Phishing attacks manipulate individuals into revealing sensitive information through deceptive emails, websites, or messages that appear legitimate. These cyber threats can lead to identity theft, financial loss, and compromised personal data. To protect yourself effectively, explore the rest of this article for essential tips on recognizing and defending against phishing scams.
Table of Comparison
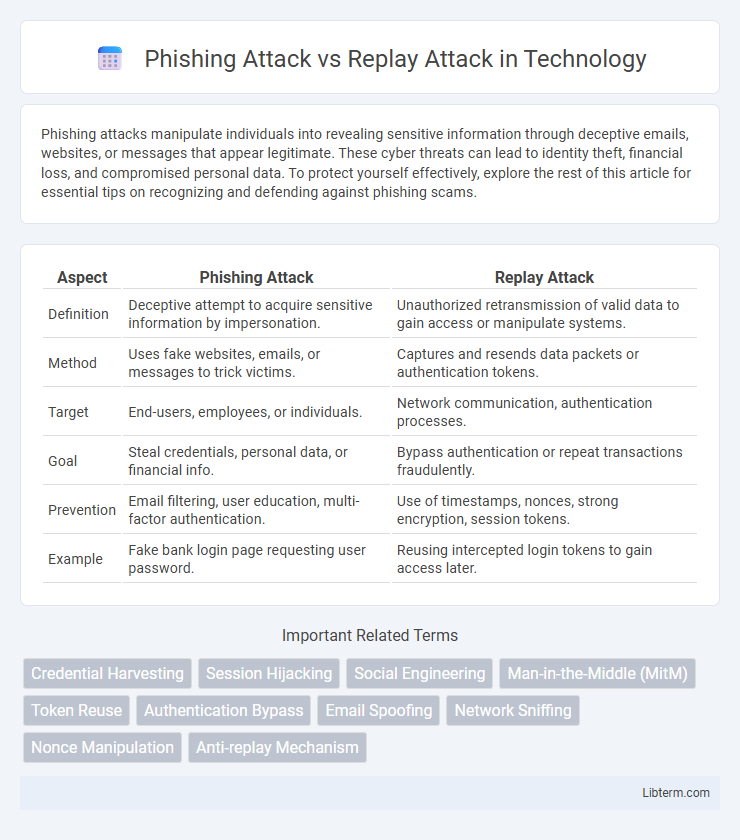
| Aspect | Phishing Attack | Replay Attack |
|---|---|---|
| Definition | Deceptive attempt to acquire sensitive information by impersonation. | Unauthorized retransmission of valid data to gain access or manipulate systems. |
| Method | Uses fake websites, emails, or messages to trick victims. | Captures and resends data packets or authentication tokens. |
| Target | End-users, employees, or individuals. | Network communication, authentication processes. |
| Goal | Steal credentials, personal data, or financial info. | Bypass authentication or repeat transactions fraudulently. |
| Prevention | Email filtering, user education, multi-factor authentication. | Use of timestamps, nonces, strong encryption, session tokens. |
| Example | Fake bank login page requesting user password. | Reusing intercepted login tokens to gain access later. |
Introduction to Cybersecurity Threats
Phishing attacks manipulate users into revealing sensitive information through deceptive emails or websites, posing a significant cybersecurity threat by targeting human vulnerabilities. Replay attacks exploit intercepted data by retransmitting valid data packets to gain unauthorized access or disrupt communications, highlighting risks in network security protocols. Both attacks underscore the need for robust encryption, user education, and multi-factor authentication to mitigate cybersecurity threats effectively.
Understanding Phishing Attacks
Phishing attacks involve cybercriminals impersonating trusted entities through emails or websites to steal sensitive information like passwords and credit card details. These attacks exploit human psychology by creating a sense of urgency or trust, tricking victims into divulging confidential data. Understanding phishing includes recognizing common tactics such as fake URLs, suspicious attachments, and urgent requests to prevent falling victim to credential theft.
Understanding Replay Attacks
Replay attacks exploit the retransmission of valid data to gain unauthorized access or perform fraudulent transactions, posing significant risks in network communications and authentication systems. Unlike phishing attacks that deceive users into revealing credentials, replay attacks capture and reuse legitimate authentication tokens or messages without altering their content. Implementing time-stamped tokens, session identifiers, and challenge-response protocols effectively mitigates replay attack vulnerabilities in secure systems.
Key Differences Between Phishing and Replay Attacks
Phishing attacks exploit social engineering to deceive victims into revealing sensitive information by impersonating trustworthy entities, primarily targeting humans. Replay attacks involve intercepting and retransmitting valid data packets within a network to gain unauthorized access or perform fraudulent transactions, focusing on exploiting system vulnerabilities. The key difference lies in phishing targeting user behavior for credential theft, while replay attacks manipulate data transmission mechanisms without direct user interaction.
Common Techniques Used in Phishing Attacks
Phishing attacks commonly use deceptive emails, fake websites, and social engineering tactics to trick victims into revealing sensitive information such as passwords and credit card details. Attackers often employ spear phishing, where they tailor messages to specific individuals or organizations, and clone phishing, which replicates legitimate communications to lure victims. These techniques exploit human trust and technological vulnerabilities, distinguishing phishing from replay attacks that involve intercepting and retransmitting valid data to gain unauthorized access.
Methods Employed in Replay Attacks
Replay attacks involve intercepting valid data transmissions and fraudulently repeating or delaying them to gain unauthorized access, often exploiting weaknesses in authentication protocols and session management. Methods employed include capturing authentication tokens, such as session cookies or cryptographic nonces, and resending them to masquerade as legitimate users without needing to decrypt data. Attackers may use tools like packet sniffers or man-in-the-middle techniques to record and retransmit these messages within a limited time frame before tokens expire.
Impact of Phishing Attacks on Organizations
Phishing attacks pose a significant threat to organizations by targeting employees through deceptive communications, leading to unauthorized access to sensitive data and financial losses. These attacks undermine trust, disrupt operations, and increase the risk of data breaches affecting customer information and intellectual property. Unlike replay attacks, which primarily exploit network vulnerabilities, phishing attacks leverage human factors, making them harder to detect and prevent.
Consequences of Replay Attacks on Data Security
Replay attacks severely threaten data security by allowing unauthorized users to intercept and resend valid data transmissions, leading to unauthorized access and data breaches. These attacks can compromise authentication processes, enabling attackers to impersonate legitimate users and gain control over sensitive systems. The loss of data integrity and confidentiality resulting from replay attacks undermines trust in communication networks and can cause significant financial and reputational damage.
Prevention Strategies for Phishing and Replay Attacks
Phishing attack prevention strategies include implementing multi-factor authentication (MFA), educating users on recognizing suspicious emails, and deploying advanced email filtering systems to detect and block malicious content. Replay attack prevention involves using cryptographic techniques such as nonce values, timestamps, and secure session tokens to ensure message freshness and prevent unauthorized retransmission. Employing end-to-end encryption and continuous monitoring of network traffic further strengthens defenses against both phishing and replay attacks.
Conclusion: Strengthening Cyber Resilience
Phishing attacks exploit human vulnerabilities by tricking individuals into revealing sensitive information, while replay attacks target network security by intercepting and retransmitting valid data packets to gain unauthorized access. Strengthening cyber resilience requires implementing multi-factor authentication, continuous monitoring, and user education to address both social engineering and technical exploitation. Robust encryption protocols and timely software updates further mitigate the risks posed by these distinct attack vectors.
Phishing Attack Infographic
 libterm.com
libterm.com