Message Authentication Code (MAC) is a cryptographic technique that ensures data integrity and authenticity by producing a short tag based on the message and a secret key. It allows you to verify that the message has not been altered and comes from a trusted source, enhancing security in communication systems. Explore the rest of the article to understand how MAC functions and its applications in safeguarding your data.
Table of Comparison
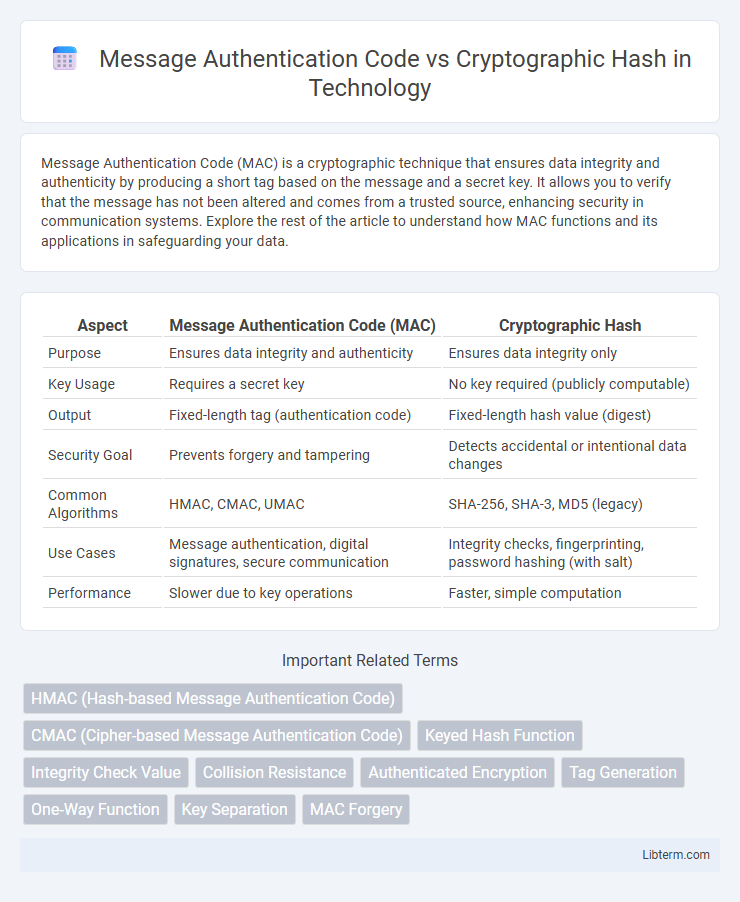
| Aspect | Message Authentication Code (MAC) | Cryptographic Hash |
|---|---|---|
| Purpose | Ensures data integrity and authenticity | Ensures data integrity only |
| Key Usage | Requires a secret key | No key required (publicly computable) |
| Output | Fixed-length tag (authentication code) | Fixed-length hash value (digest) |
| Security Goal | Prevents forgery and tampering | Detects accidental or intentional data changes |
| Common Algorithms | HMAC, CMAC, UMAC | SHA-256, SHA-3, MD5 (legacy) |
| Use Cases | Message authentication, digital signatures, secure communication | Integrity checks, fingerprinting, password hashing (with salt) |
| Performance | Slower due to key operations | Faster, simple computation |
Introduction to Message Authentication Code and Cryptographic Hash
Message Authentication Code (MAC) and Cryptographic Hash serve distinct roles in data security, with MAC providing data integrity and authenticity by combining a secret key with the input data, ensuring only those with the key can verify the message. Cryptographic Hash functions transform input data into a fixed-size hash value, focusing primarily on data integrity by producing a unique fingerprint without requiring a secret key. Understanding these foundational functions is crucial for implementing secure communication protocols that protect against data tampering and unauthorized access.
Understanding Message Authentication Code (MAC)
Message Authentication Code (MAC) provides data integrity and authentication by combining a secret key with the input message to generate a unique fixed-size output, ensuring that only parties with the key can verify the message's authenticity. Unlike cryptographic hash functions, which produce a hash value without a secret key and are vulnerable to certain attacks, MAC resists tampering by verifying both the data and its sender through keyed hashing algorithms like HMAC or CMAC. MAC is essential for secure communication protocols, preventing forgery and replay attacks by confirming the legitimacy of the transmitted message.
