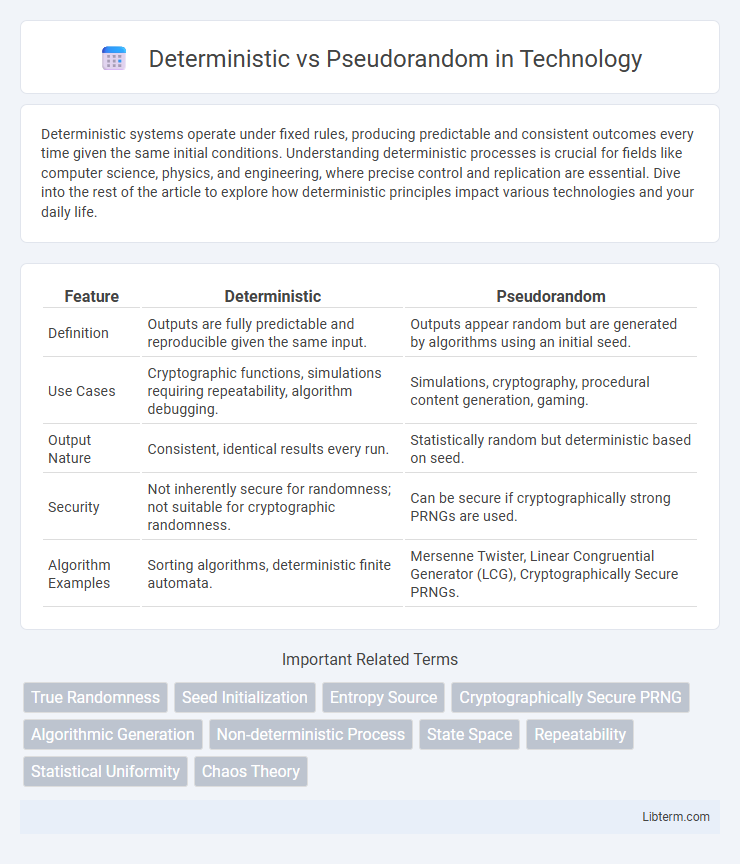
| Feature | Deterministic | Pseudorandom |
|---|---|---|
| Definition | Outputs are fully predictable and reproducible given the same input. | Outputs appear random but are generated by algorithms using an initial seed. |
| Use Cases | Cryptographic functions, simulations requiring repeatability, algorithm debugging. | Simulations, cryptography, procedural content generation, gaming. |
| Output Nature | Consistent, identical results every run. | Statistically random but deterministic based on seed. |
| Security | Not inherently secure for randomness; not suitable for cryptographic randomness. | Can be secure if cryptographically strong PRNGs are used. |
| Algorithm Examples | Sorting algorithms, deterministic finite automata. | Mersenne Twister, Linear Congruential Generator (LCG), Cryptographically Secure PRNGs. |
Understanding Deterministic Systems
Deterministic systems operate under fixed rules that produce the same output from identical initial conditions, ensuring predictable and reproducible results. In contrast, pseudorandom processes generate sequences that appear random but are ultimately derived from deterministic algorithms, relying on initial seeds for their variability. Understanding deterministic systems is crucial for applications in cryptography, simulations, and algorithm design where consistency and traceability are paramount.
Defining Pseudorandom Processes
Pseudorandom processes generate sequences that mimic true randomness through deterministic algorithms, ensuring reproducibility and predictability when the initial seed is known. Unlike genuinely random processes driven by physical or environmental noise, pseudorandom sequences are entirely defined by their initial conditions, making them essential in simulations, cryptography, and randomized algorithms. These processes balance the need for randomness with computational efficiency, enabling controlled manipulation of seemingly unpredictable data.
Key Differences Between Deterministic and Pseudorandom
Deterministic processes generate outputs that are entirely predictable and repeatable with the same initial conditions, while pseudorandom processes produce sequences that appear random but are generated by deterministic algorithms using an initial seed value. Deterministic algorithms have no inherent randomness, enabling exact replication, whereas pseudorandom number generators (PRNGs) simulate randomness for applications like cryptography and simulations but rely on complex algorithms to maintain unpredictability. The key difference lies in predictability and reproducibility--deterministic outputs are fully predictable, whereas pseudorandom outputs balance unpredictability with deterministic generation methods.
Applications of Deterministic Algorithms
Deterministic algorithms are essential in applications requiring predictable and reproducible results, such as cryptographic key generation, error detection and correction, and sorting algorithms in computer science. These algorithms provide consistent output for the same input, ensuring reliability in automated decision-making systems and real-time processing environments. Industries like finance, aerospace, and software development rely heavily on deterministic processes to maintain accuracy and stability in their critical operations.
Real-World Use Cases for Pseudorandom Methods
Pseudorandom methods are essential in real-world applications such as cryptography, where secure key generation depends on unpredictable yet reproducible sequences to ensure data protection. In simulations and gaming, pseudorandom number generators enable realistic randomness while allowing reproducibility for debugging and fairness. Additionally, machine learning algorithms utilize pseudorandom initialization to optimize model training and improve accuracy across diverse datasets.
Security Implications: Deterministic vs Pseudorandom
Deterministic algorithms generate predictable outputs from given inputs, making them vulnerable to pattern analysis and replay attacks in security contexts. Pseudorandom generators produce sequences that mimic true randomness, enhancing cryptographic strength by resisting prediction and improving key generation. The security of cryptographic systems heavily depends on the unpredictability of pseudorandom number generators to prevent vulnerabilities exploited through deterministic behavior.
Predictability and Reproducibility in Both Approaches
Deterministic algorithms produce predictable and reproducible outputs by following strict, predefined rules, ensuring the same input always yields the same result. Pseudorandom generators use deterministic processes with initial seeds, making their outputs appear random yet remain reproducible and predictable if the seed is known. True randomness lacks predictability and reproducibility, but pseudorandomness balances randomness with algorithmic control, essential for simulations and cryptographic applications.
Performance and Efficiency Comparison
Deterministic algorithms provide consistent and repeatable outputs with minimal computational overhead, making them highly efficient for performance-critical applications where predictability is essential. Pseudorandom algorithms generate sequences that appear random but rely on deterministic processes, often requiring more CPU cycles and memory due to complex state management and initialization, which can reduce efficiency under high-load conditions. In performance-sensitive environments, deterministic methods excel in speed and resource usage, while pseudorandom methods balance randomness quality with a moderate performance cost.
Challenges in Differentiating Deterministic and Pseudorandom
Distinguishing deterministic sequences from pseudorandom ones presents challenges due to their similar statistical properties and unpredictability in short samples. Cryptographic algorithms and complexity theory tools are essential for identifying underlying patterns that reveal determinism in ostensibly random data. Ensuring effective differentiation requires advanced mathematical models and rigorous testing to detect subtle algorithmic structures masked by pseudorandomness.
Future Trends in Deterministic and Pseudorandom Research
Future trends in deterministic and pseudorandom research emphasize enhancing algorithmic efficiency and security for cryptographic applications. Advances in quantum computing challenge existing pseudorandom number generators, driving developments in quantum-resistant deterministic algorithms. Integration of machine learning techniques aims to optimize randomness quality and predictability control in both deterministic and pseudorandom systems.
Deterministic Infographic
 libterm.com
libterm.com