RSA is a widely used public-key cryptographic algorithm that secures data transmission through asymmetric key encryption, relying on the computational difficulty of factoring large prime numbers. It ensures confidentiality, authentication, and digital signatures, making it a cornerstone in modern cybersecurity solutions. Explore the rest of this article to understand how RSA can protect your sensitive information effectively.
Table of Comparison
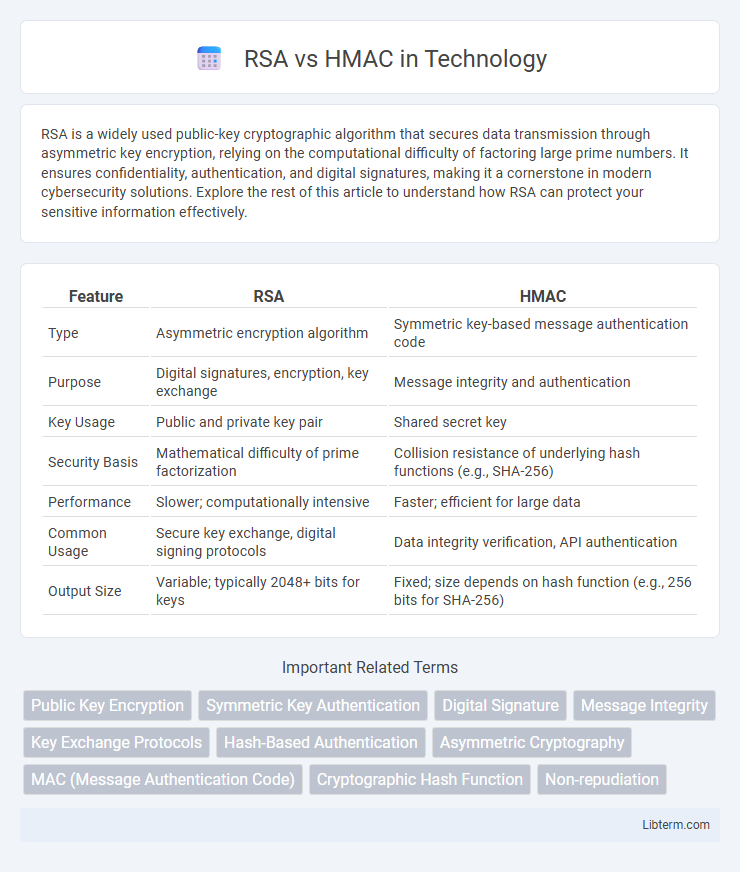
| Feature | RSA | HMAC |
|---|---|---|
| Type | Asymmetric encryption algorithm | Symmetric key-based message authentication code |
| Purpose | Digital signatures, encryption, key exchange | Message integrity and authentication |
| Key Usage | Public and private key pair | Shared secret key |
| Security Basis | Mathematical difficulty of prime factorization | Collision resistance of underlying hash functions (e.g., SHA-256) |
| Performance | Slower; computationally intensive | Faster; efficient for large data |
| Common Usage | Secure key exchange, digital signing protocols | Data integrity verification, API authentication |
| Output Size | Variable; typically 2048+ bits for keys | Fixed; size depends on hash function (e.g., 256 bits for SHA-256) |
Introduction to RSA and HMAC
RSA is an asymmetric cryptographic algorithm widely used for secure data transmission, relying on a pair of public and private keys to enable encryption and digital signatures. HMAC (Hash-based Message Authentication Code) is a symmetric key algorithm that combines a cryptographic hash function with a secret key to ensure data integrity and authentication. Both RSA and HMAC are fundamental to modern cybersecurity but serve different purposes: RSA focuses on secure key exchange and authentication, while HMAC excels in verifying message integrity.
Understanding RSA: A Brief Overview
RSA is a widely-used asymmetric cryptographic algorithm that enables secure data transmission through a pair of keys: a public key for encryption and a private key for decryption. It relies on the mathematical difficulty of factoring large prime numbers, providing strong security for digital signatures and key exchange. This contrasts with HMAC, which is a symmetric algorithm using a shared secret key for message integrity and authentication.
HMAC Explained: How It Works
HMAC (Hash-based Message Authentication Code) uses a cryptographic hash function combined with a secret key to ensure message integrity and authenticity. It works by hashing the original message and the key together in a specific algorithmic process, providing protection against tampering and replay attacks. Unlike RSA, which relies on asymmetric encryption, HMAC is a symmetric mechanism optimized for fast verification and secure communication within shared-key environments.
Key Differences Between RSA and HMAC
RSA uses asymmetric cryptography with a public and private key pair for encryption and digital signatures, while HMAC relies on symmetric cryptography using a single shared secret key for message authentication. RSA provides confidentiality, integrity, and non-repudiation, whereas HMAC primarily ensures data integrity and authentication without encryption. The computational overhead of RSA is higher due to complex key operations, whereas HMAC offers faster performance suitable for verifying data integrity in resource-constrained environments.
Use Cases for RSA in Modern Security
RSA is widely used for securing data transmission through digital signatures and key exchange in SSL/TLS protocols, ensuring authentication and confidentiality over the internet. It enables secure email communication via standards like PGP and S/MIME by facilitating encryption and non-repudiation. RSA's role in identity verification within digital certificates supports secure online transactions and access control in enterprise environments.
HMAC Applications in Data Integrity
HMAC (Hash-based Message Authentication Code) is extensively used in data integrity verification across various applications such as secure API communications, software updates, and digital transactions. It ensures message authenticity and integrity by combining a cryptographic hash function with a secret key, making it resistant to tampering and collision attacks. In contrast to RSA, which is primarily used for digital signatures and encryption, HMAC offers a faster and more efficient solution specifically optimized for verifying data integrity in real-time systems.
Security Strength: RSA vs HMAC
RSA provides security based on the computational difficulty of factoring large prime numbers, making it robust against classical cryptographic attacks but potentially vulnerable to quantum computing advancements. HMAC relies on cryptographic hash functions combined with a secret key, offering strong message integrity and authentication resistant to collision and preimage attacks. While RSA ensures secure asymmetric encryption and digital signatures, HMAC delivers faster, symmetric-key based verification with lower computational overhead and strong resistance to key-recovery attacks.
Performance and Efficiency Comparison
RSA encryption involves complex mathematical operations including large integer factorization, resulting in slower performance compared to HMAC, which uses hash functions optimized for speed and low computational overhead. HMAC delivers higher efficiency in environments requiring fast message authentication due to its symmetric key nature and minimal processing requirements. RSA's computational intensity makes it more suitable for secure key exchange rather than high-throughput data verification tasks where HMAC excels.
Choosing Between RSA and HMAC
Choosing between RSA and HMAC depends on the specific security requirements and use cases such as digital signature verification or message authentication. RSA, as an asymmetric cryptographic algorithm, offers secure key exchange and non-repudiation, making it ideal for scenarios requiring public-key infrastructure. HMAC, a symmetric algorithm relying on shared secret keys, provides faster performance and data integrity, making it suitable for authenticating message integrity in trusted environments.
Conclusion: Which Solution Fits Your Needs?
RSA excels in secure key exchange and digital signatures, making it suitable for scenarios requiring asymmetric encryption and authentication. HMAC offers robust data integrity and authentication using a shared secret, ideal for fast, symmetric key verification in trusted environments. Choosing between RSA and HMAC depends on the need for either asymmetric security features or efficient symmetric protection tailored to your system's requirements.
RSA Infographic
 libterm.com
libterm.com