Signal offers end-to-end encryption for secure messaging, ensuring your conversations remain private from hackers and third parties. Its open-source technology and minimal data collection make it a trusted choice for privacy-conscious users worldwide. Explore the full article to discover how Signal can enhance your digital security.
Table of Comparison
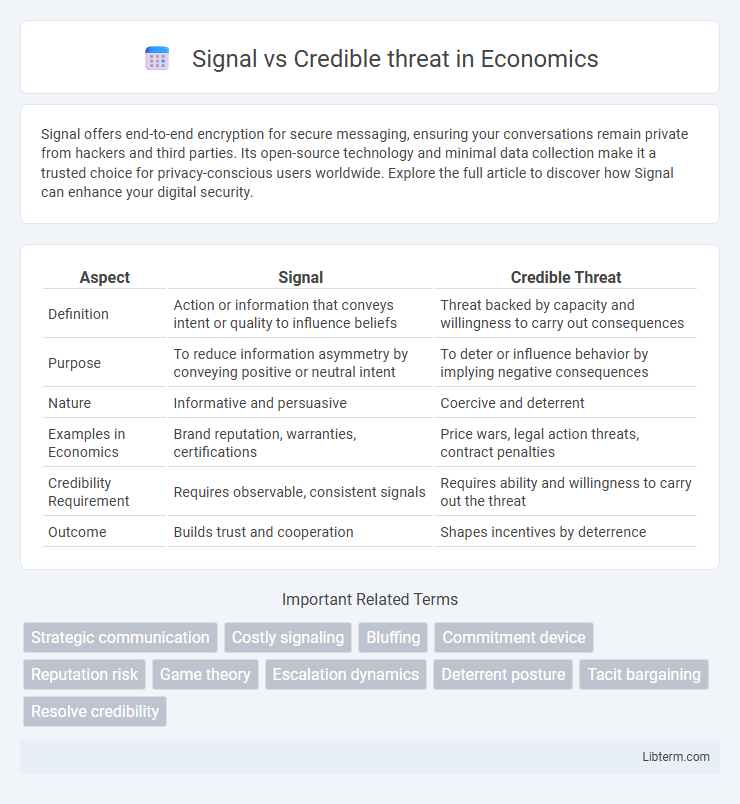
| Aspect | Signal | Credible Threat |
|---|---|---|
| Definition | Action or information that conveys intent or quality to influence beliefs | Threat backed by capacity and willingness to carry out consequences |
| Purpose | To reduce information asymmetry by conveying positive or neutral intent | To deter or influence behavior by implying negative consequences |
| Nature | Informative and persuasive | Coercive and deterrent |
| Examples in Economics | Brand reputation, warranties, certifications | Price wars, legal action threats, contract penalties |
| Credibility Requirement | Requires observable, consistent signals | Requires ability and willingness to carry out the threat |
| Outcome | Builds trust and cooperation | Shapes incentives by deterrence |
Understanding Signals and Credible Threats
Understanding signals involves recognizing subtle cues or behaviors that indicate potential future actions, while a credible threat constitutes a clear and believable intention to cause harm or enforce consequences. Signals often serve as preliminary indicators that require further assessment to determine their seriousness, whereas credible threats demand immediate attention due to their demonstrated capability and intent. Distinguishing between these ensures appropriate responses in security, negotiations, and conflict resolution scenarios.
Defining Signal and Credible Threat
A signal refers to any observable action or indicator that conveys information or intent, often used to influence the behavior of others without explicit communication. A credible threat is a specific type of signal that convincingly demonstrates the capability and willingness to cause harm or negative consequences, making the threat believable and actionable. Distinguishing between a general signal and a credible threat involves assessing both the plausibility and the seriousness of the intended action conveyed.
Key Differences Between Signals and Credible Threats
Signals are nonverbal or verbal indicators intended to convey intentions or feelings without explicit threat, often ambiguous and open to interpretation. Credible threats are explicit, well-founded warnings of harm or consequences that the receiver believes likely to be executed based on evidence or context. The key difference lies in the clarity and believability of the threat, with credible threats compelling action due to their perceived legitimacy, whereas signals merely suggest potential intent without assured follow-through.
Real-World Examples of Signals and Credible Threats
A signal indicating a potential threat can be observed in social media posts expressing frustration or unusual behavior, such as a student sharing violent content online before an incident occurs. A credible threat involves specific, direct statements or actions, like a person making explicit plans to harm a location or individual, for instance, a detailed threat to bomb a school discovered through intercepted communications. Law enforcement agencies rely on contextual analysis and corroborating evidence to differentiate between general signals and actionable credible threats to prevent violence effectively.
The Role of Intent in Signals vs Credible Threats
Signals represent intentional actions or communications designed to convey information or influence perceptions without immediate coercion, often serving as strategic tools in diplomacy or negotiations. Credible threats involve explicit intentions to carry out harmful actions if demands are not met, where the intent to follow through is clear and believed by the target. The differentiation centers on the clarity and seriousness of intent; signals imply potential future actions, whereas credible threats confirm a definitive commitment to act.
Impact on Decision-Making: Signals vs Credible Threats
Signals provide indirect cues that influence decision-making by shaping perceptions and expectations, often requiring interpretation and context analysis to assess their relevance. Credible threats, characterized by clear intent and capability, directly impact decisions by increasing the perceived risk and urgency, prompting more immediate and definitive responses. Understanding the distinction between subtle signals and explicit credible threats is crucial for accurate risk assessment and strategic planning in decision-making processes.
Strategic Use of Signals and Credible Threats
Strategic use of signals involves clear, observable actions or communications designed to influence an opponent's perception and decision-making without direct confrontation. Credible threats require demonstrable capability and commitment to act, ensuring the opponent believes that non-compliance will result in tangible consequences. Effectiveness in conflict resolution relies on aligning signals with genuinely enforceable threats to manipulate the adversary's cost-benefit analysis.
Detecting Credible Threats Among Multiple Signals
Detecting credible threats among multiple signals requires advanced analytical techniques that prioritize context, source reliability, and behavioral patterns. Effective threat assessment systems integrate real-time data from diverse platforms, employing machine learning algorithms to distinguish between false alarms and genuine risks. Enhanced signal fusion and cross-referencing of intelligence improve accuracy in identifying actionable threats, minimizing response time and resource wastage.
Psychological Factors in Signal Interpretation
Psychological factors significantly influence the interpretation of signals versus credible threats, as cognitive biases like confirmation bias and threat exaggeration can distort perception and response. The amygdala's role in processing fear may cause individuals to overestimate the danger presented by ambiguous signals, leading to false alarms. Understanding these psychological mechanisms enhances threat assessment accuracy and reduces misinterpretation in security contexts.
Preventing Misinterpretation: Best Practices for Differentiation
Clear indicators such as specific wording, context, and intent are crucial for differentiating between a signal and a credible threat to prevent misinterpretation. Employing standardized threat assessment frameworks and continuous training for personnel enhances the accuracy of identifying genuine threats versus ambiguous signals. Leveraging advanced analytical tools alongside human judgment further reduces false positives and strengthens overall security protocols.
Signal Infographic
 libterm.com
libterm.com