A Demilitarized Zone (DMZ) in computer networking acts as a secure buffer zone between an internal network and untrusted external networks, such as the internet. It hosts public-facing services like web servers and email servers to prevent direct access to your private network, enhancing security against cyber threats. Explore the full article to understand how implementing a DMZ can safeguard your network infrastructure effectively.
Table of Comparison
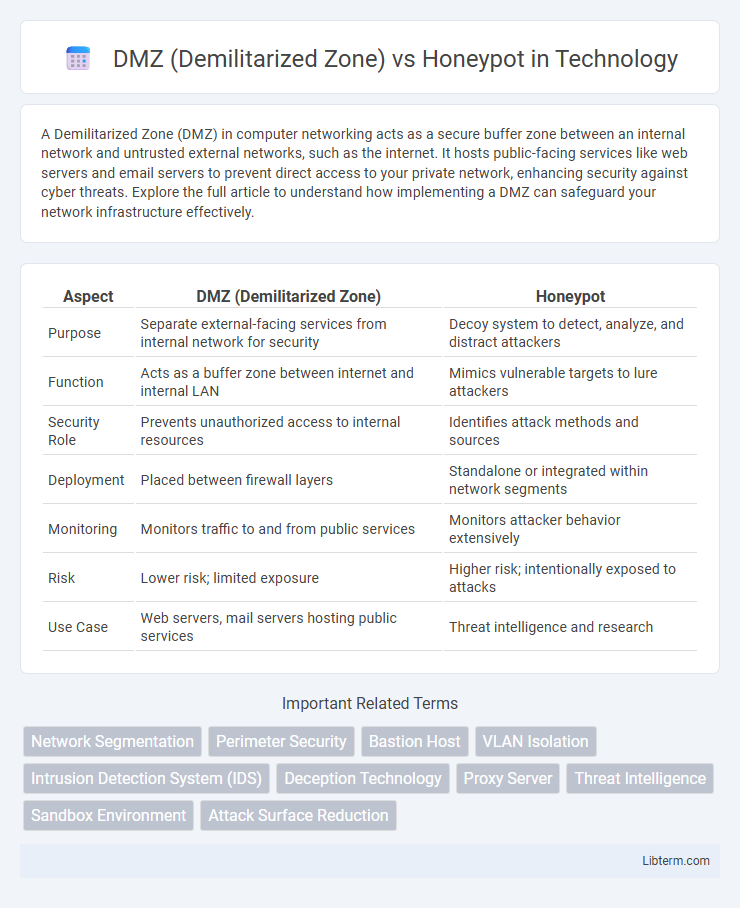
| Aspect | DMZ (Demilitarized Zone) | Honeypot |
|---|---|---|
| Purpose | Separate external-facing services from internal network for security | Decoy system to detect, analyze, and distract attackers |
| Function | Acts as a buffer zone between internet and internal LAN | Mimics vulnerable targets to lure attackers |
| Security Role | Prevents unauthorized access to internal resources | Identifies attack methods and sources |
| Deployment | Placed between firewall layers | Standalone or integrated within network segments |
| Monitoring | Monitors traffic to and from public services | Monitors attacker behavior extensively |
| Risk | Lower risk; limited exposure | Higher risk; intentionally exposed to attacks |
| Use Case | Web servers, mail servers hosting public services | Threat intelligence and research |
Introduction to DMZ and Honeypot
A DMZ (Demilitarized Zone) is a network segment that acts as a buffer zone between an organization's internal network and untrusted external networks, designed to expose external-facing services while protecting internal systems from direct access. A honeypot is a decoy system or network resource intentionally designed to attract attackers, enabling security teams to detect, analyze, and mitigate threats by luring malicious activities away from legitimate targets. Both DMZs and honeypots enhance network security but differ in purpose: the DMZ controls and filters traffic flow, while honeypots serve as traps to study attacker behavior.
What is a DMZ (Demilitarized Zone)?
