Gold Team represents elite expertise and exceptional performance in competitive environments, often excelling through strategic coordination and advanced skills. Members of Gold Team are typically trusted with high-stakes missions or projects, showcasing leadership and innovation. Explore the rest of the article to uncover how Gold Team's principles can elevate your success.
Table of Comparison
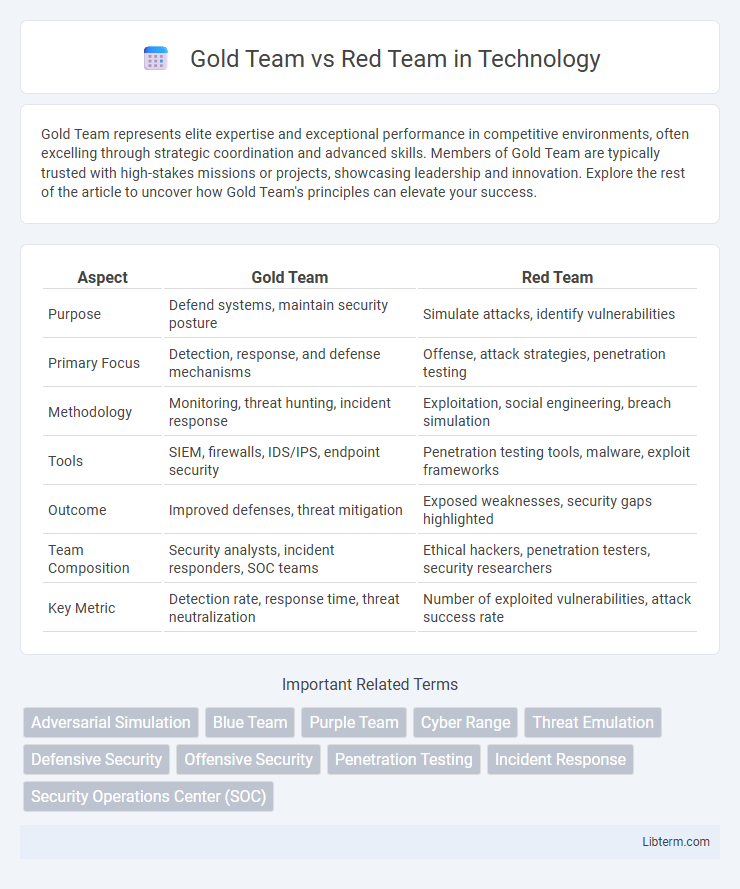
| Aspect | Gold Team | Red Team |
|---|---|---|
| Purpose | Defend systems, maintain security posture | Simulate attacks, identify vulnerabilities |
| Primary Focus | Detection, response, and defense mechanisms | Offense, attack strategies, penetration testing |
| Methodology | Monitoring, threat hunting, incident response | Exploitation, social engineering, breach simulation |
| Tools | SIEM, firewalls, IDS/IPS, endpoint security | Penetration testing tools, malware, exploit frameworks |
| Outcome | Improved defenses, threat mitigation | Exposed weaknesses, security gaps highlighted |
| Team Composition | Security analysts, incident responders, SOC teams | Ethical hackers, penetration testers, security researchers |
| Key Metric | Detection rate, response time, threat neutralization | Number of exploited vulnerabilities, attack success rate |
Introduction to Gold Team and Red Team
Gold Team and Red Team represent distinct cybersecurity roles within an organization's defense strategy. The Gold Team focuses on maintaining and enhancing the security framework through proactive measures, policy development, and system hardening to prevent attacks. In contrast, the Red Team simulates adversarial tactics by conducting realistic cyberattacks to identify vulnerabilities and test the organization's defensive capabilities.
Defining the Roles: Gold Team vs Red Team
The Gold Team specializes in defensive cybersecurity measures, responsible for monitoring, incident response, and strengthening an organization's security posture against threats. The Red Team conducts offensive operations by simulating real-world cyberattacks to identify vulnerabilities and test the effectiveness of security controls. Both teams collaborate to enhance overall security resilience, with the Gold Team defending and the Red Team challenging existing defenses.
Key Objectives of Gold Team and Red Team
Gold Team focuses on strategic defense by enhancing security measures, monitoring network infrastructures, and responding swiftly to cyber threats to protect critical assets. Red Team aims to simulate realistic cyberattacks, identifying vulnerabilities through penetration testing and social engineering to improve the organization's overall security posture. Both teams collaborate to ensure robust cybersecurity by continuously testing and strengthening defenses against evolving threats.
Skills and Expertise: Gold Team vs Red Team
Gold Team members excel in advanced threat detection, incident response, and forensic analysis, leveraging expertise in network security and malware reverse engineering. Red Team specialists focus on offensive tactics, including penetration testing, social engineering, and vulnerability exploitation to simulate real-world cyberattacks. Both teams demonstrate complementary skills essential for comprehensive cybersecurity defense and continuous system improvement.
Tools and Techniques Used by Both Teams
Gold Teams utilize advanced threat hunting tools like MITRE ATT&CK framework integration, AI-driven analytics platforms, and proprietary red teaming toolkits to simulate sophisticated attacks. Red Teams primarily deploy penetration testing tools such as Metasploit, Cobalt Strike, and custom exploit scripts to mimic real-world adversaries and identify security weaknesses. Both teams leverage automated vulnerability scanners, social engineering techniques, and network traffic analyzers to enhance their attack simulations and defense testing effectiveness.
Gold Team Responsibilities Explained
Gold Team bears the critical responsibility of providing strategic oversight and resource allocation during security operations, ensuring all actions align with organizational objectives. This team monitors incident responses, coordinates communication between stakeholders, and validates decision-making processes to maintain operational efficiency. Their primary role encompasses governance, risk management, and enforcing compliance standards to support effective cyber defense.
Red Team Responsibilities Explained
Red Team responsibilities encompass simulating real-world cyber attacks to identify security vulnerabilities, testing an organization's defenses from an adversary's perspective. They conduct penetration testing, social engineering, and vulnerability assessments to expose weaknesses in systems, networks, and human behavior. By providing actionable intelligence and detailed reports, the Red Team enables security teams to strengthen defenses and improve incident response strategies.
Collaboration Between Gold Team and Red Team
The collaboration between Gold Team and Red Team enhances cybersecurity by combining proactive defense strategies with rigorous penetration testing to identify vulnerabilities before adversaries exploit them. Continuous communication and shared insights enable both teams to adapt quickly to evolving threats, improving incident response times and overall security posture. Utilizing joint simulations and threat intelligence sharing fosters a resilient environment where defensive measures are continuously refined and validated against realistic attack scenarios.
Real-World Scenarios: Gold Team vs Red Team
Gold Team and Red Team exercises simulate real-world cybersecurity scenarios to enhance organizational defense mechanisms. Gold Teams focus on maintaining and improving security infrastructure, while Red Teams emulate sophisticated adversaries to identify vulnerabilities through penetration testing. This dynamic interaction drives continuous security improvements and preparedness against evolving cyber threats.
Best Practices for Effective Security Team Operations
Gold Team and Red Team operations focus on optimizing cybersecurity defenses and threat simulation to enhance organizational security posture. Best practices include establishing clear communication protocols, defining roles and objectives precisely, and conducting regular joint exercises to identify and address vulnerabilities effectively. Integrating continuous feedback loops and leveraging advanced threat intelligence platforms ensures proactive risk mitigation and seamless collaboration between teams.
Gold Team Infographic
 libterm.com
libterm.com