Authentication verifies your identity to grant secure access to systems, applications, or data, ensuring only authorized users can enter. Common methods include passwords, biometric scans, and multi-factor authentication, each enhancing security by adding layers of verification. Explore the article to learn how to strengthen your authentication processes effectively.
Table of Comparison
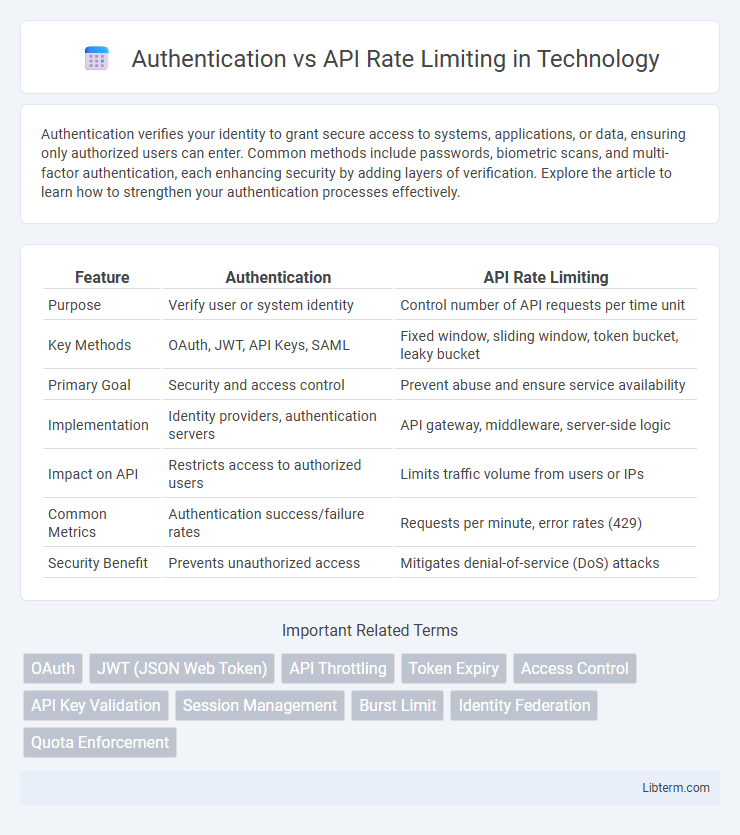
| Feature | Authentication | API Rate Limiting |
|---|---|---|
| Purpose | Verify user or system identity | Control number of API requests per time unit |
| Key Methods | OAuth, JWT, API Keys, SAML | Fixed window, sliding window, token bucket, leaky bucket |
| Primary Goal | Security and access control | Prevent abuse and ensure service availability |
| Implementation | Identity providers, authentication servers | API gateway, middleware, server-side logic |
| Impact on API | Restricts access to authorized users | Limits traffic volume from users or IPs |
| Common Metrics | Authentication success/failure rates | Requests per minute, error rates (429) |
| Security Benefit | Prevents unauthorized access | Mitigates denial-of-service (DoS) attacks |
Introduction to Authentication and API Rate Limiting
Authentication verifies the identity of users or systems accessing an API, ensuring secure and authorized interactions. API rate limiting controls the number of requests a client can make within a time frame to prevent abuse and maintain service stability. Both mechanisms are essential for protecting API resources and ensuring fair usage.
Understanding API Authentication: Purpose and Methods
API authentication verifies the identity of users or applications to protect sensitive data and enforce access control. Common authentication methods include API keys, OAuth tokens, JWT (JSON Web Tokens), and Basic Authentication, each providing varying levels of security and ease of use. Effective authentication ensures that only authorized clients can interact with the API, preventing unauthorized access and potential abuse.
What is API Rate Limiting?
API Rate Limimiting controls the number of API requests a client can make within a specific time frame to prevent abuse and ensure fair usage. Unlike authentication, which verifies user identity and permissions, rate limiting manages traffic flow by capping request frequency per user or IP address. This mechanism protects APIs from overloading, reduces server strain, and maintains service availability for all users.
Key Differences: Authentication vs. Rate Limiting
Authentication verifies the identity of users or applications accessing an API, ensuring secure and authorized access through credentials like API keys, tokens, or OAuth. API rate limiting controls the number of requests an individual user or client can make within a defined time period to prevent abuse, reduce server overload, and maintain service quality. While authentication focuses on security and access control, rate limiting targets resource management and operational stability.
Why Authentication Matters in API Security
Authentication plays a critical role in API security by ensuring that only authorized users or systems can access sensitive data and functionalities. It establishes trust between the client and server, preventing unauthorized access and reducing the risk of data breaches or malicious activity. Unlike API rate limiting, which controls the volume of requests, authentication verifies identity, forming the first line of defense in protecting APIs from attacks such as credential theft and identity spoofing.
Importance of Implementing API Rate Limiting
Implementing API rate limiting is crucial for protecting APIs from abuse and ensuring fair resource allocation among users. It helps maintain API performance by preventing excessive or malicious requests that can lead to server overload and downtime. Rate limiting complements authentication by controlling the request volume, enhancing overall security and reliability of the API services.
Common Authentication Methods for APIs
Common authentication methods for APIs include API keys, OAuth 2.0, and JWT (JSON Web Tokens), each providing a secure way to verify user identity and control access. API keys are simple tokens passed with requests, while OAuth 2.0 offers delegated access with token expiration and refresh capabilities. JWTs enable stateless authentication by encoding user information and claims within signed tokens, enhancing scalability and security for API interactions.
Popular API Rate Limiting Strategies
Popular API rate limiting strategies include token bucket, fixed window, sliding window, and leaky bucket algorithms, each designed to control the number of API requests within a specified time frame to prevent abuse and ensure fair usage. Authentication ensures that only authorized users can access the API, while rate limiting manages the volume of requests from authenticated or unauthenticated users to maintain service stability. Combining robust authentication methods like OAuth 2.0 with adaptive rate limiting strategies enhances security and optimizes API performance under varying traffic conditions.
Authentication and Rate Limiting Best Practices
Authentication ensures secure access by verifying user identities through methods like OAuth, JWT, or API keys, establishing trusted communication between clients and servers. Rate limiting protects APIs from abuse and ensures service availability by restricting the number of requests per user, IP address, or API key within a specified time frame. Best practices involve combining strong authentication mechanisms with adaptive rate limiting policies, such as dynamic thresholds based on user roles and real-time traffic analysis, to enhance both security and performance.
Conclusion: Integrating Authentication and Rate Limiting for Secure APIs
Integrating authentication with API rate limiting creates a robust security framework that ensures only authorized users access the API while preventing abuse through excessive requests. Authentication verifies user identities, enabling rate limiting rules to be applied accurately based on user roles or subscription tiers. This combined approach enhances API performance, safeguards sensitive data, and maintains service availability by mitigating threats like brute force attacks and denial of service.
Authentication Infographic
 libterm.com
libterm.com