A DMZ (Demilitarized Zone) is a physical or logical subnetwork that separates an internal local area network (LAN) from untrusted external networks, typically the internet, enhancing security by isolating public-facing services. It hosts external-facing servers such as web, email, and DNS servers to provide controlled access while protecting the internal network from direct exposure. Unlike a honeypot, which is designed to lure and analyze attackers, a DMZ acts as a buffer zone that restricts unauthorized access and limits potential damage from external threats.
What is a Honeypot in Cybersecurity?
A honeypot in cybersecurity is a security mechanism designed to lure attackers by mimicking vulnerable systems or data to detect, analyze, and study cyber threats. Unlike a DMZ, which acts as a buffer zone between a private network and the internet to prevent unauthorized access, a honeypot serves as a decoy to divert cybercriminals, allowing security teams to gather intelligence on attack methods and behaviors. Honeypots effectively enhance threat detection and incident response by providing real-time monitoring of attacker activities.
Key Differences: DMZ vs Honeypot
DMZ (Demilitarized Zone) serves as a neutral network segment that isolates external-facing services like web servers from the internal network, enhancing security by limiting direct access. Honeypots are decoy systems designed to attract, detect, and analyze cyber attackers by mimicking vulnerable targets, thereby providing threat intelligence. Unlike DMZs that protect legitimate assets by segregation, honeypots act as traps to study attacker behavior and identify new attack methods.
Core Functions of a DMZ
A DMZ (Demilitarized Zone) serves as a buffer zone between an organization's internal network and untrusted external networks, primarily designed to host public-facing services like web, mail, and DNS servers while preventing external threats from directly reaching internal systems. It controls traffic through strict firewall rules, allowing external users limited access to specific resources without exposing sensitive internal assets. Unlike a honeypot, which functions as a decoy to detect and analyze attacks, the core function of a DMZ is to enhance security by segregating and shielding critical network segments from unauthorized access.
Main Purposes of Deploying a Honeypot
Honeypots are deployed primarily to detect, analyze, and gather intelligence on cyber threats by intentionally attracting attackers to a controlled environment, enabling organizations to study attack methods and behavior without risking critical assets. Unlike a DMZ, which functions as a separated network segment to expose external-facing services while protecting internal systems, honeypots serve as decoys designed to mislead attackers and provide early warning of intrusion attempts. The main purposes of deploying a honeypot include threat detection, vulnerability assessment, attack pattern analysis, and enhancing overall cybersecurity posture through proactive deception.
Security Benefits of DMZs
A DMZ (Demilitarized Zone) enhances network security by isolating public-facing services from the internal network, reducing the risk of unauthorized access to sensitive data. This segmented architecture ensures that even if an attacker compromises the DMZ, the core internal network remains protected by additional firewalls. Compared to honeypots, which serve primarily as deception tools to detect and analyze attacks, DMZs provide foundational perimeter security that limits attack surface exposure and enforces strict access control policies.
Security Benefits of Honeypots
Honeypots enhance cybersecurity by actively attracting and isolating attackers, allowing security teams to monitor malicious behavior without risking critical systems, unlike DMZs which primarily serve as a controlled buffer zone. By simulating vulnerabilities, honeypots deceive attackers, providing early threat detection and valuable intelligence to improve defenses. This proactive approach reduces the risk of data breaches and helps organizations understand attacker techniques in real-time.
When to Use a DMZ vs a Honeypot
A DMZ (Demilitarized Zone) is best used when isolating public-facing servers from the internal network to enhance security and control external access. A honeypot is ideal for detecting, analyzing, and deceiving attackers by simulating vulnerable systems within the network environment. Deploy a DMZ for perimeter defense and a honeypot for threat intelligence and proactive intrusion detection.
Best Practices for Implementing DMZs and Honeypots
Implementing a DMZ involves strategically placing public-facing servers between untrusted external networks and the internal network to limit attack surfaces, enforcing strict firewall rules and segmentation to control traffic flow. Honeypots require deploying isolated, decoy systems designed to attract and analyze attacker behavior without exposing critical assets, using real-time monitoring and logging for threat intelligence. Best practices emphasize continuous updates, effective network segmentation, and robust incident response plans to maximize security benefits from both DMZs and honeypots.
DMZ (Demilitarized Zone) Infographic
 libterm.com
libterm.com