Firewalls serve as a critical barrier between your internal network and potential external threats, monitoring and controlling incoming and outgoing traffic based on security rules. Implementing a robust firewall strategy helps prevent unauthorized access and safeguards sensitive data from cyberattacks. Discover how optimizing your firewall settings can enhance your overall network security by reading the rest of this article.
Table of Comparison
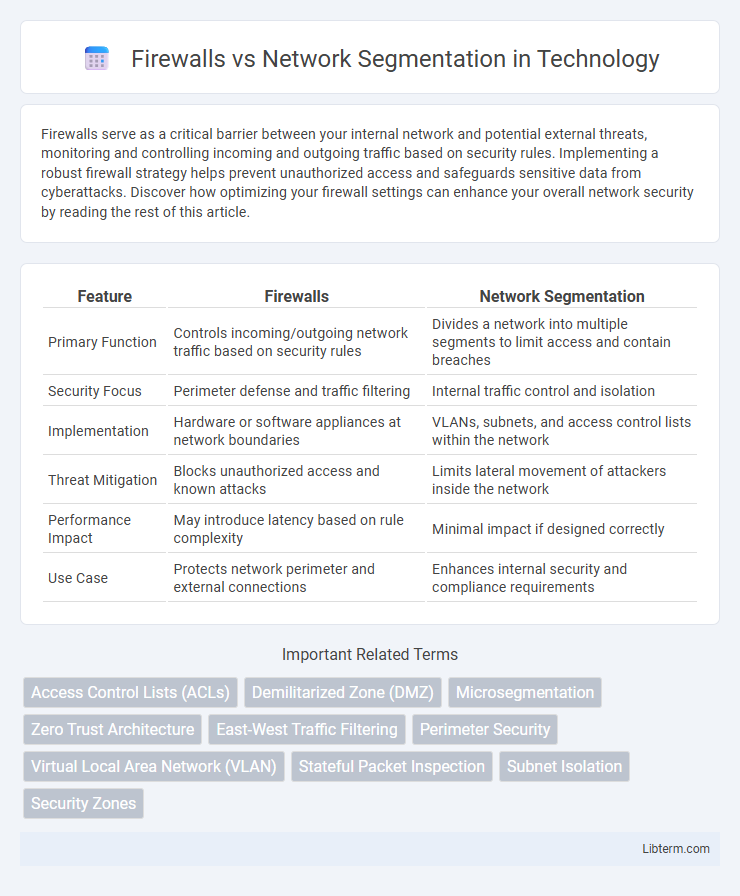
| Feature | Firewalls | Network Segmentation |
|---|---|---|
| Primary Function | Controls incoming/outgoing network traffic based on security rules | Divides a network into multiple segments to limit access and contain breaches |
| Security Focus | Perimeter defense and traffic filtering | Internal traffic control and isolation |
| Implementation | Hardware or software appliances at network boundaries | VLANs, subnets, and access control lists within the network |
| Threat Mitigation | Blocks unauthorized access and known attacks | Limits lateral movement of attackers inside the network |
| Performance Impact | May introduce latency based on rule complexity | Minimal impact if designed correctly |
| Use Case | Protects network perimeter and external connections | Enhances internal security and compliance requirements |
Introduction to Firewalls and Network Segmentation
Firewalls are security devices designed to monitor and control incoming and outgoing network traffic based on predetermined security rules, serving as a barrier between trusted internal networks and untrusted external networks. Network segmentation involves dividing a larger network into smaller, isolated segments to enhance security, improve performance, and contain potential threats within specific zones. Both firewalls and network segmentation play crucial roles in a layered security strategy by controlling access and limiting the spread of cyberattacks across an organization's infrastructure.
What Are Firewalls?
Firewalls are security devices that monitor and control incoming and outgoing network traffic based on predetermined security rules, effectively creating a barrier between trusted internal networks and untrusted external networks. They operate at various layers of the OSI model, primarily filtering traffic by IP addresses, ports, and protocols to prevent unauthorized access and cyber threats. Firewalls can be hardware-based, software-based, or a combination of both, and are essential components in network security strategies to protect data integrity and confidentiality.
Understanding Network Segmentation
Network segmentation enhances security by dividing a network into smaller, isolated segments to control traffic flow and limit the spread of threats. Unlike firewalls, which primarily inspect and filter incoming and outgoing traffic at perimeter points, segmentation enforces internal boundaries that restrict lateral movement within the network. Implementing network segmentation reduces attack surfaces, improves performance, and aligns with zero-trust architectures by enforcing strict access controls between segments.
Key Differences: Firewalls vs Network Segmentation
Firewalls serve as security barriers that monitor and control incoming and outgoing network traffic based on predefined security rules, effectively filtering access at the perimeter or between network zones. Network segmentation divides a larger network into smaller, isolated segments or subnets to contain potential threats, limit lateral movement, and improve overall network performance. While firewalls enforce access controls at network boundaries, network segmentation structures the network to isolate sensitive systems, enhancing security through separation rather than mere traffic filtering.
Advantages of Using Firewalls
Firewalls provide a critical barrier that controls inbound and outbound network traffic based on predetermined security rules, effectively preventing unauthorized access and cyber threats. They offer real-time monitoring and filtering of data packets, enhancing the overall security posture by detecting and blocking malicious activities before they reach internal networks. Firewalls also simplify threat management and compliance by centralizing security policies, making it easier to enforce and audit protections across the entire IT infrastructure.
Benefits of Network Segmentation
Network segmentation enhances security by isolating sensitive data and critical systems, limiting the attack surface and preventing lateral movement during cyberattacks. It improves network performance through reduced congestion and optimized traffic flow within defined segments. By enabling granular access control and easier threat detection, network segmentation supports regulatory compliance and minimizes the impact of potential breaches.
Use Cases for Firewalls
Firewalls serve as critical security barriers controlling inbound and outbound network traffic based on predetermined security rules, effectively preventing unauthorized access and cyber threats across various use cases such as protecting sensitive data in enterprise environments and securing web applications. They are essential for enforcing perimeter defenses in corporate networks, enabling granular control over traffic between internal and external networks, and supporting VPN connectivity for remote workforce security. Firewalls also facilitate compliance with regulatory requirements by logging traffic and detecting malicious activities, making them indispensable in industries like finance, healthcare, and government.
Use Cases for Network Segmentation
Network segmentation enhances security by dividing a network into isolated zones, limiting lateral movement in case of breaches and containing potential threats within specific segments. Use cases include protecting sensitive data environments such as payment processing networks (PCI DSS compliance), isolating IoT devices to reduce attack surfaces, and segmenting guest from corporate networks to enforce different access controls. Unlike firewalls that control traffic at perimeter or between zones, segmentation enforces internal boundaries, improving granular security policies and reducing the impact of compromised systems.
Combining Firewalls and Network Segmentation for Enhanced Security
Combining firewalls and network segmentation strengthens cybersecurity by limiting access points and isolating sensitive data within distinct network zones. Firewalls enforce strict access controls and monitor traffic, while segmentation restricts lateral movement of attackers by dividing the network into smaller, controlled segments. This integrated approach reduces the attack surface, limits breach impact, and improves overall threat detection and response capabilities.
Choosing the Right Approach for Your Network
Selecting between firewalls and network segmentation depends on your organization's security needs and network complexity. Firewalls provide perimeter defense by controlling inbound and outbound traffic based on predefined security rules, effectively blocking unauthorized access. Network segmentation divides your network into isolated zones, limiting the spread of threats by containing potential breaches within smaller sectors, which enhances internal security and improves traffic management.
Firewalls Infographic
 libterm.com
libterm.com