Tokenized text refers to the process of breaking down a piece of text into smaller units called tokens, such as words, phrases, or symbols, to facilitate natural language processing tasks. This technique enhances the accuracy of text analysis, search, and machine learning models by enabling more precise handling of language components. Explore the article to understand how tokenization impacts your text processing applications and improves semantic understanding.
Table of Comparison
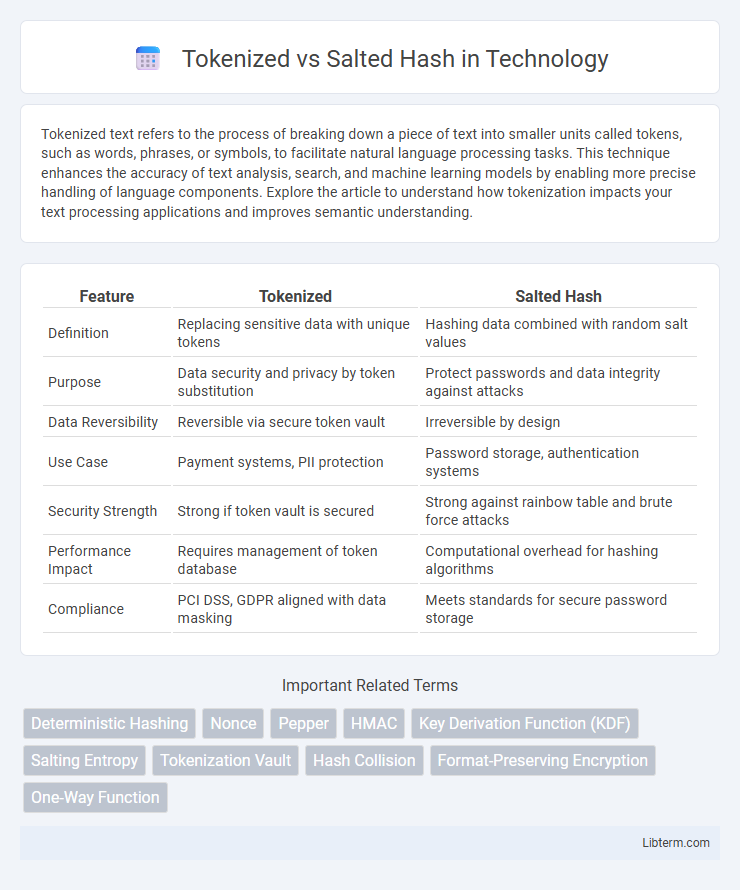
| Feature | Tokenized | Salted Hash |
|---|---|---|
| Definition | Replacing sensitive data with unique tokens | Hashing data combined with random salt values |
| Purpose | Data security and privacy by token substitution | Protect passwords and data integrity against attacks |
| Data Reversibility | Reversible via secure token vault | Irreversible by design |
| Use Case | Payment systems, PII protection | Password storage, authentication systems |
| Security Strength | Strong if token vault is secured | Strong against rainbow table and brute force attacks |
| Performance Impact | Requires management of token database | Computational overhead for hashing algorithms |
| Compliance | PCI DSS, GDPR aligned with data masking | Meets standards for secure password storage |
Introduction to Tokenized vs Salted Hash
Tokenized and salted hash methods are essential techniques for securing sensitive data, such as passwords and payment information. Tokenization replaces data with unique, non-sensitive tokens, ensuring the original data is never exposed or stored. Salted hashing involves adding random data, known as a salt, to the input before hashing to prevent attacks like rainbow table lookups and enhance password security.
What is Tokenization?
Tokenization is a data security technique that replaces sensitive information, such as credit card numbers or personal identifiers, with unique, non-sensitive tokens, which retain the format but have no exploitable value. Unlike salted hashes that transform data using cryptographic functions combined with random salts to protect against reverse-engineering, tokenization isolates the original data in a secure token vault, minimizing exposure during transactions. This method is widely used in payment processing and data privacy compliance to reduce the risk of data breaches while maintaining transactional utility.
