Phishing is a cyberattack method where malicious actors impersonate trusted entities to steal sensitive information such as passwords and credit card numbers. Recognizing common phishing tactics and understanding how to protect your personal data can significantly reduce the risk of falling victim to these scams. Dive into the rest of this article to learn how to safeguard yourself against phishing threats effectively.
Table of Comparison
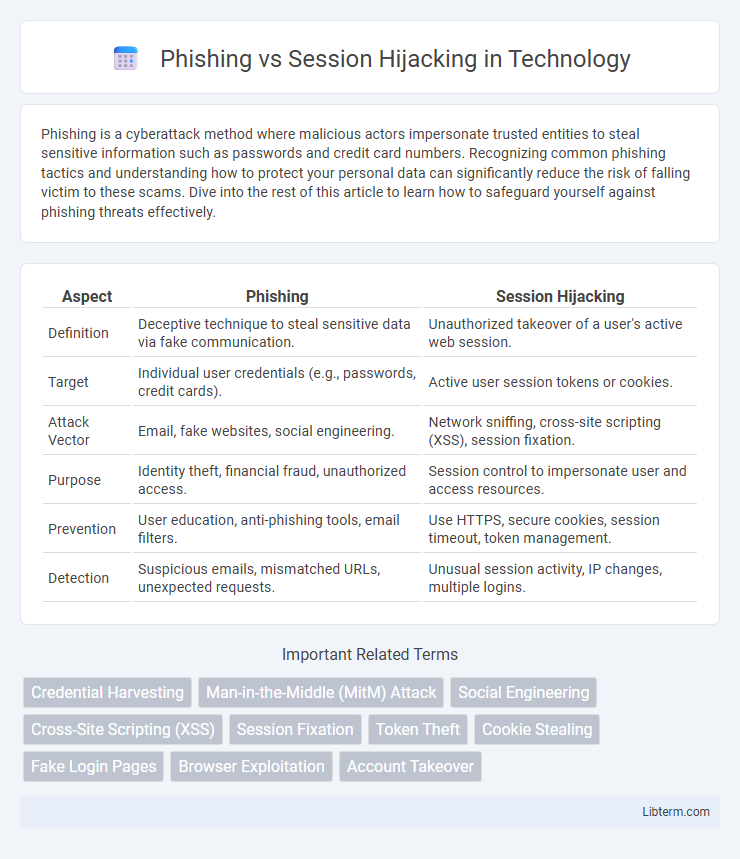
| Aspect | Phishing | Session Hijacking |
|---|---|---|
| Definition | Deceptive technique to steal sensitive data via fake communication. | Unauthorized takeover of a user's active web session. |
| Target | Individual user credentials (e.g., passwords, credit cards). | Active user session tokens or cookies. |
| Attack Vector | Email, fake websites, social engineering. | Network sniffing, cross-site scripting (XSS), session fixation. |
| Purpose | Identity theft, financial fraud, unauthorized access. | Session control to impersonate user and access resources. |
| Prevention | User education, anti-phishing tools, email filters. | Use HTTPS, secure cookies, session timeout, token management. |
| Detection | Suspicious emails, mismatched URLs, unexpected requests. | Unusual session activity, IP changes, multiple logins. |
Introduction to Phishing and Session Hijacking
Phishing involves cybercriminals using deceptive emails or websites to trick users into revealing sensitive information like passwords or credit card numbers. Session hijacking occurs when attackers take control of a user's active session by stealing session cookies, allowing unauthorized access to web applications without needing login credentials. Both techniques exploit trust but differ in approach: phishing targets user information directly, while session hijacking exploits existing authentication.
Defining Phishing: Methods and Attack Vectors
Phishing is a cyberattack method that uses deceptive emails, fake websites, or messages to trick users into revealing sensitive information such as usernames, passwords, or financial data. Common attack vectors include spear-phishing, where targeted individuals receive personalized messages, and clone phishing, which involves replicating legitimate emails with malicious links. These tactics exploit human trust by mimicking reputable sources to gain unauthorized access or credentials.
Understanding Session Hijacking Techniques
Session hijacking techniques exploit vulnerabilities in web session management, allowing attackers to intercept or predict session tokens to gain unauthorized access. Common methods include session fixation, where an attacker sets a known session ID, and session sidejacking, which captures session cookies via unsecured networks. Advanced techniques involve cross-site scripting (XSS) to steal session information or man-in-the-middle (MITM) attacks to eavesdrop and manipulate active sessions.
Key Differences Between Phishing and Session Hijacking
Phishing involves tricking users into revealing sensitive information through deceptive emails or websites, targeting user credentials directly. Session hijacking exploits active sessions by stealing or manipulating session tokens to gain unauthorized access without needing login details. The key difference lies in phishing attacking user trust to acquire credentials, while session hijacking targets communication channels to bypass authentication.
Common Indicators of Phishing Attacks
Phishing attacks commonly exhibit indicators such as suspicious URLs that mimic legitimate websites, unsolicited emails requesting sensitive information, and urgent or alarming messages designed to provoke quick reactions. Attackers often use poor grammar, generic greetings, and unexpected attachments or links to deceive victims. Recognizing these signs helps differentiate phishing attempts from session hijacking, which involves exploiting active sessions rather than deceptive messaging.
Warning Signs of Session Hijacking
Suspicious login activities and unexpected account changes frequently indicate session hijacking, with attackers exploiting stolen session tokens to gain unauthorized access. Users might experience sudden logouts, multiple simultaneous sessions, or unfamiliar IP addresses accessing their accounts, which are critical warning signs. Monitoring session behavior and implementing multi-factor authentication significantly reduce the risk and impact of session hijacking attacks.
Real-World Examples: Phishing vs Session Hijacking
Phishing attacks often exploit fake emails or websites to steal credentials, as seen in the 2016 Democratic National Committee breach where spear-phishing compromised email accounts. Session hijacking occurs when attackers intercept or steal active session tokens, exemplified by the Firesheep browser extension in 2010, which allowed attackers to capture unencrypted Wi-Fi sessions. Both methods result in unauthorized access but differ in technique, with phishing relying on social engineering and session hijacking leveraging technical interception.
Impact and Consequences of Each Attack
Phishing attacks primarily result in unauthorized access to sensitive personal or financial information, leading to identity theft, financial loss, and compromised user credentials. Session hijacking exploits active user sessions to gain illicit access to web applications, often resulting in data breaches, unauthorized transactions, and loss of user trust. Both attacks severely impact organizational security, but session hijacking can cause immediate operational disruption, while phishing often facilitates longer-term infiltration.
Prevention Strategies for Phishing and Session Hijacking
Preventing phishing involves implementing multi-factor authentication (MFA), educating users on recognizing suspicious emails, and deploying advanced email filtering solutions. Session hijacking prevention relies on using secure HTTPS connections, employing session timeouts, and ensuring tokens are encrypted and regenerated frequently. Regular software updates and robust firewall configurations also enhance defense against both phishing attacks and session hijacking attempts.
Conclusion: Strengthening Cybersecurity Awareness
Strengthening cybersecurity awareness is crucial to defend against phishing and session hijacking, as both exploit user vulnerabilities through deceptive tactics and unauthorized access. Educating users about recognizing suspicious emails, securing login credentials, and implementing multi-factor authentication significantly reduces risks. Continuous training and up-to-date threat intelligence empower organizations to prevent data breaches and protect sensitive information effectively.
Phishing Infographic
 libterm.com
libterm.com