Spoofing attacks involve impersonating a trusted entity to gain unauthorized access to systems or data, often exploiting weaknesses in authentication protocols. These powerful cyber threats can compromise your personal or organizational information, leading to data breaches or financial loss. Discover more about how spoofing attacks work and strategies to protect yourself in the full article.
Table of Comparison
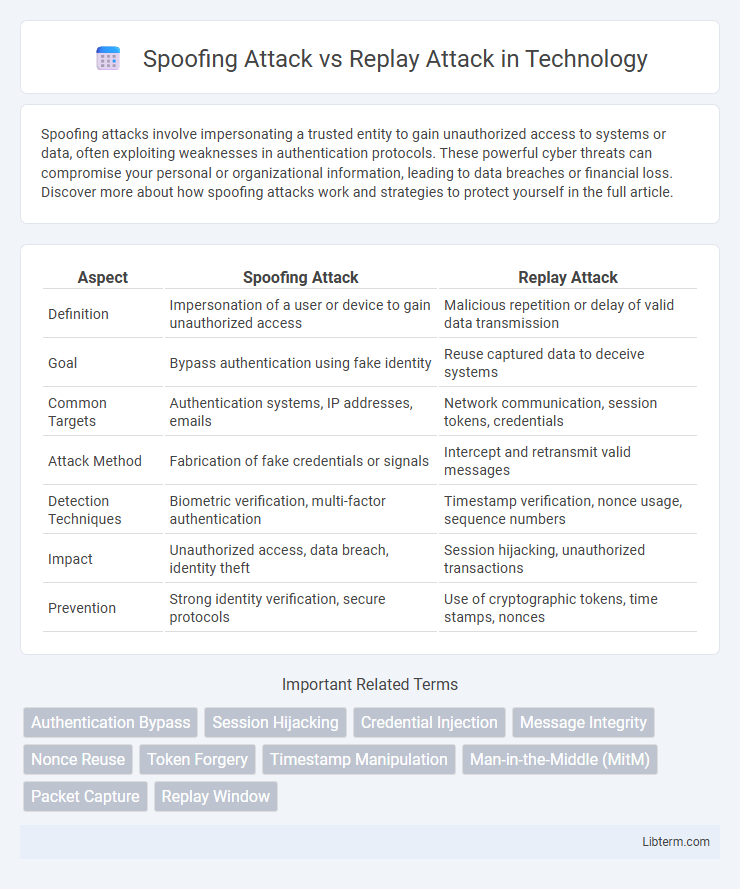
| Aspect | Spoofing Attack | Replay Attack |
|---|---|---|
| Definition | Impersonation of a user or device to gain unauthorized access | Malicious repetition or delay of valid data transmission |
| Goal | Bypass authentication using fake identity | Reuse captured data to deceive systems |
| Common Targets | Authentication systems, IP addresses, emails | Network communication, session tokens, credentials |
| Attack Method | Fabrication of fake credentials or signals | Intercept and retransmit valid messages |
| Detection Techniques | Biometric verification, multi-factor authentication | Timestamp verification, nonce usage, sequence numbers |
| Impact | Unauthorized access, data breach, identity theft | Session hijacking, unauthorized transactions |
| Prevention | Strong identity verification, secure protocols | Use of cryptographic tokens, time stamps, nonces |
Introduction to Cybersecurity Threats
Spoofing attacks involve impersonating a trusted entity by falsifying data, such as IP addresses or email headers, to gain unauthorized access or steal sensitive information. Replay attacks capture and retransmit valid data transmissions, exploiting the lack of proper authentication or encryption to deceive systems into granting access repeatedly. Both threats undermine cybersecurity by exploiting trust mechanisms, necessitating robust authentication protocols and encryption to mitigate risk.
What is a Spoofing Attack?
