Configuration management ensures that your IT systems and software remain consistent, reliable, and secure by tracking and controlling changes throughout their lifecycle. This process minimizes errors, improves system integrity, and enhances collaboration among teams. Discover how effective configuration management can optimize your workflows and safeguard your infrastructure in the rest of this article.
Table of Comparison
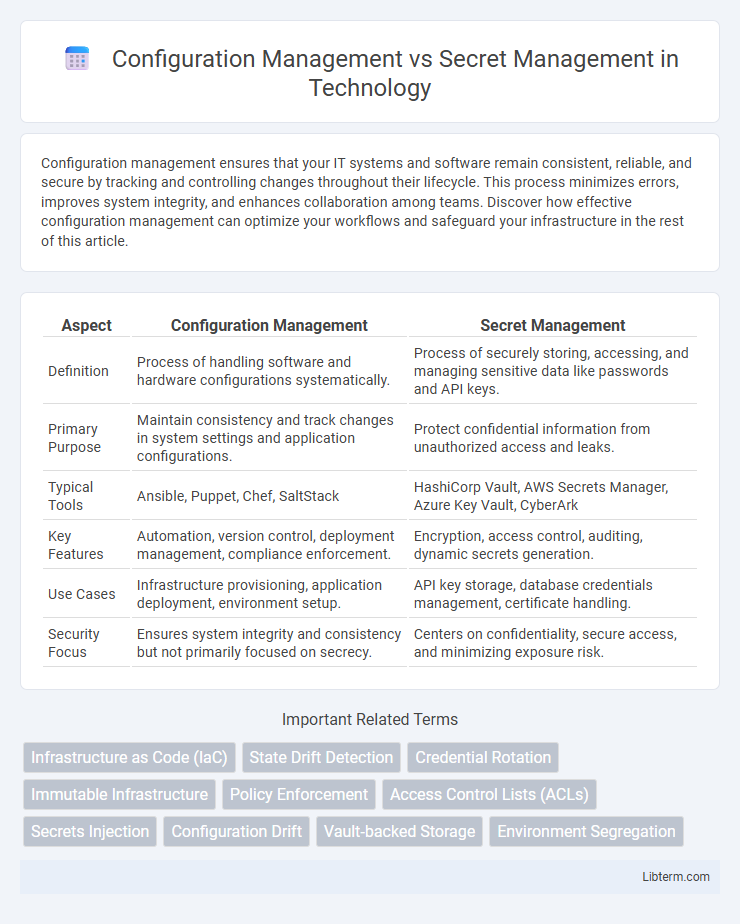
| Aspect | Configuration Management | Secret Management |
|---|---|---|
| Definition | Process of handling software and hardware configurations systematically. | Process of securely storing, accessing, and managing sensitive data like passwords and API keys. |
| Primary Purpose | Maintain consistency and track changes in system settings and application configurations. | Protect confidential information from unauthorized access and leaks. |
| Typical Tools | Ansible, Puppet, Chef, SaltStack | HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, CyberArk |
| Key Features | Automation, version control, deployment management, compliance enforcement. | Encryption, access control, auditing, dynamic secrets generation. |
| Use Cases | Infrastructure provisioning, application deployment, environment setup. | API key storage, database credentials management, certificate handling. |
| Security Focus | Ensures system integrity and consistency but not primarily focused on secrecy. | Centers on confidentiality, secure access, and minimizing exposure risk. |
Introduction to Configuration Management and Secret Management
Configuration Management involves systematically handling and maintaining software settings, infrastructure setups, and environment parameters to ensure consistency and traceability across development, testing, and production environments. Secret Management focuses on securely storing, accessing, and distributing sensitive information such as API keys, passwords, certificates, and tokens, minimizing the risk of unauthorized exposure. Both practices are essential for robust application deployment and operational security, with Configuration Management optimizing environment reproducibility and Secret Management safeguarding critical credentials.
