Bypassing restrictions or security measures requires a deep understanding of the system and potential vulnerabilities to ensure effective and safe navigation. It's essential to follow ethical guidelines and legal frameworks to avoid unintended consequences or violations. Explore the rest of this article to learn how you can responsibly approach bypass techniques and safeguard your digital activities.
Table of Comparison
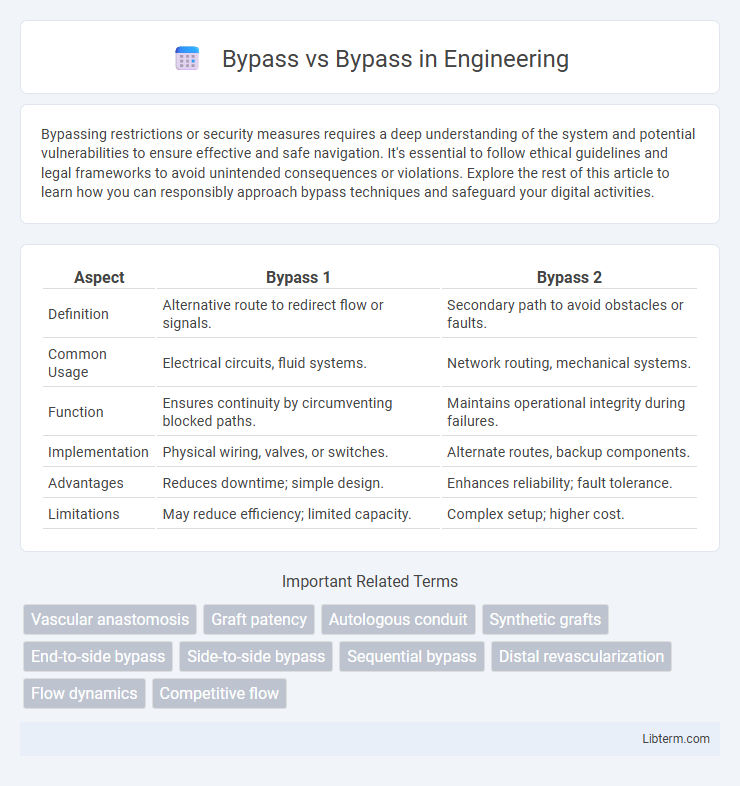
| Aspect | Bypass 1 | Bypass 2 |
|---|---|---|
| Definition | Alternative route to redirect flow or signals. | Secondary path to avoid obstacles or faults. |
| Common Usage | Electrical circuits, fluid systems. | Network routing, mechanical systems. |
| Function | Ensures continuity by circumventing blocked paths. | Maintains operational integrity during failures. |
| Implementation | Physical wiring, valves, or switches. | Alternate routes, backup components. |
| Advantages | Reduces downtime; simple design. | Enhances reliability; fault tolerance. |
| Limitations | May reduce efficiency; limited capacity. | Complex setup; higher cost. |
Understanding the Term "Bypass": Multiple Contexts
Bypass" refers to diverting something around an obstacle, commonly seen in medical procedures like coronary artery bypass surgery, where blood flow is redirected around blocked arteries. In technology, bypass may involve circumventing security measures or restrictions to access systems or data, emphasizing different operational goals. Understanding the context is crucial as the term "bypass" varies significantly between healthcare, telecommunications, and engineering applications.
Medical Bypass vs. Technological Bypass
Medical bypass involves surgical procedures like coronary artery bypass grafting (CABG) to restore blood flow around blocked arteries and improve cardiovascular function. Technological bypass refers to circumventing security systems or restrictions, such as firewall bypass or software bypass techniques, to access protected digital resources. Both types of bypass aim to restore or gain access by rerouting around obstacles, though one is rooted in healthcare and the other in cybersecurity.
How Bypass Procedures Differ in Medicine
Bypass procedures in medicine differ primarily based on the targeted organ and technique used; coronary artery bypass grafting (CABG) reroutes blood around blocked heart arteries using grafts from veins or arteries, while gastric bypass surgery alters the digestive system by creating a small stomach pouch connected directly to the small intestine for weight loss. CABG focuses on restoring adequate blood flow to the heart muscle to prevent ischemia and heart attacks, whereas gastric bypass aims to reduce calorie absorption and hunger through anatomical and hormonal changes. These procedures vary in complexity, recovery time, and indications, reflecting their distinct therapeutic goals in cardiovascular and bariatric medicine.
Bypass Methods in Digital Security
Bypass methods in digital security involve techniques used to circumvent security protocols, such as firewall rules, authentication mechanisms, or encryption measures. Common bypass techniques include exploiting software vulnerabilities, using proxy servers, or manipulating input validation to gain unauthorized access or evade detection. Understanding these methods is critical for strengthening cybersecurity frameworks and preventing unauthorized intrusion.
Advantages and Disadvantages: Medical Bypass
Medical bypass procedures, such as coronary artery bypass grafting (CABG), improve blood flow by redirecting blood around blocked arteries, reducing symptoms like chest pain and decreasing the risk of heart attacks. Advantages include long-term symptom relief, improved quality of life, and increased survival rates for patients with severe coronary artery disease. Disadvantages involve risks like infection, bleeding, stroke, longer recovery times, and potential complications from anesthesia or graft failure.
Risks and Benefits: Digital Bypass Techniques
Digital bypass techniques in medical device security offer significant benefits such as enhanced testing capabilities and improved access control, reducing the risk of device malfunction or unauthorized use. However, risks include potential vulnerabilities to cyberattacks and the possibility of compromising patient data integrity or device functionality. Careful implementation with robust encryption and authentication protocols can optimize safety while leveraging the advantages of digital bypass methods.
Legal Perspectives on Bypass Actions
Bypass actions in legal contexts refer to unauthorized attempts to circumvent established procedures or restrictions, often scrutinized under regulatory compliance and intellectual property laws. Courts assess bypass cases by evaluating intent, harm caused, and adherence to contractual or statutory obligations, with liability frequently hinging on whether the bypass undermines legal protections or causes unfair competitive advantage. Legal consequences may include injunctions, damages, or criminal penalties, emphasizing the importance of lawful conduct in bypass scenarios to uphold jurisdictional integrity and protect stakeholder interests.
Bypass vs. Bypass: Ethical Considerations
Bypass vs. Bypass scenarios raise significant ethical considerations surrounding patient autonomy, informed consent, and resource allocation. Healthcare professionals must weigh the potential benefits and risks of each bypass option, ensuring decisions align with ethical principles of beneficence and non-maleficence. Transparent communication and patient-centered care are crucial in navigating the moral complexities inherent in bypass treatment decisions.
Choosing the Right Bypass Approach
Choosing the right bypass approach depends on factors such as the patient's overall health, the specific location of the blockage, and the intended outcome of the procedure. Coronary artery bypass grafting (CABG) is commonly selected for severe coronary artery disease, while extra-anatomic bypasses are preferred in complex vascular cases involving peripheral arteries. Careful evaluation of anatomical considerations and surgical risks ensures optimal bypass technique selection for improved patient prognosis.
The Future of Bypass Solutions in Various Fields
The future of bypass solutions in medicine and technology emphasizes minimally invasive techniques and advanced biomaterials to improve patient outcomes and device efficiency. Innovations like robotic-assisted surgery and AI-driven network bypass algorithms are revolutionizing cardiovascular treatments and data traffic management, respectively. Ongoing research aims to enhance durability, reduce complications, and optimize real-time response across diverse applications.
Bypass Infographic
 libterm.com
libterm.com