A spoofing attack involves impersonating a trusted entity by falsifying data to gain unauthorized access or deceive systems. This type of attack manipulates identity information such as IP addresses, email headers, or user credentials to masquerade as a legitimate source. Spoofing attacks are commonly used to bypass security measures and launch further exploits within networks or communication channels.
How Spoofing Attacks Work
Spoofing attacks involve impersonating a legitimate user or device by falsifying data, such as IP addresses, email headers, or biometric information, to gain unauthorized access or manipulate systems. Attackers intercept or fabricate communication signals, tricking systems into believing the source is trusted. This technique exploits vulnerabilities in authentication protocols to bypass security measures and compromise confidentiality or integrity.
Types of Spoofing Attacks
Spoofing attacks encompass several types, including IP spoofing, where attackers forge IP addresses to impersonate trusted sources; email spoofing, used to deceive recipients by falsifying sender information; and DNS spoofing, which redirects traffic to malicious sites by altering DNS records. In contrast, replay attacks capture and retransmit valid data packets to gain unauthorized access or disrupt communications, often exploiting vulnerabilities in authentication protocols. Understanding these spoofing techniques is crucial for implementing robust cybersecurity measures to protect network integrity and data confidentiality.
What is a Replay Attack?
A replay attack involves an attacker capturing valid data transmissions and retransmitting them to deceive a system into unauthorized actions. Unlike spoofing attacks, which involve impersonation by falsifying credentials or identities, replay attacks exploit previously captured data to gain access or disrupt communications. This attack is common in network security where authentication messages or transaction codes are intercepted and reused to bypass security mechanisms.
How Replay Attacks Operate
Replay attacks operate by intercepting and capturing valid data transmissions, then maliciously retransmitting them to deceive the receiver into performing unauthorized actions. Unlike spoofing attacks that impersonate a legitimate user or device, replay attacks rely on the repetition of previously transmitted messages to exploit authentication or transaction processes. This method targets vulnerabilities in communication protocols lacking robust time-stamping or nonce mechanisms to prevent message reuse.
Key Differences Between Spoofing and Replay Attacks
Spoofing attacks involve impersonating a legitimate entity by falsifying data to gain unauthorized access, while replay attacks capture and retransmit valid data packets to duplicate legitimate communication. Spoofing targets identity deception at the source, often manipulating IP addresses or credentials, whereas replay attacks target the integrity and timing by resending intercepted messages without modification. The primary difference lies in spoofing's focus on creating false identity versus replay's emphasis on exploiting the reuse of authentic message sequences.
Real-World Examples of Both Attacks
A spoofing attack involves impersonating a trusted entity to gain unauthorized access, such as an attacker using a fake email address to deceive employees in a phishing scam at a financial firm. Replay attacks occur when valid data transmissions are intercepted and retransmitted by an attacker, exemplified by fraudsters capturing and re-sending payment information in contactless card transactions to duplicate payments. Both attack types have been documented in high-profile breaches, including the 2019 City of Baltimore ransomware incident linked to spoofed email credentials and the 2017 Tesla Model S key fob replay attack exploited by hackers to steal vehicles.
Prevention and Mitigation Strategies
Spoofing attacks can be prevented by implementing strong authentication techniques such as multi-factor authentication (MFA) and cryptographic methods like digital signatures to verify the identity of users and devices. Replay attacks require mitigation through the use of nonce values, timestamps, and session tokens to ensure message freshness and prevent retransmission of captured data. Employing encryption protocols like TLS and secure communication channels further strengthens defense by protecting data integrity and confidentiality against both spoofing and replay attempts.
Conclusion: Strengthening Cyber Defenses
Spoofing attacks manipulate identity information to gain unauthorized access, while replay attacks exploit captured data to execute fraudulent transactions. Strengthening cyber defenses requires implementing multi-factor authentication, robust encryption, and real-time monitoring to detect and prevent both attack types effectively. Integrating these security measures reduces vulnerability and enhances protection against identity-based and data exploitation threats.
Spoofing Attack Infographic
 libterm.com
libterm.com