Digital signatures ensure the authenticity and integrity of electronic documents by using cryptographic techniques to verify the sender's identity. They provide a secure way to sign contracts, agreements, and other important files without physical presence or paper. Discover how digital signatures can protect your transactions and streamline your workflows by reading the full article.
Table of Comparison
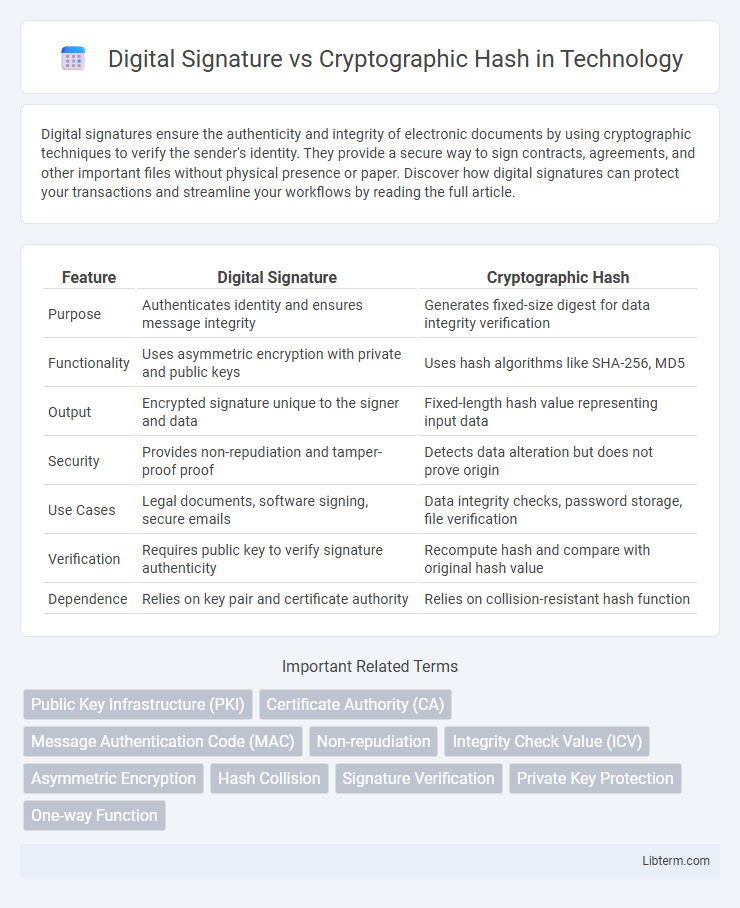
| Feature | Digital Signature | Cryptographic Hash |
|---|---|---|
| Purpose | Authenticates identity and ensures message integrity | Generates fixed-size digest for data integrity verification |
| Functionality | Uses asymmetric encryption with private and public keys | Uses hash algorithms like SHA-256, MD5 |
| Output | Encrypted signature unique to the signer and data | Fixed-length hash value representing input data |
| Security | Provides non-repudiation and tamper-proof proof | Detects data alteration but does not prove origin |
| Use Cases | Legal documents, software signing, secure emails | Data integrity checks, password storage, file verification |
| Verification | Requires public key to verify signature authenticity | Recompute hash and compare with original hash value |
| Dependence | Relies on key pair and certificate authority | Relies on collision-resistant hash function |
Introduction to Digital Signatures and Cryptographic Hashes
Digital signatures provide a secure method for verifying the authenticity and integrity of digital messages by using asymmetric cryptography, where a private key signs the message and a public key verifies it. Cryptographic hashes generate a fixed-size string of characters from input data, serving as a unique digital fingerprint that detects changes or tampering. Unlike digital signatures that authenticate the sender, cryptographic hashes ensure data integrity by producing consistent outputs for identical inputs and drastically different outputs for any modification.
Defining Digital Signatures: Purpose and Function
Digital signatures serve as a cryptographic mechanism to verify the authenticity and integrity of digital documents by using a private key to create a unique signature linked to the message content. Their primary purpose is to provide non-repudiation, ensuring the signer cannot deny the transaction, and to guarantee that the data has not been altered since signing. Unlike cryptographic hashes, which generate fixed-size outputs from arbitrary inputs to detect changes, digital signatures combine hash functions with asymmetric encryption to enable secure identity verification and data integrity simultaneously.
