Second-party risk involves the potential threats and vulnerabilities that arise from your direct relationships with suppliers, contractors, or partners. Managing this risk requires thorough evaluation, regular monitoring, and clear communication to ensure your business operations remain secure. Discover how to effectively identify and mitigate second-party risk by reading the rest of the article.
Table of Comparison
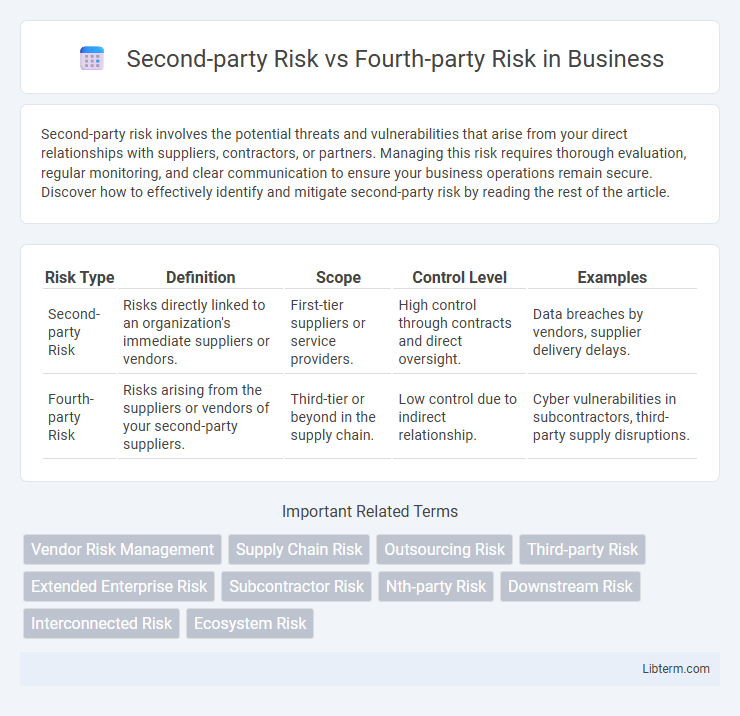
| Risk Type | Definition | Scope | Control Level | Examples |
|---|---|---|---|---|
| Second-party Risk | Risks directly linked to an organization's immediate suppliers or vendors. | First-tier suppliers or service providers. | High control through contracts and direct oversight. | Data breaches by vendors, supplier delivery delays. |
| Fourth-party Risk | Risks arising from the suppliers or vendors of your second-party suppliers. | Third-tier or beyond in the supply chain. | Low control due to indirect relationship. | Cyber vulnerabilities in subcontractors, third-party supply disruptions. |
Understanding Second-party Risk
Second-party risk involves the potential threats arising directly from a company's vendors or suppliers, who have a direct contractual relationship with the organization. This risk includes issues such as data breaches, operational failures, or compliance violations that can impact the company due to the dependency on these immediate external parties. Effective management of second-party risk requires thorough due diligence, continuous monitoring, and strong contractual controls to mitigate vulnerabilities stemming from these business partners.
Defining Fourth-party Risk
Fourth-party risk refers to the potential threats and vulnerabilities that arise from the subcontractors and service providers used by an organization's direct vendors, known as second parties. It extends the risk management scope beyond immediate suppliers to include indirect relationships that can impact security, compliance, and operational continuity. Understanding and mitigating fourth-party risk is essential for comprehensive supply chain resilience and regulatory compliance.
Key Differences Between Second-party and Fourth-party Risk
Second-party risk involves direct risks from a company's immediate suppliers or service providers, while fourth-party risk extends to risks originating from those suppliers' own subcontractors or service providers. The key difference lies in the level of control and visibility; companies often have more oversight over second parties but limited insight into fourth-party operations. Managing fourth-party risk requires enhanced due diligence and continuous monitoring to address potential vulnerabilities beyond direct contractual relationships.
Common Examples of Second-party Risks
Common examples of second-party risks include vendor non-compliance, data breaches caused by suppliers, and inadequate cybersecurity measures from third-party service providers directly contracted by a company. These risks arise when a company's immediate partners fail to meet contractual, regulatory, or security standards, potentially impacting business operations and reputation. Understanding these risks is crucial for effective vendor management and risk mitigation strategies.
Typical Scenarios Involving Fourth-party Risks
Fourth-party risks arise when an organization's third-party vendors outsource services to other entities, creating complex supply chain dependencies that are often less visible and harder to control. Typical scenarios involve cloud service providers subcontracting data management tasks or IT vendors relying on third-party software providers, exposing the primary organization to vulnerabilities from these indirect relationships. Monitoring and managing fourth-party risks require enhanced due diligence, continuous vendor risk assessments, and integrating comprehensive supply chain security protocols.
Impact of Second-party Risk on Organizations
Second-party risk refers to the potential threats an organization faces from its direct suppliers, vendors, or service providers whose actions or failures can disrupt operations, compromise data security, or lead to regulatory non-compliance. This risk can result in financial losses, reputational damage, and operational delays, directly impacting the organization's supply chain resilience and customer trust. Effective management of second-party risk involves rigorous vendor assessment, continuous monitoring, and strong contractual controls to mitigate disruptions and safeguard organizational assets.
How Fourth-party Risk Extends the Supply Chain
Fourth-party risk extends the supply chain by encompassing the vendors and service providers that second parties rely on to fulfill their obligations, creating additional layers of dependency. This expanded risk landscape includes indirect relationships often overlooked in traditional risk management, increasing vulnerability to cybersecurity breaches, operational disruptions, and compliance failures. Organizations must map and monitor these fourth-party connections to effectively manage potential impacts that cascade beyond their direct suppliers.
Strategies to Identify Second-party and Fourth-party Risks
Implementing comprehensive vendor risk management systems enables organizations to identify second-party risks by thoroughly assessing suppliers and direct partners through audits, questionnaires, and performance metrics. To detect fourth-party risks, it's crucial to map and analyze the entire supply chain ecosystem, including subcontractors and extended service providers, leveraging continuous monitoring tools and third-party risk intelligence platforms. Integrating automated risk assessment solutions with real-time data analytics enhances visibility into both second-party and fourth-party entities, facilitating proactive mitigation strategies and compliance adherence.
Best Practices for Managing Extended Third-party Relationships
Effective management of extended third-party relationships involves rigorous due diligence and continuous monitoring of both second-party and fourth-party risks. Implementing robust vendor assessment frameworks, detailed contractual agreements, and real-time risk analytics ensures transparency and reduces vulnerabilities across the supply chain. Leveraging automation tools and establishing clear communication protocols enhances oversight and mitigates cascading risks from less visible fourth-party entities.
Future Trends in Second-party and Fourth-party Risk Management
Future trends in second-party and fourth-party risk management emphasize enhanced visibility through advanced analytics and AI-driven platforms, enabling organizations to map and monitor complex supply chains more effectively. Increasing regulatory scrutiny and evolving cybersecurity threats drive the adoption of integrated risk assessment tools that evaluate not only direct vendors but also their extended networks, including subcontractors and partners. Firms are investing in continuous real-time monitoring systems and collaboration frameworks to proactively mitigate risks stemming from fourth-party relationships, ensuring resilience and compliance in dynamic global markets.
Second-party Risk Infographic
 libterm.com
libterm.com