What is a Salted Hash?
A salted hash is a cryptographic technique that enhances password security by adding a unique, random value called a "salt" to the input before hashing. This process prevents attackers from using precomputed rainbow tables to reverse-engineer stored passwords, as each hash output is unique even for identical passwords. Salted hashes are widely used in authentication systems to mitigate risks of password theft and brute-force attacks.
Core Differences Between Tokenization and Salting
Tokenization replaces sensitive data with non-sensitive tokens that have no exploitable value, preserving the original data format for secure storage or transmission, while salting adds random data to passwords before hashing to enhance security by preventing rainbow table and precomputed hash attacks. Tokenization is primarily used in payment processing and data privacy to protect sensitive information without altering its usability, whereas salting is a cryptographic method designed to protect stored passwords by ensuring unique hash outputs even for identical inputs. The core difference lies in tokenization's approach of data substitution versus salting's method of data modification to strengthen hashing algorithms.
Security Implications of Tokenization
Tokenization enhances security by replacing sensitive data with unique tokens that have no exploitable value outside the system, thereby reducing the risk of data breaches. Unlike salted hashes, tokens do not rely on cryptographic transformations, minimizing vulnerability to reverse-engineering or brute-force attacks. Implementing tokenization can effectively isolate sensitive information from applications, limiting exposure and simplifying compliance with data protection regulations like PCI DSS and GDPR.
Security Strengths of Salted Hashes
Salted hashes enhance security by adding unique random values, or salts, to each password before hashing, significantly reducing the risk of rainbow table attacks and increasing resistance to brute-force attempts. This method ensures that identical passwords produce distinct hash outputs, preventing attackers from cracking multiple passwords simultaneously. Tokenized data replaces sensitive information with tokens but lacks the inherent cryptographic robustness of salted hashes, making salted hashes a stronger choice for securing password storage.
Use Cases: When to Use Tokenization
Tokenization is ideal for scenarios requiring secure storage and transmission of sensitive data such as payment card information, where the original data must be replaced with a non-sensitive equivalent to reduce compliance scope with standards like PCI DSS. Salted hashes are more suited for protecting passwords in authentication systems, as they prevent dictionary and rainbow table attacks by combining the password with a unique salt before hashing. Use tokenization when data needs to be reversible or need to maintain format and usability in business processes without exposing actual sensitive information.
Use Cases: When to Use Salted Hashing
Salted hashing is essential for securely storing passwords, as it protects against rainbow table and brute force attacks by adding unique random data to each password before hashing. Use salted hashing in applications requiring user authentication, ensuring that even if the hash database is compromised, individual passwords remain difficult to crack. Tokenization, in contrast, is better suited for protecting sensitive data such as credit card numbers by replacing them with non-sensitive tokens, making salted hashing the preferred choice for secure password management.
Pros and Cons: Tokenization vs Salted Hash
Tokenization enhances data security by replacing sensitive information with unique tokens that are meaningless outside the tokenization system, reducing the risk of data breaches and simplifying PCI compliance, but requires a secure token vault and can introduce complexity in key management. Salted hashing improves password security by adding a unique random value (salt) to each input before hashing, making it resistant to rainbow table attacks and ensuring that identical inputs produce different hashes, though it is irreversible and unsuitable for data that requires decryption. Tokenization is ideal for protecting payment card information and other personally identifiable data where reversibility is necessary, while salted hashing is best suited for securely storing passwords and verifying data authenticity without the need to retrieve original values.
Choosing the Right Approach for Your Data
Selecting between tokenized and salted hash methods depends on data sensitivity and use-case requirements; tokenization replaces sensitive data with non-sensitive equivalents, ideal for preserving format and supporting data reversibility under strict controls. Salted hashing transforms data into irreversible values combined with unique salt values, enhancing security against attacks like rainbow tables and is well-suited for password storage or integrity verification where reversibility is unnecessary. Evaluating regulatory compliance, system performance, and data retrieval needs ensures the right approach maximizes both security and operational efficiency.
Tokenized Infographic
 libterm.com
libterm.com