Understanding Cryptographic Hash Functions
Cryptographic hash functions generate a fixed-size string of characters from input data, ensuring data integrity by producing unique hash values for different inputs. Unlike digital signatures, which involve asymmetric encryption and provide authentication and non-repudiation, cryptographic hashes are primarily designed for verifying data consistency without revealing the original data. Key properties of cryptographic hash functions include determinism, preimage resistance, and collision resistance, making them essential for security protocols and digital forensics.
Key Differences Between Digital Signatures and Hashes
Digital signatures provide authentication, non-repudiation, and integrity by encrypting a hash value with a private key, whereas cryptographic hashes generate a fixed-size output from input data primarily for integrity verification without key requirements. Digital signatures involve asymmetric cryptography with public and private keys, enabling verification by anyone with the public key, while hashes use deterministic algorithms like SHA-256 to produce consistent digests for identical inputs. The critical difference lies in digital signatures ensuring origin authenticity and proof of signing, while hashes serve as a compact, unique fingerprint identifying data changes.
Core Use Cases for Digital Signatures
Digital signatures primarily ensure authenticity, non-repudiation, and integrity in electronic documents by verifying the signer's identity and confirming the message has not been altered. Core use cases include securing email communications, authenticating software distribution, and enabling legally binding electronic contracts. Cryptographic hashes support digital signatures by generating unique message digests but do not provide identity verification or non-repudiation on their own.
Primary Applications of Cryptographic Hashes
Cryptographic hashes serve as fundamental tools for data integrity verification by producing fixed-size hash values that uniquely represent original data, enabling efficient detection of any alterations. Primary applications include file integrity checks, password storage through hashing, and digital fingerprinting in blockchain technology to ensure immutable transaction records. These hashes underpin security protocols like SSL/TLS by verifying message authenticity without exposing underlying content, highlighting their critical role in cybersecurity.
Security Benefits: Digital Signature vs Hash Function
Digital signatures provide authentication, non-repudiation, and integrity by combining a cryptographic hash with asymmetric encryption, ensuring the sender's identity and message authenticity. In contrast, cryptographic hash functions verify data integrity by producing a fixed-size digest but do not offer authentication or non-repudiation on their own. The security benefits of digital signatures surpass hash functions alone by enabling verification of both data integrity and signer identity, critical for secure communications and legal validations.
Common Algorithms for Digital Signatures and Hashes
Common algorithms for digital signatures include RSA, DSA (Digital Signature Algorithm), and ECDSA (Elliptic Curve Digital Signature Algorithm), which provide authentication and non-repudiation by encrypting a hash with a private key. Cryptographic hash functions like SHA-256, SHA-3, and MD5 generate fixed-size outputs from variable-length inputs, ensuring data integrity by producing unique hash values for distinct data sets. While digital signatures use these hashes as part of the signing process, the primary distinction lies in their purpose: digital signatures verify authenticity and origin, whereas cryptographic hashes ensure data consistency and detect tampering.
Implementation Challenges and Best Practices
Digital signature implementation faces challenges such as key management complexity, computational overhead, and ensuring interoperability across diverse systems, while cryptographic hash functions must address collision resistance and algorithm performance. Best practices include using standardized algorithms like RSA or ECDSA for digital signatures and SHA-256 for hashing, alongside secure key storage solutions and regular algorithm updates to mitigate vulnerabilities. Emphasizing robust validation procedures and utilization of hardware security modules (HSMs) enhances overall security and reliability in both technologies.
Choosing the Right Solution: Digital Signature or Hash?
Choosing the right solution between a digital signature and a cryptographic hash depends on the security requirements and the intended use case. Digital signatures provide authentication, non-repudiation, and integrity by using asymmetric cryptography to verify the signer's identity, making them ideal for legal documents and secure communications. Cryptographic hashes ensure data integrity by generating a fixed-size hash value from input data but lack authentication features, making them suitable for verifying data consistency and detecting tampering without confirming the source.
Digital Signature Infographic
 libterm.com
libterm.com