OpenID Connect Hybrid Flow combines the benefits of both the Authorization Code Flow and the Implicit Flow, allowing your application to receive identity tokens and access tokens simultaneously. This approach enhances security and user experience by enabling immediate access to user information while securely obtaining tokens from the authorization server. Discover how leveraging Hybrid Flow can optimize your authentication process by reading the full article.
Table of Comparison
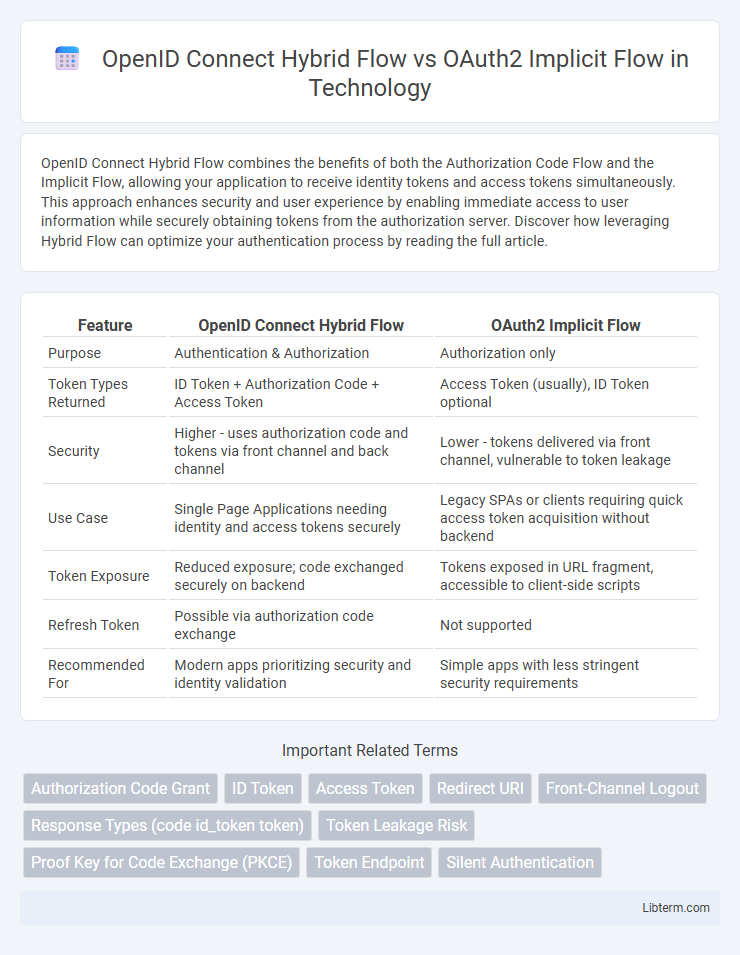
| Feature | OpenID Connect Hybrid Flow | OAuth2 Implicit Flow |
|---|---|---|
| Purpose | Authentication & Authorization | Authorization only |
| Token Types Returned | ID Token + Authorization Code + Access Token | Access Token (usually), ID Token optional |
| Security | Higher - uses authorization code and tokens via front channel and back channel | Lower - tokens delivered via front channel, vulnerable to token leakage |
| Use Case | Single Page Applications needing identity and access tokens securely | Legacy SPAs or clients requiring quick access token acquisition without backend |
| Token Exposure | Reduced exposure; code exchanged securely on backend | Tokens exposed in URL fragment, accessible to client-side scripts |
| Refresh Token | Possible via authorization code exchange | Not supported |
| Recommended For | Modern apps prioritizing security and identity validation | Simple apps with less stringent security requirements |
Introduction to OpenID Connect Hybrid Flow and OAuth2 Implicit Flow
OpenID Connect Hybrid Flow combines the benefits of OAuth2 Implicit Flow and Authorization Code Flow by allowing clients to receive tokens directly from the authorization endpoint while also obtaining an authorization code for secure token exchange. OAuth2 Implicit Flow enables client-side applications to acquire access tokens immediately from the authorization endpoint without an intermediate authorization code, enhancing speed but reducing security compared to other flows. Both flows serve different client needs: Hybrid Flow supports enhanced security and identity verification through ID tokens, whereas Implicit Flow prioritizes simplicity and quick token delivery for single-page applications.
