An empty threat lacks the intention or capability to follow through, rendering it ineffective in influencing behavior or decisions. Such threats often undermine your credibility and can lead to diminished trust in both personal and professional relationships. Explore the article to understand how to identify, respond to, and avoid making empty threats yourself.
Table of Comparison
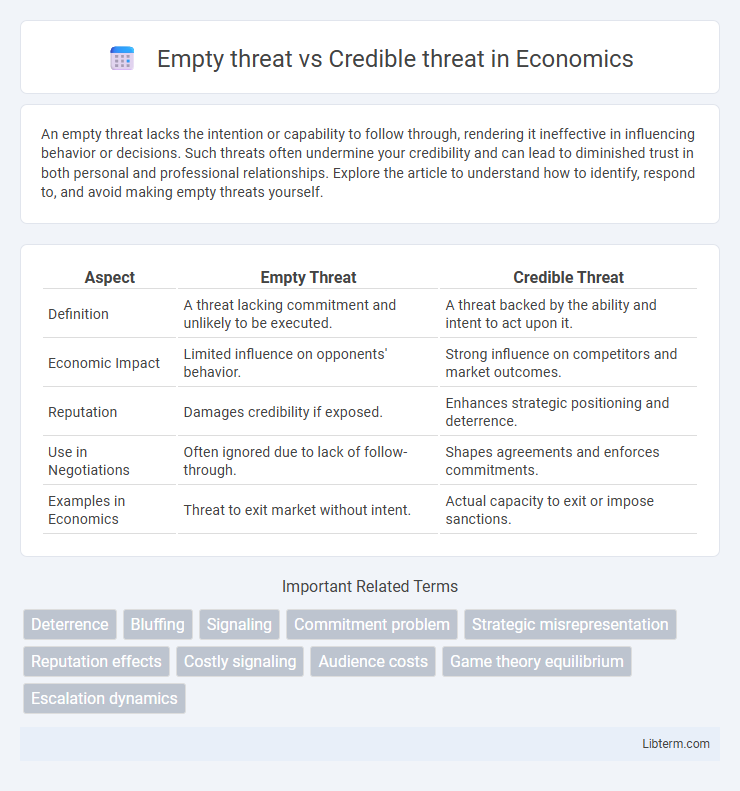
| Aspect | Empty Threat | Credible Threat |
|---|---|---|
| Definition | A threat lacking commitment and unlikely to be executed. | A threat backed by the ability and intent to act upon it. |
| Economic Impact | Limited influence on opponents' behavior. | Strong influence on competitors and market outcomes. |
| Reputation | Damages credibility if exposed. | Enhances strategic positioning and deterrence. |
| Use in Negotiations | Often ignored due to lack of follow-through. | Shapes agreements and enforces commitments. |
| Examples in Economics | Threat to exit market without intent. | Actual capacity to exit or impose sanctions. |
Understanding Threats: Empty vs. Credible
Empty threats lack the intention or capability to follow through, often used as bluffing tactics to influence behavior without real consequences. Credible threats, supported by a demonstrable ability and willingness to act, hold significant persuasive power in negotiations and conflict resolution. Recognizing the difference hinges on evaluating the actor's resources, past behavior, and the plausibility of execution in the given context.
Defining Empty Threats in Conflict Situations
Empty threats in conflict situations refer to warnings or statements of action that lack the intention or capability to be carried out, undermining their effectiveness in influencing opponents. These threats often fail to alter the behavior of the opposing party due to the perceived lack of real consequences. Understanding the distinction between empty and credible threats is crucial for strategic decision-making and maintaining negotiation leverage.
Characteristics of Credible Threats
Credible threats are characterized by the threatener's ability and willingness to follow through, creating a realistic risk that influences the target's decision-making. They often involve clear communication, consistent past behavior, and the presence of tangible resources or power to enforce the threat. The reliability and seriousness of these elements distinguish credible threats from empty threats, which lack the capability or intent to be executed.
Key Differences Between Empty and Credible Threats
Empty threats lack the intention or capability to be executed, making them ineffective in influencing behavior or decisions. Credible threats are backed by the ability and willingness to follow through, thereby having a tangible impact on the target's choices. The key difference lies in the perceived likelihood of enforcement, which determines their power and strategic value in negotiations or conflicts.
Psychological Impact of Threat Credibility
The psychological impact of threat credibility hinges on the perceived likelihood of enforcement, with credible threats provoking heightened anxiety, fear, and compliance due to anticipated consequences. Empty threats, lacking follow-through, diminish trust and reduce emotional arousal, often leading to disregard or defiance. Understanding the dynamic between threat credibility and victim response is crucial in fields such as negotiation, security, and behavioral psychology.
Real-World Examples: Empty vs. Credible Threats
An empty threat occurs when a party declares an intention to take action but lacks the will or capability to follow through, such as North Korea's repeated missile test warnings without escalation. In contrast, credible threats involve genuine capabilities and intent, exemplified by the U.S. imposing strict economic sanctions on Iran during nuclear negotiations, demonstrating readiness to enforce consequences. The effectiveness of a threat depends on the perceived willingness and ability to act, influencing diplomatic and strategic outcomes.
Detecting an Empty Threat: Warning Signs
Detecting an empty threat involves recognizing inconsistencies between the threatener's words and actions, such as a lack of follow-through or unrealistic demands that lack enforcement capability. Warning signs include exaggerated claims without past evidence of action, hesitation during confrontation, and conflicting nonverbal cues like nervousness or avoidance. Understanding these indicators helps differentiate credible threats that demand attention from empty threats designed merely to intimidate without intent to act.
Strategies for Responding to Different Types of Threats
Empty threats lack the intention or capability to be executed, requiring a firm and confident response to avoid undermining authority. Credible threats involve real potential consequences and demand careful assessment, strategic negotiation, or preemptive measures to mitigate risks effectively. Tailoring responses by evaluating the threat's credibility ensures appropriate resource allocation and maintains strategic advantage in conflict resolution.
Consequences of Making Empty vs. Credible Threats
Empty threats undermine trust and damage relationships, often leading to diminished influence and credibility in future interactions. Credible threats, backed by the willingness and ability to follow through, create effective deterrence and enforce boundaries, resulting in predictable and controlled outcomes. The consequences of making credible threats include gaining respect and compliance, whereas empty threats risk retaliation, loss of authority, and escalated conflicts.
Building and Maintaining Credibility in Negotiations
Building and maintaining credibility in negotiations hinges on distinguishing empty threats from credible threats. Credible threats rely on the negotiator's demonstrated willingness and capacity to act, supported by consistent past behavior and clear consequences. Empty threats, lacking follow-through or feasibility, undermine trust and weaken bargaining power, ultimately diminishing the negotiator's influence.
Empty threat Infographic
 libterm.com
libterm.com