Phishing is a cyberattack method where attackers impersonate legitimate organizations to steal your sensitive information such as passwords, credit card numbers, or personal details. Recognizing suspicious emails and avoiding clicking on unknown links are essential steps to protect yourself from falling victim to these scams. Read the rest of this article to learn effective strategies that safeguard your online security against phishing threats.
Table of Comparison
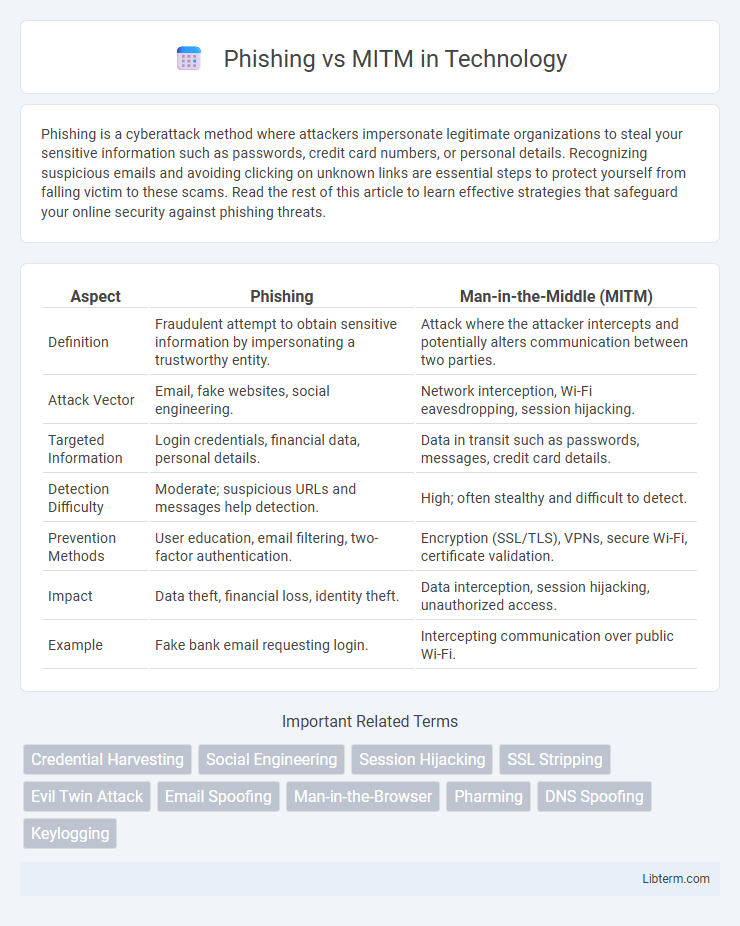
| Aspect | Phishing | Man-in-the-Middle (MITM) |
|---|---|---|
| Definition | Fraudulent attempt to obtain sensitive information by impersonating a trustworthy entity. | Attack where the attacker intercepts and potentially alters communication between two parties. |
| Attack Vector | Email, fake websites, social engineering. | Network interception, Wi-Fi eavesdropping, session hijacking. |
| Targeted Information | Login credentials, financial data, personal details. | Data in transit such as passwords, messages, credit card details. |
| Detection Difficulty | Moderate; suspicious URLs and messages help detection. | High; often stealthy and difficult to detect. |
| Prevention Methods | User education, email filtering, two-factor authentication. | Encryption (SSL/TLS), VPNs, secure Wi-Fi, certificate validation. |
| Impact | Data theft, financial loss, identity theft. | Data interception, session hijacking, unauthorized access. |
| Example | Fake bank email requesting login. | Intercepting communication over public Wi-Fi. |
Understanding Phishing and MITM Attacks
Phishing attacks manipulate users into revealing sensitive information by masquerading as trustworthy entities, often through deceptive emails or websites. Man-in-the-Middle (MITM) attacks intercept and alter communication between two parties without their knowledge, enabling attackers to steal data or inject malicious content. Understanding these techniques is crucial for implementing effective cybersecurity measures and protecting personal and organizational data.