Key Differences Between Configuration and Secret Management
Configuration management involves maintaining and organizing system settings and software configurations to ensure consistency and control across environments, while secret management specifically handles sensitive data such as passwords, API keys, and certificates with enhanced security measures. Configuration management tools focus on version control, automation, and environment consistency, whereas secret management platforms prioritize encryption, access control, and secure secret distribution. The key difference lies in the nature of the data managed: configuration data is generally non-sensitive and aimed at system operation, whereas secrets require stringent confidentiality and protection against unauthorized access.
Core Principles of Configuration Management
Configuration management emphasizes maintaining consistency of system performance, functional requirements, and physical attributes throughout its lifecycle by systematically controlling configurations. Core principles include version control, change management, and environment consistency, ensuring that configurations are documented, monitored, and reproducible. Secret management focuses on securing sensitive data such as passwords and API keys, distinct from configuration management's focus on overall system state and integrity.
Core Principles of Secret Management
Secret management centers on securely storing, distributing, and accessing sensitive credentials like API keys, passwords, and encryption keys using encryption, access controls, and audit logs. Configuration management handles provisioning and maintaining system settings and software configurations to ensure consistency and reliability. Core principles of secret management include confidentiality, integrity, controlled access, regular rotation, and secure transmission to minimize exposure risks and prevent unauthorized access.
Common Use Cases for Configuration Management
Configuration management streamlines the consistent deployment and updates of software environments by managing settings, infrastructure details, and system parameters across multiple servers. Common use cases include automating environment setups, ensuring configuration consistency during continuous integration and deployment (CI/CD), and tracking changes in infrastructure as code (IaC) repositories. This approach reduces human errors, facilitates compliance, and supports scalable, repeatable infrastructure provisioning.
Typical Scenarios for Secret Management
Secret management is crucial in scenarios involving secure storage and retrieval of sensitive information such as API keys, passwords, and encryption tokens within cloud environments, containerized applications, and microservices architectures. It ensures access control, auditing, and automatic rotation of secrets to prevent unauthorized access and reduce security risks. Unlike configuration management, which handles application settings and environment variables, secret management deals specifically with protecting credentials and confidential data throughout the software development lifecycle.
Benefits of Separating Configuration and Secret Management
Separating configuration management and secret management enhances security by isolating sensitive credentials from application settings, reducing the risk of unauthorized access or leaks. It improves operational efficiency by enabling distinct access controls, auditing processes, and lifecycle management tailored to non-sensitive configurations and secret data. This division supports compliance with regulatory standards by ensuring that secrets receive specialized protection measures while configurations remain easily accessible for application deployment and scaling.
Security Implications: Configuration vs Secret Handling
Configuration management involves handling application settings and environment variables that are generally non-sensitive, whereas secret management focuses on safeguarding sensitive information such as API keys, passwords, and certificates. Proper secret handling requires encryption, strict access controls, and audit logging to prevent unauthorized access and leakage, reducing the risk of security breaches. Mismanaging secrets in configuration files can lead to exposure vulnerabilities, making it critical to separate secret storage from general configuration to enhance overall system security.
Tools and Technologies for Configuration and Secret Management
Configuration management tools like Ansible, Puppet, and Chef automate infrastructure provisioning and enforce system state consistency, enabling efficient control over software environments. Secret management solutions such as HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault specialize in securely storing, accessing, and rotating sensitive information like API keys, passwords, and certificates. Integrating configuration management with secret management tools enhances security by decoupling sensitive data from configuration files while maintaining seamless deployment workflows.
Best Practices for Managing Configurations and Secrets
Effective configuration management involves maintaining version-controlled, environment-specific configuration files to ensure consistency and traceability across deployments. Secret management requires utilizing dedicated vaults or key management services with strict access controls, encryption at rest and in transit, and automated rotation policies to minimize exposure risks. Both practices demand integration with CI/CD pipelines and monitoring tools to detect unauthorized changes and ensure compliance with security standards.
Configuration Management Infographic
 libterm.com
libterm.com