OAuth2 Client Credentials Flow enables secure server-to-server authentication by allowing applications to obtain an access token using their own credentials, without involving user interaction. This flow is ideal for automated processes, background services, or machine-to-machine communication requiring API access. Discover how implementing this flow can enhance your system's security and efficiency by reading the full article.
Table of Comparison
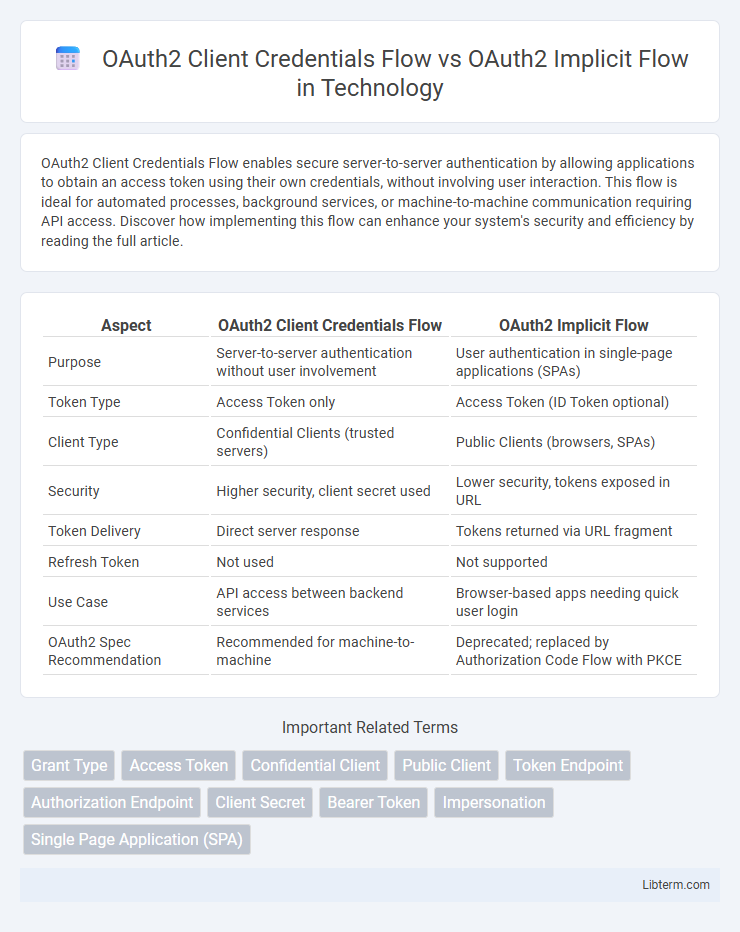
| Aspect | OAuth2 Client Credentials Flow | OAuth2 Implicit Flow |
|---|---|---|
| Purpose | Server-to-server authentication without user involvement | User authentication in single-page applications (SPAs) |
| Token Type | Access Token only | Access Token (ID Token optional) |
| Client Type | Confidential Clients (trusted servers) | Public Clients (browsers, SPAs) |
| Security | Higher security, client secret used | Lower security, tokens exposed in URL |
| Token Delivery | Direct server response | Tokens returned via URL fragment |
| Refresh Token | Not used | Not supported |
| Use Case | API access between backend services | Browser-based apps needing quick user login |
| OAuth2 Spec Recommendation | Recommended for machine-to-machine | Deprecated; replaced by Authorization Code Flow with PKCE |
Introduction to OAuth2 Authorization Flows
OAuth2 Client Credentials Flow is designed for server-to-server authentication, allowing applications to obtain an access token using their own credentials without user involvement. OAuth2 Implicit Flow targets single-page applications, enabling clients to receive tokens directly through browser redirects without exchanging an authorization code. Both flows address different security and architectural needs within OAuth2, optimizing token acquisition based on client type and use case.
Overview of Client Credentials Flow
OAuth2 Client Credentials Flow is a secure authentication method primarily used for server-to-server communication where no user context is involved. It allows applications to obtain an access token directly by authenticating with the authorization server using their own credentials, enabling access to protected resources or APIs on behalf of the application itself. This flow is ideal for machine-to-machine interactions, contrasting with the OAuth2 Implicit Flow, which is designed for user-agent-based applications with user authentication.