Core Concepts and Protocol Differences
OpenID Connect Hybrid Flow combines features of both Authorization Code Flow and Implicit Flow, enabling clients to receive ID tokens and authorization codes simultaneously, enhancing security by allowing token validation server-side. OAuth2 Implicit Flow delivers tokens directly from the authorization endpoint without an intermediate code exchange, increasing exposure to tokens in browser-based applications but reducing latency. Key protocol differences include the Hybrid Flow's ability to securely obtain user identity alongside access tokens through separate channels, whereas Implicit Flow prioritizes immediate token access for public clients at the cost of weaker security guarantees.
How OpenID Connect Hybrid Flow Works
OpenID Connect Hybrid Flow combines features of both Authorization Code Flow and Implicit Flow by returning an ID token directly from the authorization endpoint along with an authorization code for server-side token exchange. This approach enables immediate user authentication with an ID token while securely retrieving access tokens through a back-end server, enhancing security over the Implicit Flow. Hybrid Flow supports dynamic client registration and allows fine-grained control over token issuance, improving flexibility and reducing exposure of tokens in browser environments.
How OAuth2 Implicit Flow Works
OAuth2 Implicit Flow is designed for single-page applications to obtain access tokens directly from the authorization endpoint without exchanging a code. It simplifies the process by returning tokens in the URL fragment, minimizing the need for server-side interaction but increasing exposure risk due to tokens being accessible via the user agent. This flow bypasses the authorization code exchange, making it faster but less secure compared to hybrid or authorization code flows because tokens are vulnerable to interception and replay attacks.
Security Considerations: Hybrid vs Implicit Flow
OpenID Connect Hybrid Flow enhances security by combining the benefits of both the authorization code and implicit flows, allowing tokens to be retrieved securely via server-side code while still enabling immediate token access in the client. OAuth2 Implicit Flow exposes tokens directly in the browser URL, increasing vulnerability to token leakage, interception, and replay attacks, making it less secure for modern applications. Hybrid Flow's use of server-side token exchange and ID token validation reduces risks such as token exposure and replay, thereby providing stronger protection against common security threats in authentication processes.
Token Handling and Delivery Mechanisms
OpenID Connect Hybrid Flow combines the benefits of the Authorization Code and Implicit Flows by delivering both an ID token and an authorization code, enabling secure token handling through back-channel code exchange and front-channel token delivery. OAuth2 Implicit Flow directly returns access tokens via the front-channel without intermediate code exchange, increasing exposure risk since tokens are delivered in URLs and cannot be securely stored server-side. Hybrid Flow enhances security by separating token delivery paths, reducing token leakage risks and enabling more robust token validation compared to the front-channel-only delivery mechanism used in the Implicit Flow.
Use Cases and Recommended Scenarios
OpenID Connect Hybrid Flow is ideal for applications requiring both identity tokens and access tokens with enhanced security, such as single-page applications needing server-side token validation and APIs demanding user authentication. OAuth2 Implicit Flow suits public clients like mobile or web apps where immediate token reception is critical, but it carries higher risks due to token exposure in URLs and should be avoided in highly sensitive environments. Recommended scenarios prioritize Hybrid Flow for complex apps with backend components and OAuth2 Implicit Flow for simpler, client-only applications with limited security needs.
Pros and Cons of OpenID Connect Hybrid Flow
OpenID Connect Hybrid Flow combines elements of both Authorization Code and Implicit flows, offering enhanced security by delivering tokens directly from the authorization endpoint and the token endpoint. This approach allows immediate access to identity tokens while maintaining the ability to securely obtain access tokens via a back-channel, reducing exposure to token interception risks common in pure Implicit Flow. However, Hybrid Flow's complexity increases implementation effort and requires secure client handling of multiple tokens, which may complicate development compared to the simpler, but less secure, OAuth2 Implicit Flow.
Pros and Cons of OAuth2 Implicit Flow
OAuth2 Implicit Flow offers faster token delivery by returning tokens directly in the URL without requiring a backend server, making it suitable for single-page applications (SPAs). However, it poses security risks such as exposure of access tokens in URLs, susceptibility to token theft through browser history, and lack of refresh token support, which can lead to vulnerability in token management. Modern best practices recommend migrating from Implicit Flow to Authorization Code Flow with PKCE for enhanced security in client-side applications.
Choosing the Best Flow for Your Application
Choosing the best flow for your application depends on security requirements and the type of client. OpenID Connect Hybrid Flow combines the benefits of both authorization code and implicit flows, offering enhanced security by delivering tokens directly to the client while allowing immediate ID token access. OAuth2 Implicit Flow suits single-page applications needing quick token access but carries higher security risks due to exposure of tokens in URLs, making Hybrid Flow preferable for applications requiring stronger security guarantees.
OpenID Connect Hybrid Flow Infographic
 libterm.com
libterm.com