What is a Cryptographic Hash Function?
A cryptographic hash function is a mathematical algorithm that transforms input data into a fixed-size string of characters, which appears random and is unique to each unique input. It is designed to be collision-resistant, preimage-resistant, and efficiently computable, ensuring data integrity by detecting any alterations. Unlike Message Authentication Codes (MACs), cryptographic hashes do not use secret keys, making them suitable for verifying data authenticity without confidentiality.
Key Differences Between MAC and Cryptographic Hash
Message Authentication Code (MAC) employs a secret key combined with the input data to generate a unique digest, ensuring both data integrity and authenticity, while Cryptographic Hash functions produce a fixed-size output solely based on input data without requiring a key, providing data integrity but not authentication. MACs prevent forgery by requiring knowledge of the secret key, whereas cryptographic hashes are vulnerable to collision and preimage attacks without key protection. The primary key difference lies in MAC's reliance on shared secret keys for authentication, contrasted with cryptographic hash functions serving as one-way, keyless fingerprint generators.
Use Cases: MAC vs Cryptographic Hash
Message Authentication Codes (MACs) provide data integrity and authenticity by using a secret key, making them ideal for secure communication protocols, digital payments, and authentication systems. Cryptographic hashes generate fixed-length digests from data without keys, serving primarily for data integrity verification, digital signatures, and password hashing. MACs are preferred when verifying both message integrity and sender authenticity, while cryptographic hashes are suited for ensuring data consistency and producing fingerprints in storage or transmission.
Security Implications of MAC and Hash Functions
Message Authentication Codes (MACs) provide data integrity and authentication by using a secret key, making them resilient against forgery even if the attacker knows the hash algorithm, unlike cryptographic hash functions which do not use keys and only ensure data integrity but cannot guarantee authenticity. Cryptographic hash functions like SHA-256 generate fixed-size digests for input data but are vulnerable to length extension and collision attacks that MACs mitigate through keyed mechanisms. The security implications highlight that MACs are essential in environments requiring authentication and strong resistance to tampering, whereas hashes alone are insufficient for preventing active attacks or malicious data modification.
Common Algorithms: Examples of MACs and Hashes
Common Message Authentication Code (MAC) algorithms include HMAC (Hash-based Message Authentication Code), CMAC (Cipher-based MAC), and GMAC (Galois MAC), each designed to ensure data integrity and authenticity using secret keys combined with cryptographic primitives. Widely used cryptographic hash functions include SHA-256, SHA-3, and MD5, which generate fixed-size hash values for verifying data integrity but do not provide authentication on their own. HMAC combines hash functions like SHA-256 with a secret key, distinguishing it from standalone hashes by adding a layer of message authentication.
Performance and Efficiency Comparison
Message Authentication Codes (MACs) typically involve cryptographic hash functions combined with secret keys, resulting in higher computational overhead compared to standalone Cryptographic Hash Functions like SHA-256. In terms of performance, cryptographic hashes generally execute faster due to their simpler construction and absence of key processing, making them more efficient for data integrity verification. However, MACs provide enhanced security through authentication, which justifies their relatively slower performance in scenarios requiring message validation and protection against tampering.
Choosing Between MAC and Cryptographic Hash
Choosing between a Message Authentication Code (MAC) and a cryptographic hash depends on the security requirements of data integrity and authentication. A MAC uses a secret key to provide both data integrity and authenticity, making it ideal for scenarios requiring verification of the sender's identity. Cryptographic hashes, while ensuring data integrity through fixed-length outputs, do not offer authentication and are suited for applications like checksums or fingerprinting where keyless verification is sufficient.
Conclusion: Which Approach to Use When
Message Authentication Codes (MACs) provide data integrity and authentication using a shared secret key, making them essential for verifying data origin in secure communication. Cryptographic hash functions, while efficient for ensuring data integrity, lack authentication and should be used when verifying data consistency without the need for secrecy. Choose MACs for scenarios requiring both integrity and authentication, such as secure message exchange, and rely on cryptographic hashes for integrity checks, digital signatures, or password storage where authentication is not the primary concern.
Message Authentication Code Infographic
 libterm.com
libterm.com