Overview of Implicit Flow
OAuth2 Implicit Flow is designed primarily for single-page applications (SPAs) that run entirely in a user's browser, enabling them to obtain access tokens directly from the authorization endpoint without an intermediate authorization code. This flow reduces the number of steps and avoids the need to store client secrets, making it suitable for public clients but less secure compared to other flows due to token exposure in URLs. Access tokens are delivered via URL fragments and must be handled carefully to prevent interception and replay attacks.
Key Differences Between Client Credentials and Implicit Flow
OAuth2 Client Credentials Flow is designed for server-to-server authentication where no user interaction is required, using client ID and secret to obtain an access token directly. OAuth2 Implicit Flow targets single-page applications, enabling the client to receive the access token via the browser without a back-end server, emphasizing speed and simplicity but with less security due to token exposure in the URL. The primary difference lies in the user involvement and token delivery method: Client Credentials Flow operates without user context and securely exchanges credentials via back-end, whereas Implicit Flow is user-driven and exposes tokens client-side.
Security Considerations for Each Flow
OAuth2 Client Credentials Flow offers enhanced security by directly exchanging client credentials for access tokens without exposing tokens to user agents, making it suitable for server-to-server communication with no user interaction. OAuth2 Implicit Flow exposes access tokens to the user agent, increasing the risk of token interception or leakage in browser-based applications, thus requiring careful handling of tokens and short-lived access durations to mitigate vulnerabilities. Implementing refresh token mechanisms is possible in Client Credentials but not in Implicit Flow, which limits long-term session management and heightens security risks in the latter.
Use Cases for Client Credentials Flow
OAuth2 Client Credentials Flow is ideal for server-to-server interactions where applications need to authenticate without user involvement, such as microservices communication, backend API authentication, and automated jobs. It provides secure access using client ID and secret, enabling services to obtain tokens directly from the authorization server. This flow avoids exposing tokens in user agents, making it preferable for machine-to-machine use cases over OAuth2 Implicit Flow, which is designed for browser-based applications requiring user delegation.
Use Cases for Implicit Flow
OAuth2 Implicit Flow is designed primarily for single-page applications (SPAs) and public clients where the client secret cannot be securely stored, enabling direct token issuance without an authorization code exchange. It is ideal for use cases requiring immediate access tokens on the client side, such as browser-based applications needing quick authentication for API calls without backend involvement. However, due to security drawbacks like token exposure in URLs, modern recommendations favor Authorization Code Flow with PKCE over Implicit Flow.
Advantages and Limitations of Client Credentials Flow
OAuth2 Client Credentials Flow offers secure server-to-server authentication without user involvement, making it ideal for machine-to-machine communication where confidentiality and token lifespan flexibility are crucial. It provides stronger security by avoiding token exposure in user agents, unlike the OAuth2 Implicit Flow, which is designed for user-agent-based applications but is less secure due to access tokens being directly accessible in browsers. Limitations of the Client Credentials Flow include the inability to represent user identity or permissions, restricting its use to scenarios without user context.
Advantages and Limitations of Implicit Flow
OAuth2 Implicit Flow offers advantages such as simplicity and reduced latency by eliminating the need for an authorization code exchange, making it suitable for single-page applications (SPAs) where secure storage of client secrets is challenging. However, it has limitations including increased exposure to access tokens in URL fragments, higher risk of token interception, and lack of refresh token support, which can lead to security vulnerabilities compared to more secure flows like Client Credentials Flow. The Client Credentials Flow, in contrast, is designed for server-to-server authentication without user involvement, providing enhanced security by using confidential clients and direct token exchanges.
Choosing the Right OAuth2 Flow for Your Application
Choosing the right OAuth2 flow depends on your application type and security requirements. The Client Credentials flow is ideal for server-to-server communication without direct user interaction, offering enhanced security with confidential client authentication. The Implicit flow targets browser-based or mobile applications requiring immediate access tokens but has higher security risks due to token exposure in the URL.
OAuth2 Client Credentials Flow Infographic
 libterm.com
libterm.com