Key Differences Between Phishing and MITM
Phishing involves deceiving users into revealing sensitive information through fraudulent emails or websites, exploiting human trust and social engineering tactics. MITM (Man-in-the-Middle) attacks intercept and manipulate communications between two parties without their knowledge, targeting network vulnerabilities to capture data in transit. The key difference lies in phishing exploiting user interaction to steal credentials, while MITM directly compromises data transmission channels.
How Phishing Attacks Work
Phishing attacks trick users into revealing sensitive information by masquerading as trustworthy entities through emails, fake websites, or messages. These attacks exploit social engineering techniques to prompt victims to enter credentials, download malware, or share confidential data. Cybercriminals leverage phishing to gain unauthorized access, often initiating further exploits like Man-in-the-Middle (MITM) attacks.
How Man-in-the-Middle (MITM) Attacks Operate
Man-in-the-Middle (MITM) attacks operate by secretly intercepting and altering communication between two parties without their knowledge, often exploiting unsecured networks or weak cryptographic protocols. Attackers position themselves between the victim and the destination server to capture sensitive information like login credentials, credit card numbers, or personal messages in real-time. MITM techniques include packet sniffing, session hijacking, and DNS spoofing, making these attacks highly dangerous for unencrypted data transmissions.
Common Techniques Used in Phishing
Phishing commonly employs deceptive emails, fake websites, and social engineering tactics to trick users into revealing sensitive information like passwords and credit card details. Attackers often use spear phishing, which targets specific individuals or organizations using personalized messages to increase success rates. Credential harvesting through malicious links and attachments remains a primary method in phishing campaigns, distinguishing it from Man-in-the-Middle (MITM) attacks that intercept data during transmission.
Popular Methods for Conducting MITM Attacks
Man-in-the-Middle (MITM) attacks commonly exploit methods such as ARP spoofing, DNS spoofing, and Wi-Fi eavesdropping to intercept and manipulate communications between two parties. Attackers use ARP spoofing to redirect traffic within a local network by associating their MAC address with the IP address of a legitimate user, enabling data capture. DNS spoofing involves corrupting the DNS cache to redirect victims to fake websites, while Wi-Fi eavesdropping leverages unsecured wireless networks to sniff sensitive data in transit.
Signs and Symptoms of Phishing Attempts
Phishing attempts often exhibit signs such as unsolicited emails or messages containing urgent requests, suspicious links, and poor grammar or spelling errors. These messages may mimic legitimate organizations and use deceptive domain names or email addresses to trick recipients into revealing sensitive information. Recognizing inconsistencies in sender details and unexpected requests for passwords or financial data helps identify phishing threats before falling victim.
Indicators of a Potential MITM Attack
Indicators of a potential Man-in-the-Middle (MITM) attack include unexpected SSL/TLS certificate warnings, such as mismatched or expired certificates, which suggest someone is intercepting encrypted communications. Users may notice unusual network latency or repeated authentication prompts when accessing websites or services, indicating possible interception. Other signs include unexpected changes in DNS settings, altered IP addresses, or suspicious Wi-Fi networks masquerading as legitimate access points.
Preventive Measures Against Phishing
Effective preventive measures against phishing include implementing robust email filtering systems that detect and block malicious links, using multi-factor authentication (MFA) to add an extra layer of security, and regularly educating employees about recognizing phishing attempts and suspicious communications. Organizations should also ensure that software and security patches are kept up to date to prevent exploitation of vulnerabilities commonly targeted by phishing attacks. Employing domain-based message authentication, reporting, and conformance (DMARC) helps verify email sender legitimacy, further reducing the risk of successful phishing.
Security Best Practices to Prevent MITM
Implement strong encryption protocols such as TLS and SSH to secure communications and prevent Man-in-the-Middle (MITM) attacks. Use multi-factor authentication and regularly update software to reduce vulnerabilities exploited by attackers. Employ network monitoring tools to detect unusual traffic patterns indicating potential MITM activity and prioritize user education on recognizing phishing attempts linked to these attacks.
Phishing Infographic
 libterm.com
libterm.com