A trap account is a security measure designed to detect unauthorized access by enticing attackers with seemingly valuable but fake information. It helps in identifying breach attempts and monitoring malicious activity without compromising real data. Discover how a trap account can enhance Your cybersecurity strategy by reading the full article.
Table of Comparison
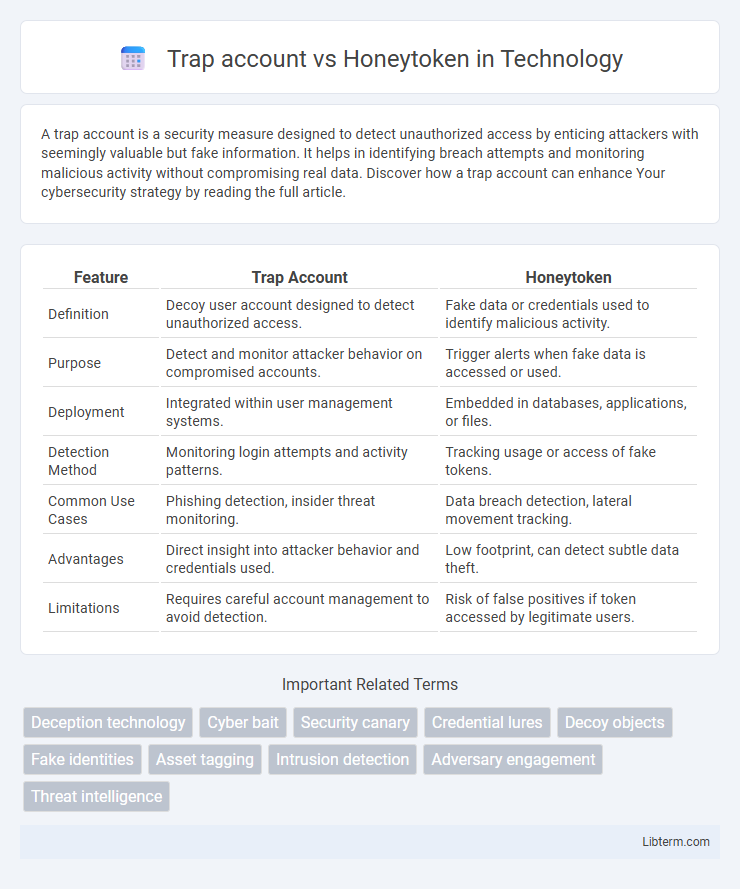
| Feature | Trap Account | Honeytoken |
|---|---|---|
| Definition | Decoy user account designed to detect unauthorized access. | Fake data or credentials used to identify malicious activity. |
| Purpose | Detect and monitor attacker behavior on compromised accounts. | Trigger alerts when fake data is accessed or used. |
| Deployment | Integrated within user management systems. | Embedded in databases, applications, or files. |
| Detection Method | Monitoring login attempts and activity patterns. | Tracking usage or access of fake tokens. |
| Common Use Cases | Phishing detection, insider threat monitoring. | Data breach detection, lateral movement tracking. |
| Advantages | Direct insight into attacker behavior and credentials used. | Low footprint, can detect subtle data theft. |
| Limitations | Requires careful account management to avoid detection. | Risk of false positives if token accessed by legitimate users. |
Introduction to Trap Accounts and Honeytokens
Trap accounts are decoy user profiles created within a system to detect unauthorized access or insider threats by monitoring suspicious login attempts and activities. Honeytokens are strategically crafted pieces of data or credentials, such as fake database entries or API keys, designed to alert security teams when accessed or exfiltrated, serving as early warning signals of a breach. Both technologies serve as proactive cybersecurity measures to identify attacker behavior and protect sensitive information.
Defining Trap Accounts: Key Concepts
Trap accounts are decoy user profiles created to attract and detect unauthorized access within a system by mimicking legitimate accounts with attractive credentials or permissions. These accounts act as early warning systems, alerting security teams to malicious activity when accessed or manipulated, without granting actual access to sensitive data. Unlike honeytokens, which are digital breadcrumbs like fake database entries or documents, trap accounts are complete user identities designed to engage and trap intruders.
Understanding Honeytokens: What They Are
Honeytokens are deceptive data artifacts designed to lure attackers by mimicking sensitive information such as fake credentials, documents, or database entries within a network. Unlike trap accounts, which are specific user accounts set up to detect unauthorized access, honeytokens function as digital breadcrumbs that trigger alerts when accessed or used, enabling early detection of security breaches. These strategically planted tokens enhance threat intelligence by providing actionable insights into attacker behavior and method without impacting legitimate system operations.
Core Differences Between Trap Accounts and Honeytokens
Trap accounts are decoy user profiles designed to lure attackers and monitor unauthorized access within a network, while honeytokens are deceptive data elements such as fake credentials or files embedded in systems to detect malicious activity. Trap accounts mimic legitimate user behavior, aiming to catch credential thieves or insider threats, whereas honeytokens trigger alerts upon unauthorized usage, providing early warning without requiring interaction with a real account. The core difference lies in trap accounts being fully functional, monitored identities, compared to honeytokens as passive data artifacts that signal compromise when accessed.
Use Cases for Trap Accounts in Cybersecurity
Trap accounts serve as cybersecurity tools designed to detect unauthorized access by mimicking real user profiles within a system. These accounts are strategically deployed in sensitive environments to identify insider threats, monitor malicious activity, and trigger alerts when accessed, providing early warnings of potential breaches. Unlike honeytokens, which are data artifacts, trap accounts leverage user authentication mechanisms to engage attackers and gather intelligence on attacker behavior.
Common Applications of Honeytokens in Security
Honeytokens are strategically deployed within systems to detect unauthorized access by mimicking valuable data such as fake credentials, API keys, or network routes, thereby alerting security teams to potential breaches. Unlike traditional trap accounts that primarily identify attacker activity through login attempts, honeytokens embed within databases, files, or emails to trace data exfiltration and insider threats with higher granularity. Common applications include monitoring database queries, tracking the use of decoy credentials in phishing attacks, and triggering alerts when dummy API keys are abused, enhancing proactive threat detection and incident response.
Detection Techniques: Trap Accounts vs Honeytokens
Trap accounts enhance detection techniques by mimicking legitimate user profiles, allowing security teams to identify suspicious login attempts, unauthorized access, or lateral movement within a network. Honeytokens function as digital bait--such as fake credentials or database entries--that generate alerts when accessed, signaling potential data breaches or insider threats. Both methods leverage deception but differ in application scope: trap accounts monitor user behavior while honeytokens detect unauthorized interactions with sensitive information.
Benefits and Limitations of Trap Accounts
Trap accounts enhance cybersecurity by deceiving attackers with fake credentials, enabling early threat detection and detailed monitoring of malicious activities. These accounts limit false positives and reduce collateral damage by isolating attacker actions without affecting real user data. However, trap accounts require careful configuration to avoid accidental exposure and potential misuse by insiders, and they may demand significant resources for setup and continuous maintenance.
Advantages and Drawbacks of Honeytokens
Honeytokens offer a covert method to detect unauthorized access by embedding fake data or credentials within a system, making them highly effective for early threat detection without alerting attackers. Their advantage lies in minimal resource consumption and ease of deployment across various digital environments, enhancing deception without extensive infrastructure. However, honeytokens may generate false positives and require careful management to avoid desensitization or accidental exposure to legitimate users, potentially reducing their long-term effectiveness.
Choosing the Right Deception Tool: Trap Account or Honeytoken?
Choosing between a trap account and a honeytoken depends on the specific cybersecurity goals and threat models. Trap accounts, also known as honeypot accounts, simulate real user profiles to attract attackers and monitor intrusion attempts, providing detailed insight into attacker behavior and techniques. Honeytokens are discrete pieces of fake data, such as bogus credentials or documents, that alert defenders upon unauthorized access, offering a lightweight and stealthy deception method ideal for detecting insider threats and lateral movement.
Trap account Infographic
 libterm.com
libterm.com